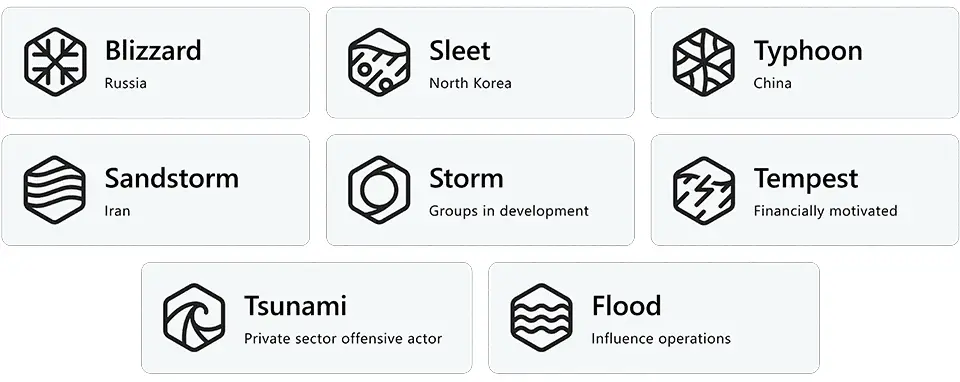
Eight threat actor groups that Microsoft tracks represented in the new naming taxonomy
Microsoft has announced that it will henceforth employ climate-related nomenclature to designate various types of hacking activities. Unclassified hacking behavior still under investigation will be dubbed “Storm,” while hacking activities supported by the Chinese government will be referred to as “Typhoon.” Iranian hacking activities will be called “Sandstorm,” and economically-motivated cyberattacks will be termed “Tempest.”
Microsoft’s classification system for hacking groups encompasses nation-state actors, financially motivated attacks, private sector offensive actors, influence operations, and groups still in development.

The newly announced climate-based naming system includes terms such as “Typhoon,” “Sandstorm,” “Rain,” “Sleet,” “Blizzard,” “Hail,” “Dust,” and “Cyclone” to describe hacking activities originating from China, Iran, Lebanon, North Korea, Russia, South Korea, Turkey, and Vietnam, respectively.
As for distinctions based on attack behavior, designations like “Tempest,” “Tsunami,” and “Flood” depict economically driven, private sector, and influence operation-targeted hacking activities, respectively. Other unclassified hacking attacks will be labeled as “Storm.”
While Microsoft believes that this new naming convention will help quickly identify the origins and objectives of specific hacking activities, some argue that the system could cause confusion with existing cybersecurity industry naming conventions, potentially leading to difficulties in understanding and comprehension.