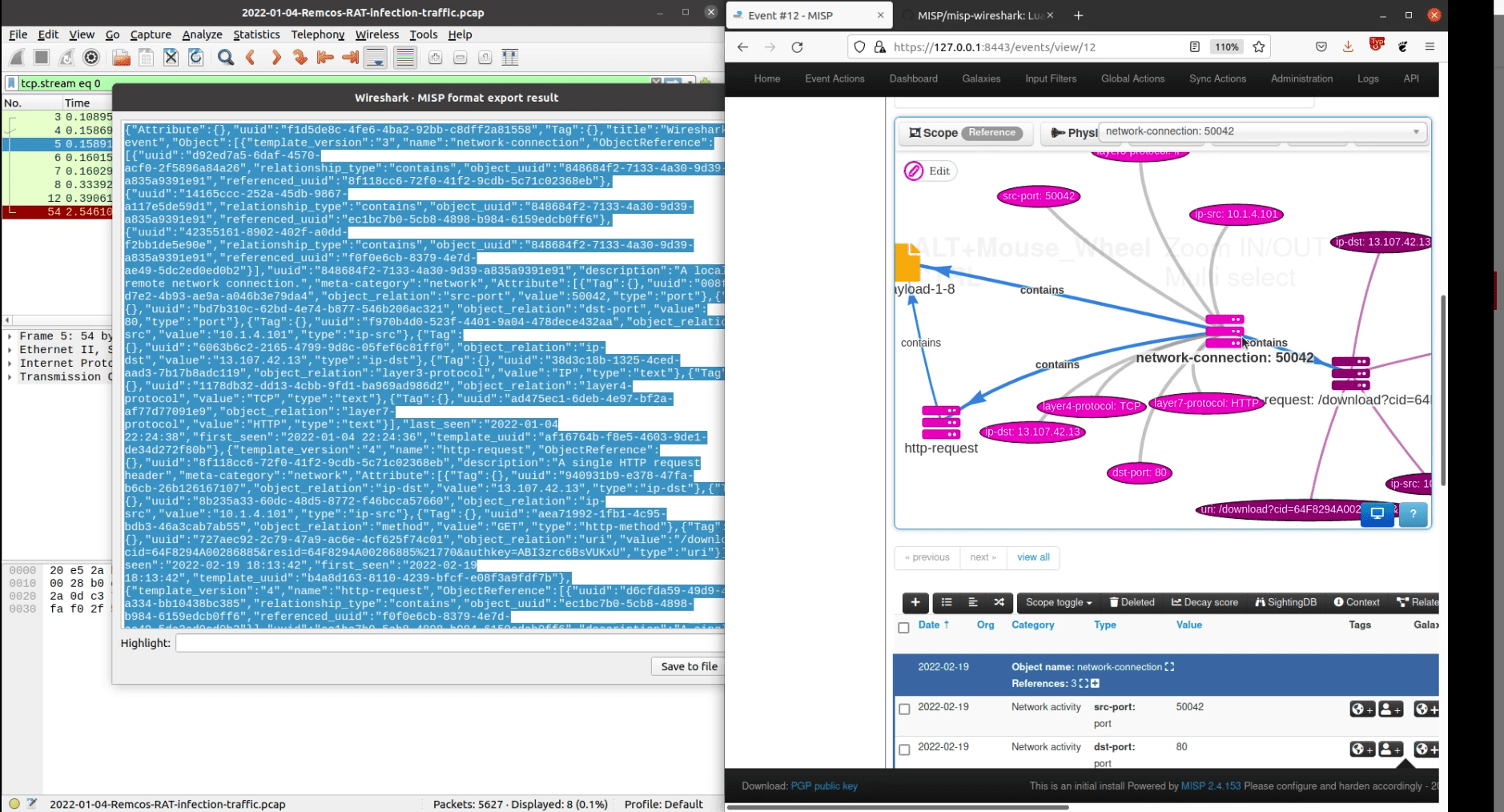
misp-wireshark
misp-wireshark is a Lua plugin intended to help analysts extract data from Wireshark and convert it into the MISP Core format.

Installation
On Linux, clone the repository in Wireshark’s plugin location folder
mkdir -p ~/.local/lib/wireshark/plugins
cd ~/.local/lib/wireshark/plugins
git clone https://github.com/MISP/misp-wireshark
cd misp-wireshark/
git submodule update –init –recursive
Usage
Wireshark
- Go to Tools located in Wireshark’s top bar and click on MISP: Export to MISP format
- Enter the export options to configure the behavior of the exporter
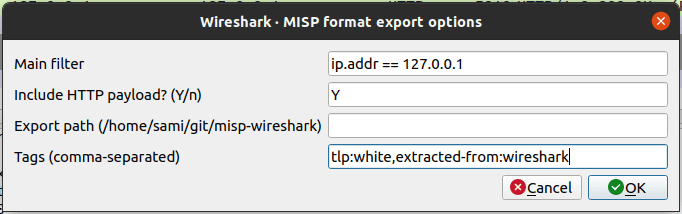
- Main filter: Fill this field to filter the exported data. Essentially, it will just be a copy/paste from the global filter in the interface. (This cannot be done automatically because of this)
- Include HTTP payload: Should the payloads sent via HTTP be included as a file in the output
- Export path: The location where the exported file should be saved when clicking on Save to file
- Tags: Optional tags can be attached to some MISP attributes.
- Copy or save in a file the data to be imported in MISP
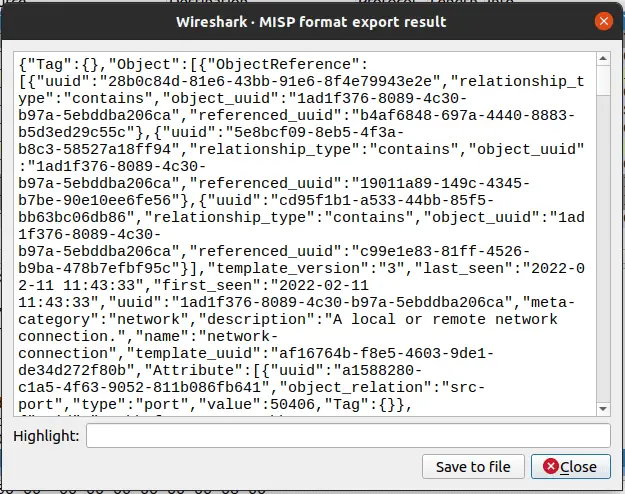
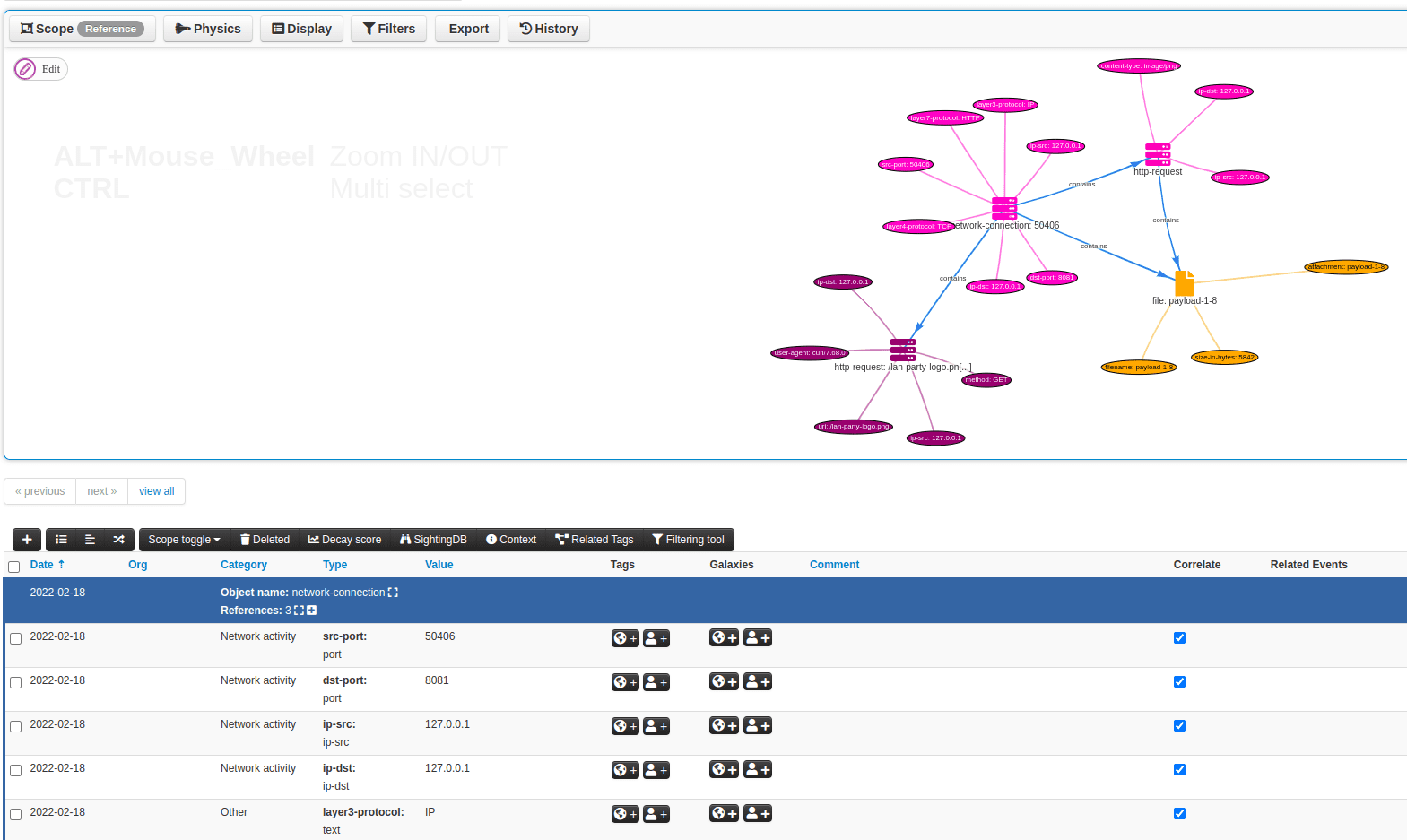
- Import in MISP
Tshark
Command-line options are the same parameters as in the user interface:
- filters: The filter expression to be applied
- include_payload: Should potential payload be also exported. Accept y or n
- export_path: The folder under which the json should be saved. If not supplied, default to stdout
- tags: Optional tags to be attached to some MISP attributes
Example
tshark \
-r ~/Downloads/capture.cap \
-X lua_script:/home/john/.local/lib/wireshark/plugins/misp-wireshark/misp-wireshark.lua \
-X lua_script1:filters=”ip.addr == 127.0.0.1″ \
-X lua_script1:include_payload=n \
-X lua_script1:tags=”tlp1,tlp2″ \
frame.number == 0
Note: As we did not supply an export path, the result is printed on stdout. However, to avoid mixing both the plugin output and tshark output, we provide a filter to tshark that will filter out every packet. However, this filter is not used by the plugin. Only the filter provided via -X lua_script1:filters is used.
Based on the example above, frame.number == 0 is only used to prevent the output of tshark while ip.addr == 127.0.0.1 is actually used by the plugin.
Source: https://github.com/MISP/