The Insikt Group, a threat research group of network security company Recorded Future, brought us an update on the Mirai botnet in a blog post published on Thursday. In late January of this year, a variant of the Mirai botnet launched a series of DDoS attacks against financial companies.
Insikt Group stated that the botnet in the attack may be closely related to the variant of the Mirai botnet, IoTroop (also known as Reaper). So far, at least three European financial institutions have become victims of the attacks.
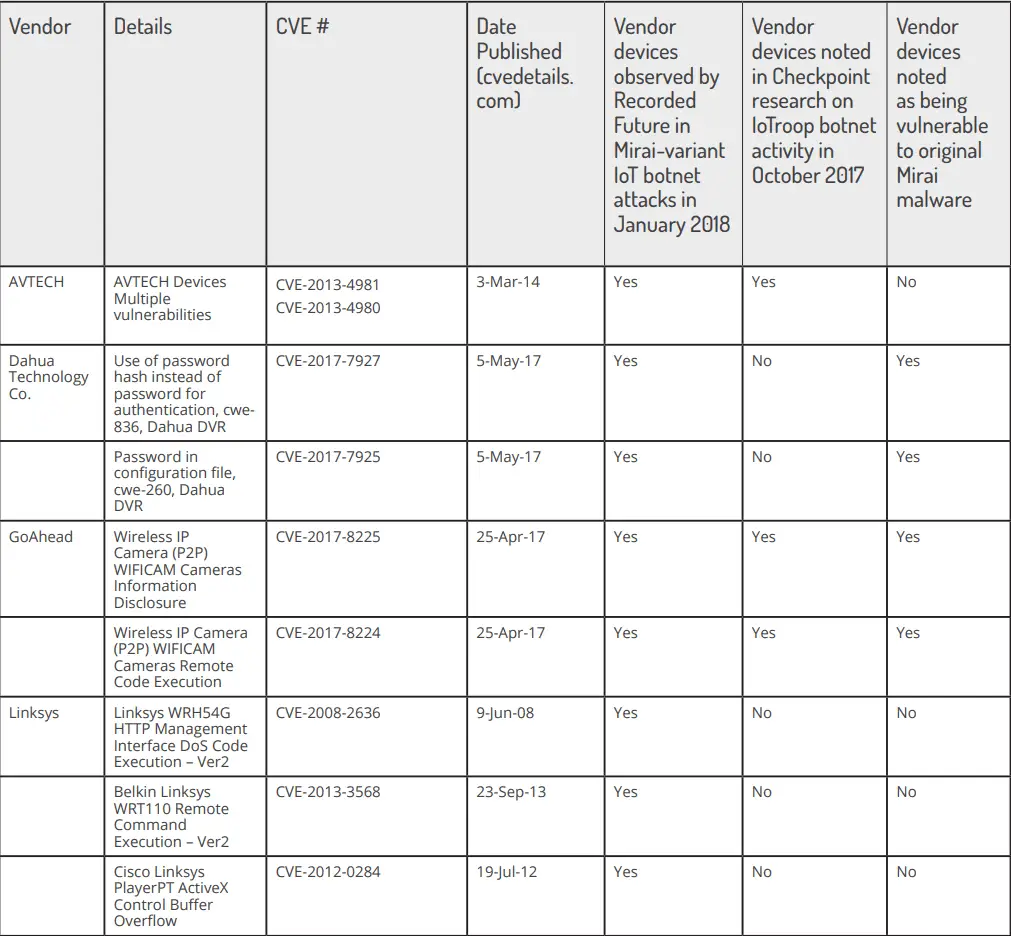
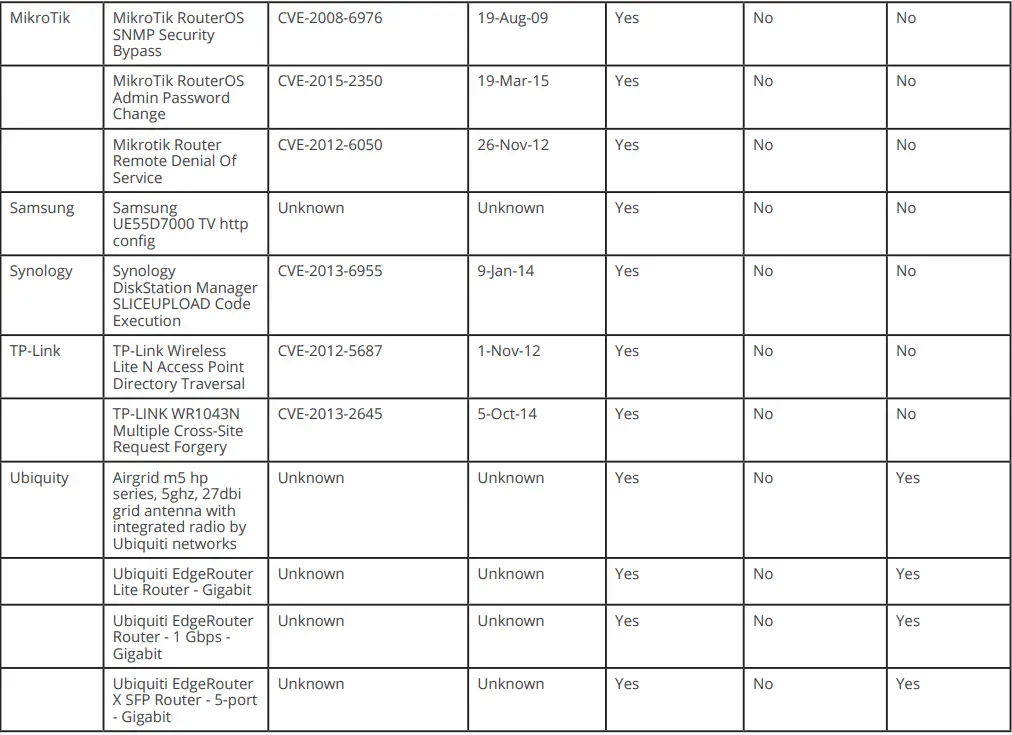
On October 29, 2017, Israeli cybersecurity company Check Point stated in its published technical report that their security team has discovered a new type of botnet, codenamed IoTroop. It consists of a variety of infected IoT devices, such as routers and wireless webcams, most of which are manufactured by companies such as TP-Link, Avtech, MikroTik, Linksys, Synology, and GoAhead.
Check Point said that while malware used by IoTroop to spread botnets (also known as Reaper) uses some of Mirai’s code, it is a completely new type of malware and threats.
It is unique in that malware is built using flexible Lua engines and scripts, which means that it is not limited by the static pre-programmed attacks of the Mirai botnet. The code can be easily updated at any time, as long as the large-scale botnet is built, it can launch new and more destructive attacks.
IoTroop is more responsible than Mirai. In addition to weak credentials, it was also determined that it can use at least a dozen vulnerabilities and can add the most recently disclosed vulnerabilities at any time. Detailed list of vulnerabilities is as follows:
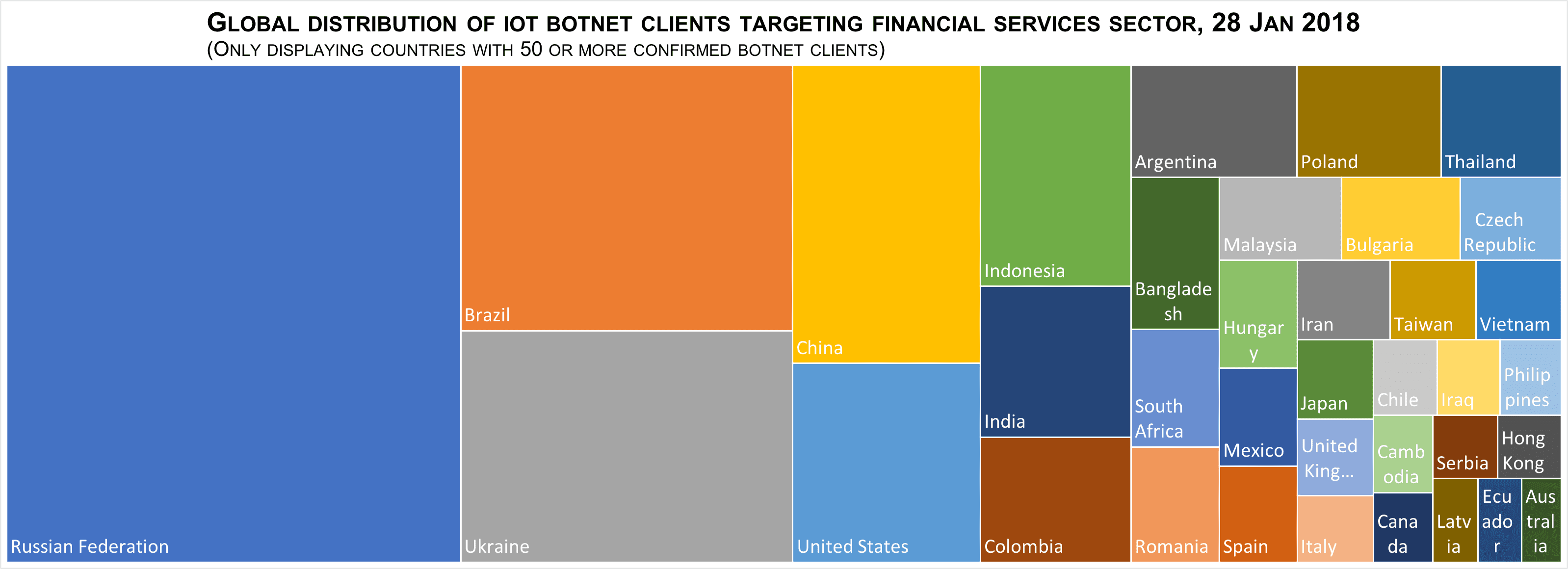
Insikt Group stated that the first attack took place around 18:30 on January 28, 2018. The botnet involved in the attack consists of at least 13,000 IoT devices, each with a unique IP address. In addition, this attack applied DNS amplification technology and attacked peak traffic to 30 Gbps.
The second attack was almost simultaneous with the first attack. Based on the use of the botnet infrastructure and the timing of attacks, the Insikt Group believes that the attack was initiated by the same Mirai variant botnet.
Further analysis confirmed the Insikt Group’s view that in this attack, the victim company’s IP address communicated with 26 unique IP addresses, and 19 of them participated in the attack on the first financial institution.
The third attack occurred around 21:00 on January 28, 2018, which was just a few hours after the first two incidents occurred.
According to the Insikt Group, 80% of the botnets are infected MikroTik routers, and the remaining 20% is made up of many other IoT devices, including vulnerable Apache and IIS web servers and produced by Ubiquity, Cisco, and ZyXEL. Routers.
These devices are distributed in 139 different countries and regions, mainly from Russia, Brazil, and Ukraine. However, this distribution does not reflect any specific content related to the configuration of the botnet, which may only reflect that MikroTik’s products are relatively popular in these countries.
The Insikt Group also stated that they have also found webcams, smart TVs, and digital video recorders (DVRs) on this 20% IoT device, mainly from MikroTik, GoAhead, Ubiquity, Linksys, and TP-Link. Produced by well-known manufacturers such as Dahua.
It is worth noting that while many vulnerable devices have been mentioned in previous reports, devices such as the Dahua CCTV DVR, Samsung UE55D7000 TV, and Contiki operating system seem to be discovered for the first time and are vulnerable to IoTroop botnets. s attack. This means that the IoTroop botnet is evolving and “evolved” by adding code that can exploit new IoT device vulnerabilities.
In February 2018, the Dutch police arrested an 18-year-old man for allegedly launching a DDoS attack against several Dutch companies, including the technology website Tweakers and Internet service provider Tweak. The Insikt Group suspects that this man may also be related to the recent DDoS attacks on three European financial institutions but has not yet been confirmed by the police.
According to reports by Dutch media Tweakers, the arrested man appeared to have been used only in the September 2017 attack by hiring a botnet. This means that even if the man is ultimately found to be related to the DDoS attacks in January this year, he may just rent the Mirai variant IoT botnet from the team behind IoTroop.
Therefore, Insikt Group stated that they are not clear who the developers behind the IoTroop botnet are, and it is not even possible to determine who performed the January attacks this year.
The Insikt Group stated that there is a common problem with the MikroTik devices that make up the IoTroop botnet, that is, TCP port 2000 is enabled. This is a reserved port for the MikroTik Bandwidth Test Server protocol and it turns out that this port seems to be a breakthrough for the IoTroop botnet infection device. Worse, for the new MikroTik device, this port is enabled by default.
In response, InsiktGroup has made a series of recommendations for companies that want to prevent their IoT devices from being part of any botnet network, including:
- Always replace default manufacturer passwords immediately upon use.
- Keep the firmware for devices current and up to date.
- For IP camera and similar systems that require remote access, invest in a VPN.
- Disable unnecessary services (e.g., Telnet) and close ports that are not required for the IoT device.
Source, Image: recordedfuture