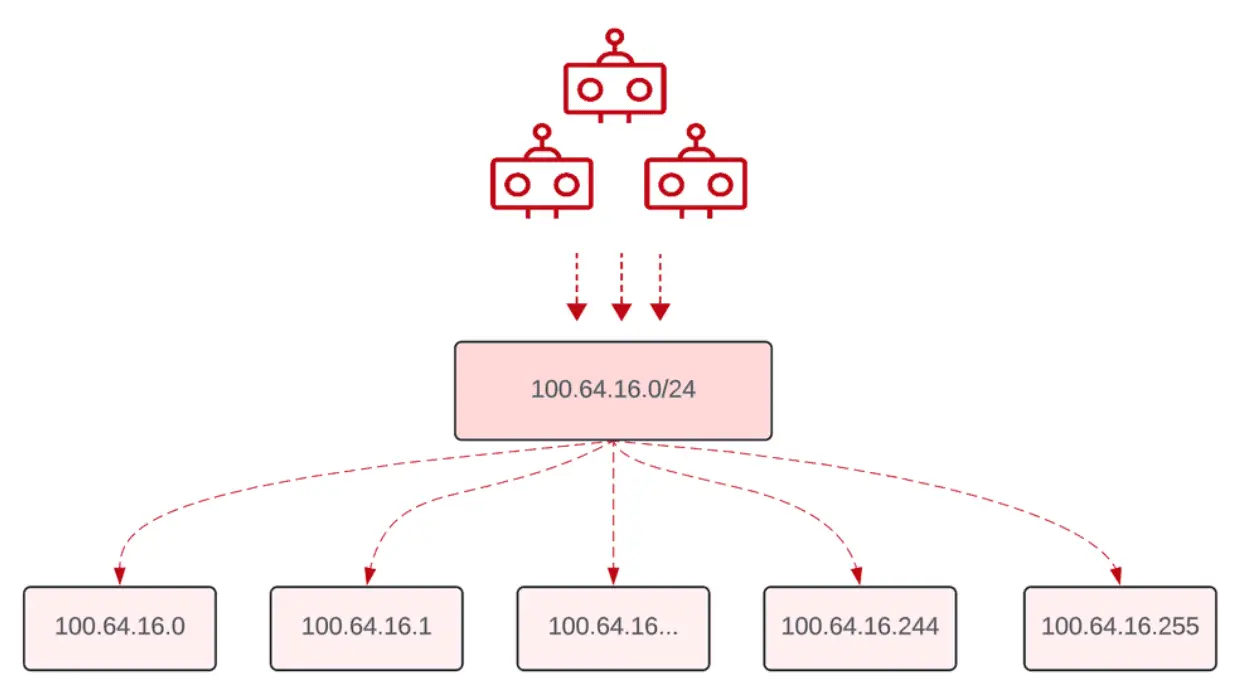
Carpet Bomb attacks aim to flood traffic to all IPs within a subnet on a victim network, with the goal to bypass per destination attack detection | Image: Global Secure Layer
Global Secure Layer (GSL), a prominent cybersecurity firm, recently mitigated the largest packet rate DDoS attack ever recorded on its platform. The assault targeted a Minecraft gaming customer, peaking at a staggering 3.15 billion packets per second (Gpps). This unprecedented attack size surpasses previous records by a factor of 3.2 to 3.5, underscoring the escalating threat posed by DDoS attacks.
The attack began with a preliminary strike on August 24th, targeting a single prefix of the victim’s network. This initial wave, peaking at 1.7 Gpps, lasted only 20 seconds and had minimal impact, thanks to the preemptive security configurations on Creatia, GSL’s DDoS management platform. This brief attack served as a reconnaissance mission, allowing the attackers to probe the network for weaknesses before launching a full-scale assault.
Frustrated by the initial failure, the attackers returned with a vengeance the following day, unleashing a massive back-to-back campaign that carpet-bombed all advertised prefixes of the victim’s network. The peak of this attack reached an astonishing 3.15 Gpps, overwhelming private network interfaces (PNIs) between Korea Telecom and major tier 1 providers. Although the attack temporarily impacted some prefixes, particularly in New York, GSL’s swift reconfiguration of security settings prevented any long-term damage.
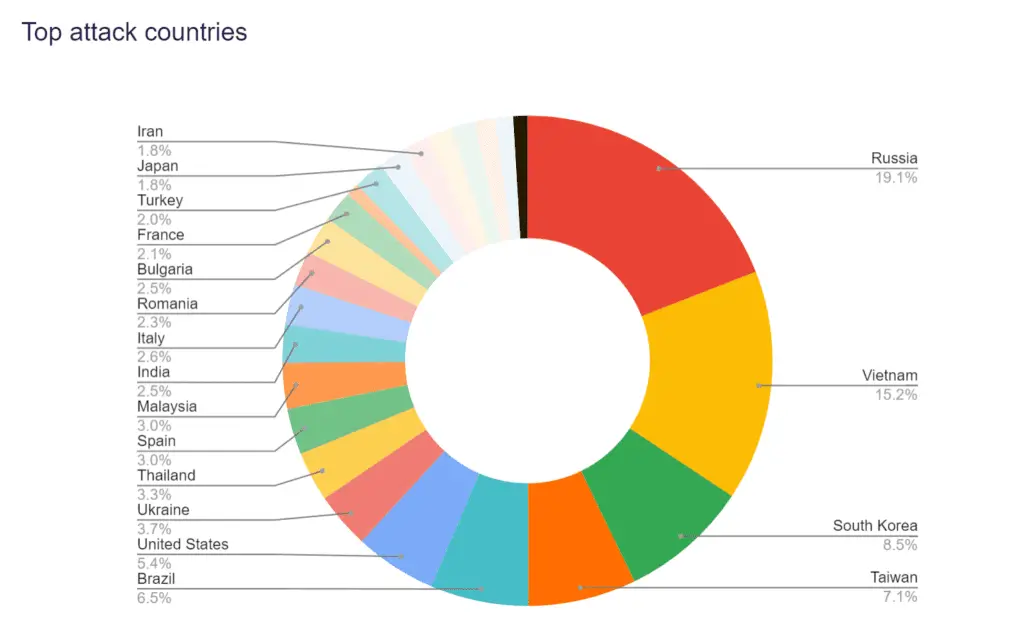
GSL’s analysis revealed that the attackers employed two distinct botnets during the assault. The first botnet, responsible for the record-breaking packet rate attack, saw Russia, Vietnam, and Korea as the primary sources. This botnet’s composition was dominated by devices vulnerable to CVE-2023-2231, an authentication manipulation exploit. GSL identified over 42,000 sources participating in this attack, with a significant number traced back to Korea Telecom’s network.
In contrast, the second botnet focused on volumetric attacks, peaking at 1.516 terabits per second (Tbps). This botnet’s origins were more geographically diverse, with Russia, Ukraine, and Brazil leading the charge. The devices involved in these attacks included DrayTek Vigor routers and Hikvision IP cameras, showcasing the attackers’ ability to leverage widely available commercial hardware for their campaign.
GSL’s Goliath platform, deployed across 33 global points of presence, played a crucial role in mitigating the attacks. Despite the sheer scale and complexity of the assault, Goliath’s robust infrastructure and Creatia’s intelligent security configurations ensured that the impact on the customer was minimal. The attackers’ repeated attempts to breach the network were thwarted, with mitigation times consistently under 100 milliseconds.
Related Posts:
- 50,000 Minecraft players are infected with a malicious program
- Kaspersky Lab: Minecraft is still a big malware target
- AI Powers a Phishing Frenzy – Zscaler Report Warns of Unprecedented Threat Wave
- Linux Leaps to Record 4.44% Market Share: Open-Source OS Hits All-Time High in July