Following the successful resolution, Microsoft’s security division today unveiled the intricate details of the CVE-2023-32369 vulnerability, dubbed Migraine: a formidable security flaw nestled within macOS’s System Integrity Protection (SIP), enabling evasion of Apple’s integrity safeguards with the potential objective of installing rootkits.
System Integrity Protection (SIP)—also known as “rootless”—was first introduced by Apple in macOS Yosemite. SIP essentially locks down the system from root by leveraging the Apple sandbox to protect the entire platform, conceptually similar to how SELinux protects Linux systems. One of the most dominant features of SIP is the filesystem restriction capability, which protects entire files and directories from being overridden. The files and directories that are protected by SIP by default are common ones that are related to the system’s integrity.
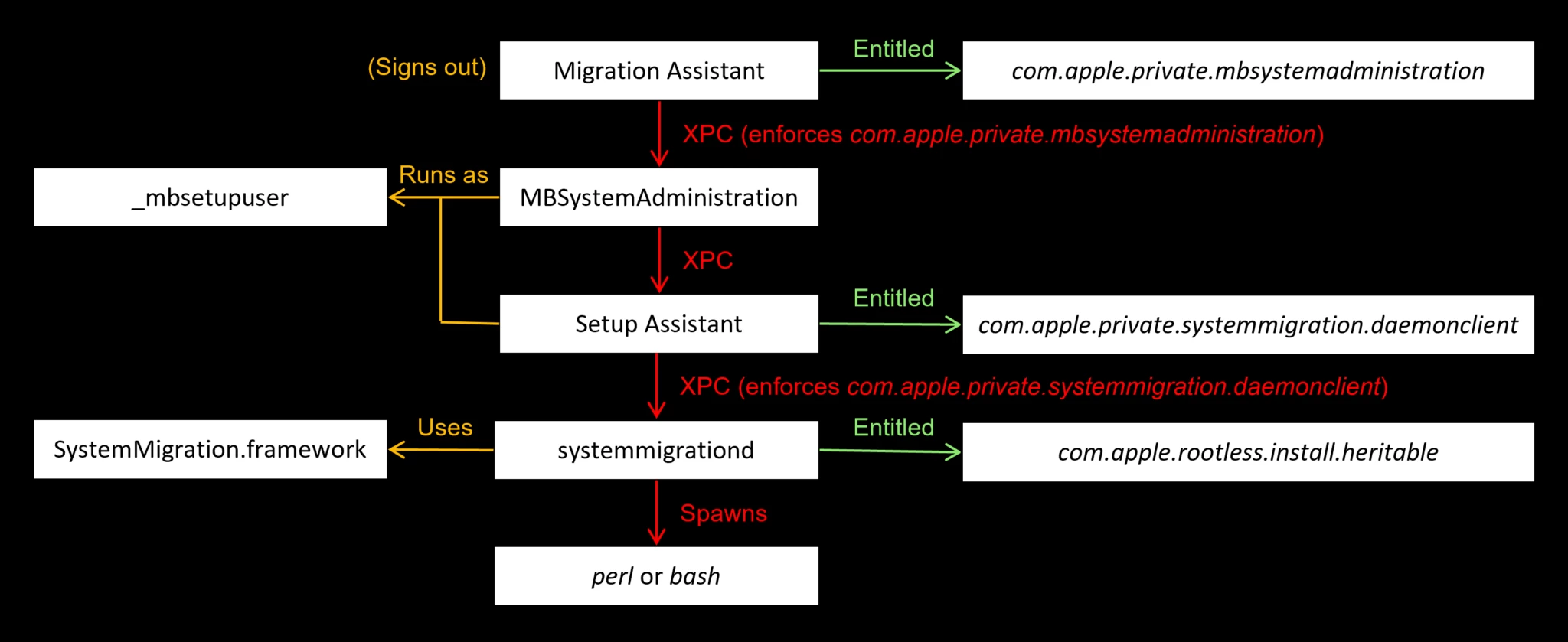
The underlying security premise of SIP allows only Apple-signed processes or those possessing unique permissions to alter protected components. For instance, the Apple software update program is granted this exclusive modification privilege. Concurrently, without rebooting the system and accessing macOS Recovery, SIP cannot be disabled, indicating the requirement of physical access to the target device to initiate an attack.

However, Microsoft’s security researchers uncovered that attackers with root privileges could exploit macOS Migration Assistant to circumvent SIP. It was proven that attackers with root access could utilize AppleScript to automate the migration process, adding it to an exclusion list to enable launch, negating the necessity of physically accessing the device, and rebooting into Recovery mode.
Ultimately, via the flaw, attackers could bypass SIP and install rootkits to obscure malicious processes and files. Even if anomalies are detected by users or security software, it is impossible to eradicate the rootkits.
Nevertheless, for assailants, obtaining root privileges poses significant hurdles, indicating that leveraging this vulnerability is far from effortless.
After Microsoft disclosed the CVE-2023-32369 flaw to Apple, the tech giant has since released patches in security updates for macOS Ventura 13.4, macOS Monterey 12.6.6, and macOS Big Sur 11.7.7 on May 18. The majority of users are presumed to have updated to these unaffected versions, prompting Microsoft’s public disclosure of the vulnerability.