Mirage: powerful and modular framework dedicated to the security analysis of wireless communications
Mirage is a powerful and modular framework dedicated to the security analysis of wireless communications. It actually provides :
- a lightweight and hackable Bluetooth Low Energy protocol stack
- multiple highly customizable offensive modules (e.g. Man-in-the-Middle, sniffing, jamming, hijacking, cloning …)
- mutiple modules dedicated to information gathering (e.g. ATT/GATT dumping, scanning …)
- a chaining operator allowing to easily combine attack modules in order to build complex attack workflows
- supports of multiple Bluetooth Low Energy devices, such as HCI devices, BTLEJack, Nordic and Ubertooth sniffers
- supports of tools for monitoring HCI communications, using ADB or Hcidump
- an user-friendly development environment allowing to easily write new modules or customize existing ones
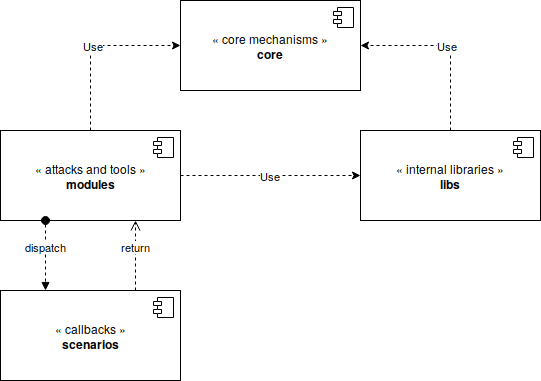
Mirage is divided into four main components :
- The core component (“core”) : this component includes the core mechanisms of the framework. First, it allows to load, configure and execute the modules. It provides some mechanisms allowing to manipulate background tasks, signals, parameters and configuration files. It provides an unique entrypoint.
- The internal libraries (“libs”) : this component is in charge of implementing the Bluetooth Low Energy stack (
mirage.libs.ble). It also provides some display and logging mechanisms (mirage.libs.io) and some utilities and helpers functions (e.g. background tasks manipulation, time management, …). - The attacks and tools (“modules”) : these components, called modules, implement the different attack and tools provided by Mirage. They provide a specific attack or function (such as Man-in-the-Middle, sniffing …) and can be used independently or sequentially thanks to the chaining operator.
- The callbacks (“scenarios”) : some modules (such as Man-in-the-Middle) implements some complex behaviours and implements a standardised API allowing to easily customize their execution. The scenarios are specialised classes composed of bindings allowing to quickly customize a module’s execution.
Install && Use
© Copyright 2019, Romain Cayre





