Mispadu Banking Trojan Expands Reach, Targeting Europe and Beyond
The Mispadu banking trojan, infamous for its attacks on Latin American countries, is aggressively broadening its targets. Morphisec Labs has identified a surge in Mispadu activity across Europe, marking a concerning shift in the threat’s reach.
No Sector is Safe
Mispadu’s latest attacks aren’t limited by industry. From automotive manufacturing giants to legal firms handling sensitive data, this trojan poses a risk to every organization that relies on online banking or sensitive login credentials. Mexico, the original hotbed of Mispadu activity, remains a major target, but the threat now extends far beyond its initial borders.
Stolen Credentials Fuel Further Attacks
With thousands of compromised accounts dating back to April 2023, Mispadu’s operators have amassed a vast arsenal to fuel their operations. Stolen login details are used to craft highly believable phishing emails, tailored to look like legitimate communications from banks or services that the victim recognizes. This personalized element makes these follow-up attacks particularly dangerous.
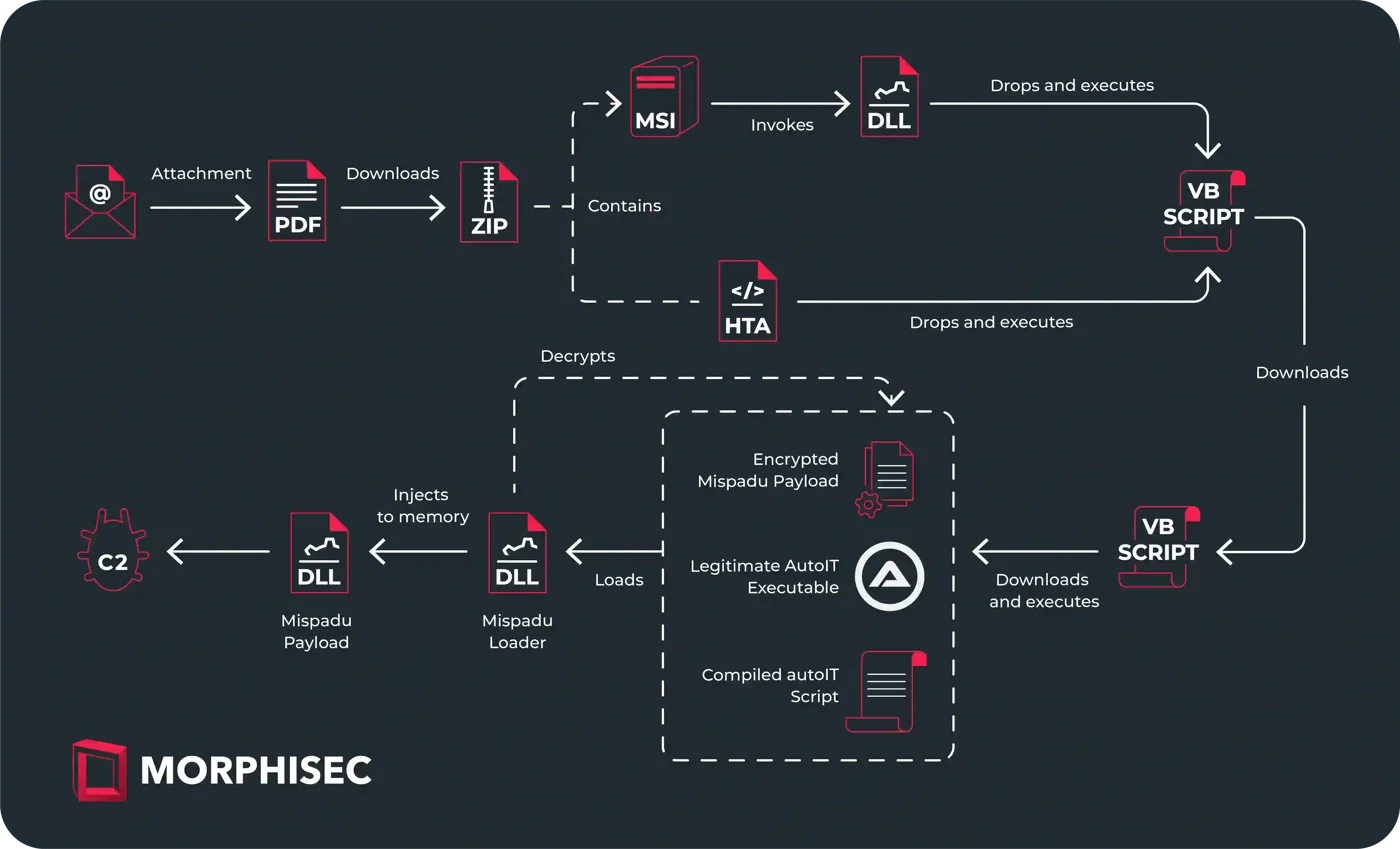
Infection Chain: New Tricks, Same Goal

Infection Chain | Image: Morphisec Labs
Mispadu employs a multi-staged attack chain, subtly refined from its previous incarnations. The initial stage involves the distribution of phishing emails, each containing a PDF that masquerades as an invoice. Victims enticed to “View Full Invoice” are led to download a ZIP file, initiating the trojan’s infiltration process.
The infection proceeds through a meticulously crafted VB script, leading to the download and execution of obfuscated files. These files, ingeniously disguised and employing anti-VM tactics, ensure the payload is delivered only to genuine targets, sidestepping detection mechanisms.
Upon successful evasion, Mispadu banking trojan deploys its final payload, leveraging NirSoft’s legitimate tools to harvest credentials from browsers and email clients. The trojan’s insidious nature is further exemplified by its ability to monitor over 200 financial and email services, awaiting the opportunity to pilfer sensitive information.
The sophistication of Mispadu’s campaign is evident in its dual C2 server strategy, one for payload delivery and the other for exfiltrating stolen credentials. With over 60K files found on the latter server, the extent of the breach is both substantial and alarming, underscoring the trojan’s relentless pursuit of data.
Proactive Defense is Essential
Staying ahead of Mispadu necessitates a comprehensive security strategy:
- Think Before You Click: Educate your users about the dangers of phishing emails. Scrutinize unexpected attachments and double-check the sender’s address before opening anything.
- Stay Updated: Ensure all operating systems, web browsers, and applications have the latest security patches. Outdated software is a welcome mat for malware.
- Advanced Threat Detection: Implement security solutions that use behavioral analysis and zero-trust principles to proactively block even highly evasive malware like Mispadu.





