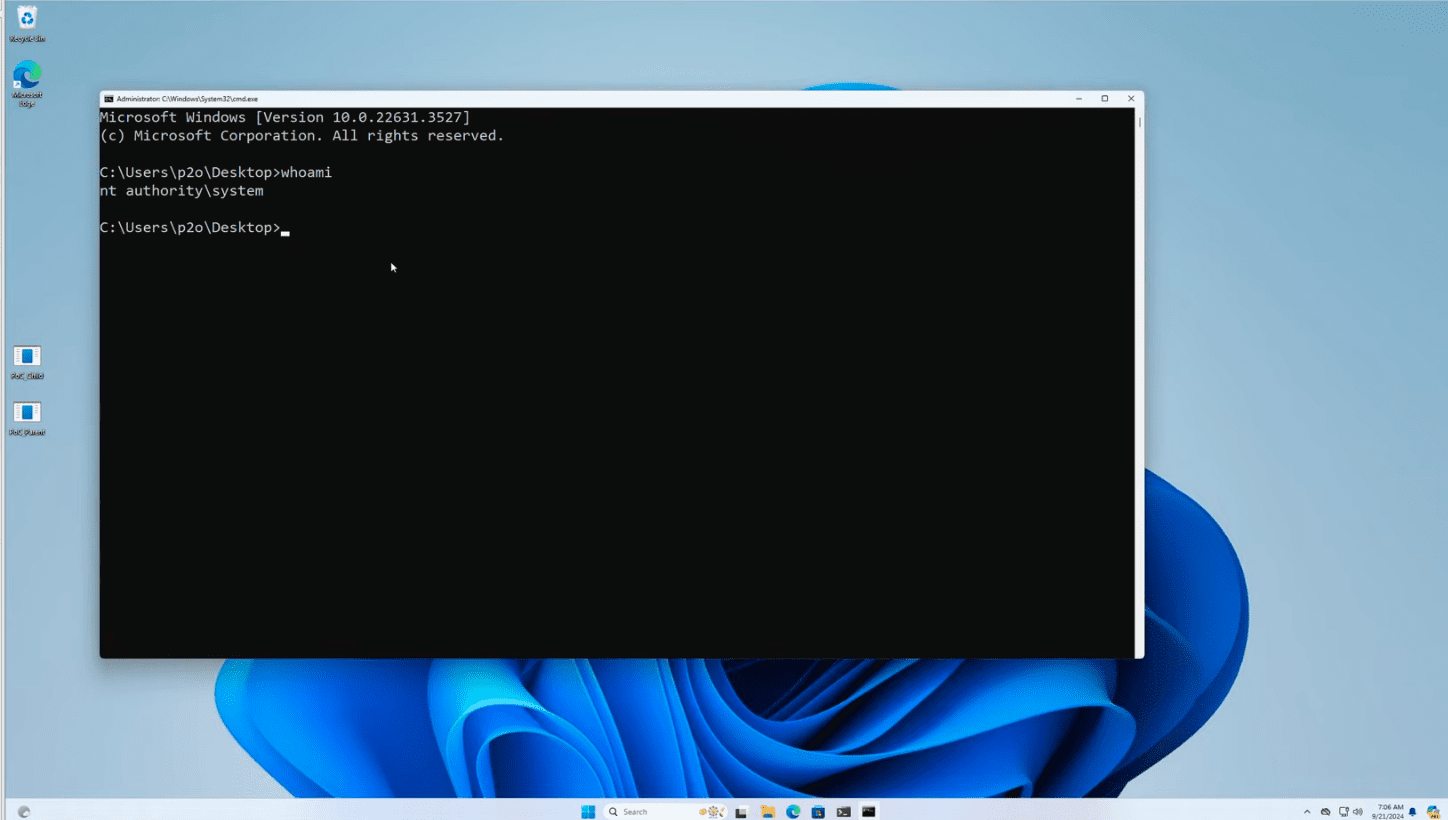
Security researcher Angelboy (@scwuaptx) with DEVCORE has identified a privilege escalation vulnerability in Microsoft’s Kernel Streaming service. The vulnerability, tracked as CVE-2024-30090 and assigned a CVSS score of 7.0, could allow an attacker to gain SYSTEM privileges on a vulnerable Windows system.
Kernel Streaming is a framework used by Windows to efficiently handle data streams from various devices such as webcams, microphones, and other audio devices. “On Windows systems, when we open the webcam, enable sound, and activate audio devices such as microphones, the system needs to write or read related data such as your voice and captured images from your devices into RAM,” Angelboy explains. “It is essential to read data into your computer more efficiently during this process. Microsoft provides a framework called Kernel Streaming to handle these data, which primarily operates in kernel mode.”
The vulnerability arises from a race condition that can be exploited to manipulate privilege checks within the Kernel Streaming service. “An attacker who successfully exploited this vulnerability could gain SYSTEM privileges,” Microsoft confirmed in its security advisory. “Successful exploitation of this vulnerability requires an attacker to win a race condition.”
Specifically, the vulnerability arises when nt!SeDebugPrivilege is changed, enabling a non-administrative user to gain PROCESS_ALL_ACCESS to high-privilege processes. This attack vector essentially bypasses the need for SeDebugPrivilege, which typically requires administrative control.
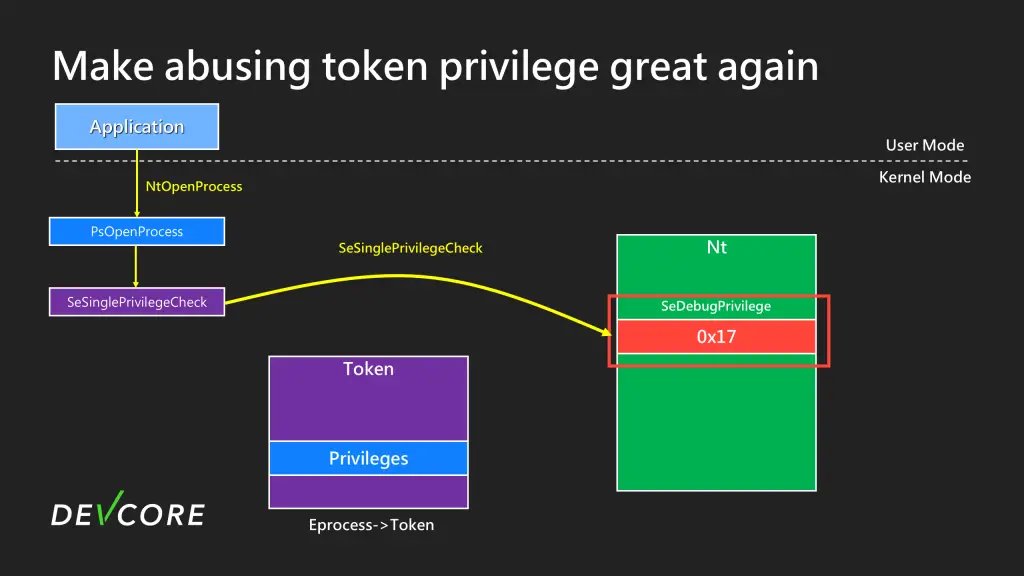
The exploit manipulates how Windows checks process privileges. Typically, users with SeChangeNotifyPrivilege—a common privilege—are allowed limited access to system resources. However, by exploiting this flaw, attackers can trick the system into believing they have SeDebugPrivilege, which grants higher-level access.
Angelboy’s analysis delves into the technical details of the vulnerability, explaining how an attacker can leverage the race condition to modify specific privilege values and ultimately gain unauthorized access.
Following Angelboy’s analysis, security researcher Dor00tkit published a proof-of-concept (PoC) exploit code for CVE-2024-30090 on GitHub. The PoC demonstrates how attackers can reliably exploit this flaw on Windows 11 23H2 systems, utilizing a proxying to kernel technique to achieve privilege escalation.
Fortunately, Microsoft patched this flaw during their June 2024 Patch Tuesday update. Users are strongly encouraged to apply this update immediately, as leaving systems unpatched exposes them to potential attacks leveraging this exploit.
Related Posts:
- PoC Exploit Release for Windows Kernel-Mode Driver Elevation of Privilege Flaw (CVE-2024-35250)
- GitHub Security Alerts has detected over 4 million vulnerabilities