metarget v0.9.1 releases: framework providing automatic constructions of vulnerable infrastructures
metarget
Metarget = meta- + target, a framework providing automatic constructions of vulnerable infrastructures, used to deploy simple or complicated vulnerable cloud-native targets swiftly and automatically.
1.1 Why Metarget?
During security researches, we might find that the deployment of a vulnerable environment often takes much time, while the time spent on testing PoC or ExP is comparatively short. In the field of cloud-native security, thanks to the complexity of cloud-native systems, this issue is more terrible.
There are already some excellent security projects like Vulhub, VulApps in the open-source community, which pack vulnerable scenes into container images, so that researchers could utilize them and deploy scenes quickly.
However, these projects mainly focus on vulnerabilities in applications. What if we need to study the vulnerabilities in the infrastructures like Docker, Kubernetes, and even Linux kernel?
Hence, we develop Metarget and hope to solve the deployment issue above to some extent. Furthermore, we also expect that Metarget could help to construct multilayer vulnerable cloud-native scenes automatically.
1.2 Install Vulnerability!
In this project, we come up with concepts like installing vulnerabilities and installing vulnerable scenes. Why not install vulnerabilities just like installing software? We can do that because our goals are security research and offensive security.
To be exact, we expect that:
- metarget cnv install cve-2019-5736 will install Docker with CVE-2019-5736 onto the server.
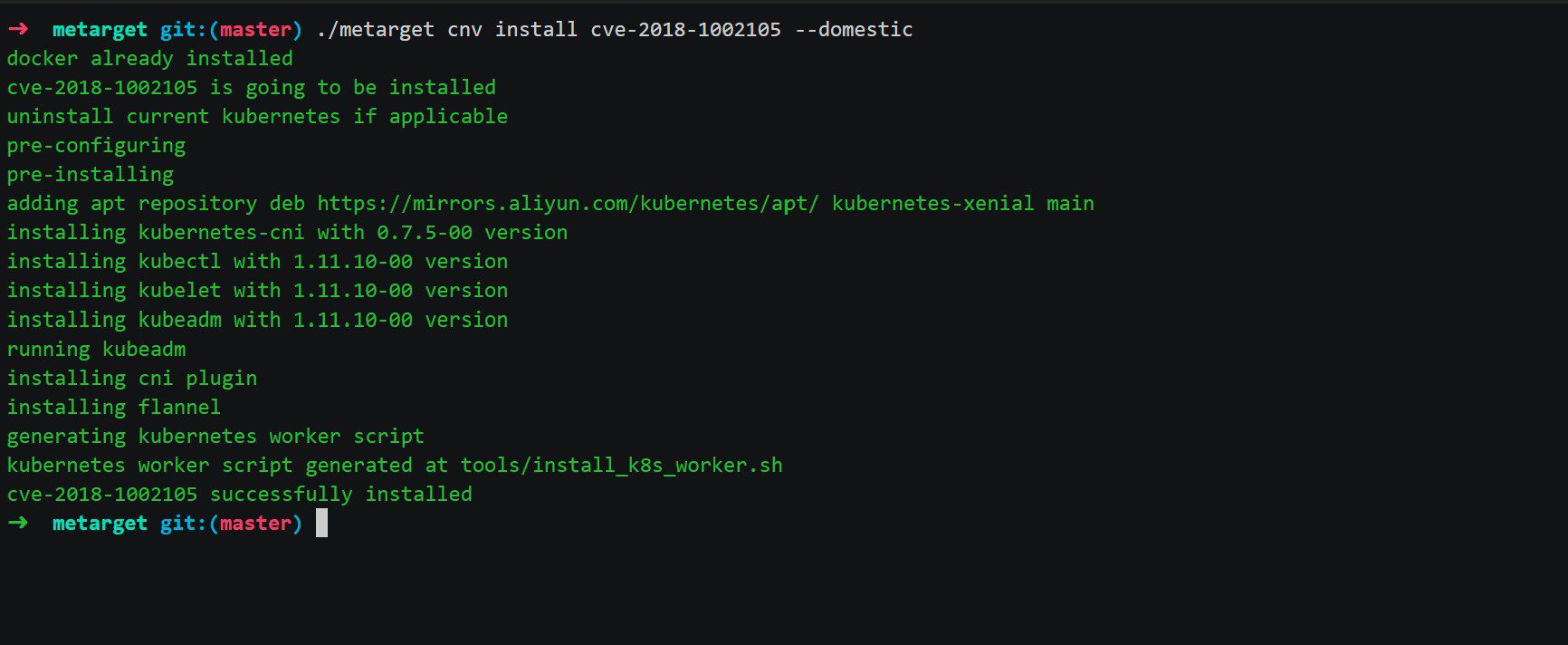
- metarget cnv install cve-2018-1002105 will install Kubernetes with CVE-2018-1002105 onto the server.
- metarget cnv install kata-escape-2020 will install Kata-containers with CVE-2020-2023/2025/2026 onto the server.
- metarget cnv install cve-2016-5195 will install a kernel with DirtyCoW into the server.
It’s cool, right? No more steps. No RTFM. Execute one command and enjoy your coffee.
Furthermore, we expect that:
- with Metarget’s help, ethical hackers are able to deploy simple or complicated cloud-native targets swiftly and learn by hacking cloud-native environments.
- metarget appv install dvwa will install a DVWA target onto our vulnerable infrastructure.
- metarget appv install thinkphp-5-0-23-rce –external will install a ThinkPHP RCE vulnerability with NodePort service onto our vulnerable infrastructure.
You can just run 5 commands below after installing a new Ubuntu and obtain a multi-layer vulnerable scene:
./metarget cnv install cve-2016-5195 # container escape with dirtyCoW
./metarget cnv install cve-2019-5736 # container escape with docker
./metarget cnv install cve-2018-1002105 # kubernetes single-node cluster with cve-2018-1002105
./metarget cnv install privileged-container # deploy a privileged container
./metarget appv install dvwa --external # deploy dvwa target
RCE, container escape, lateral movement, persistence, they are yours now.
More awesome functions are coming! Stay tuned 🙂
Note:
Thie project aims to provide vulnerable scenes for security research. The security of scenes generated is not guaranteed. It is NOT recommended to deploy components or scenes with Metarget on the Internet.
Changelog v0.9.1
- adopt semantic versioning
- some
cnvs andappvs added
Install & Use
Copyright (c) 2020 brant-ruan




