mkYARA
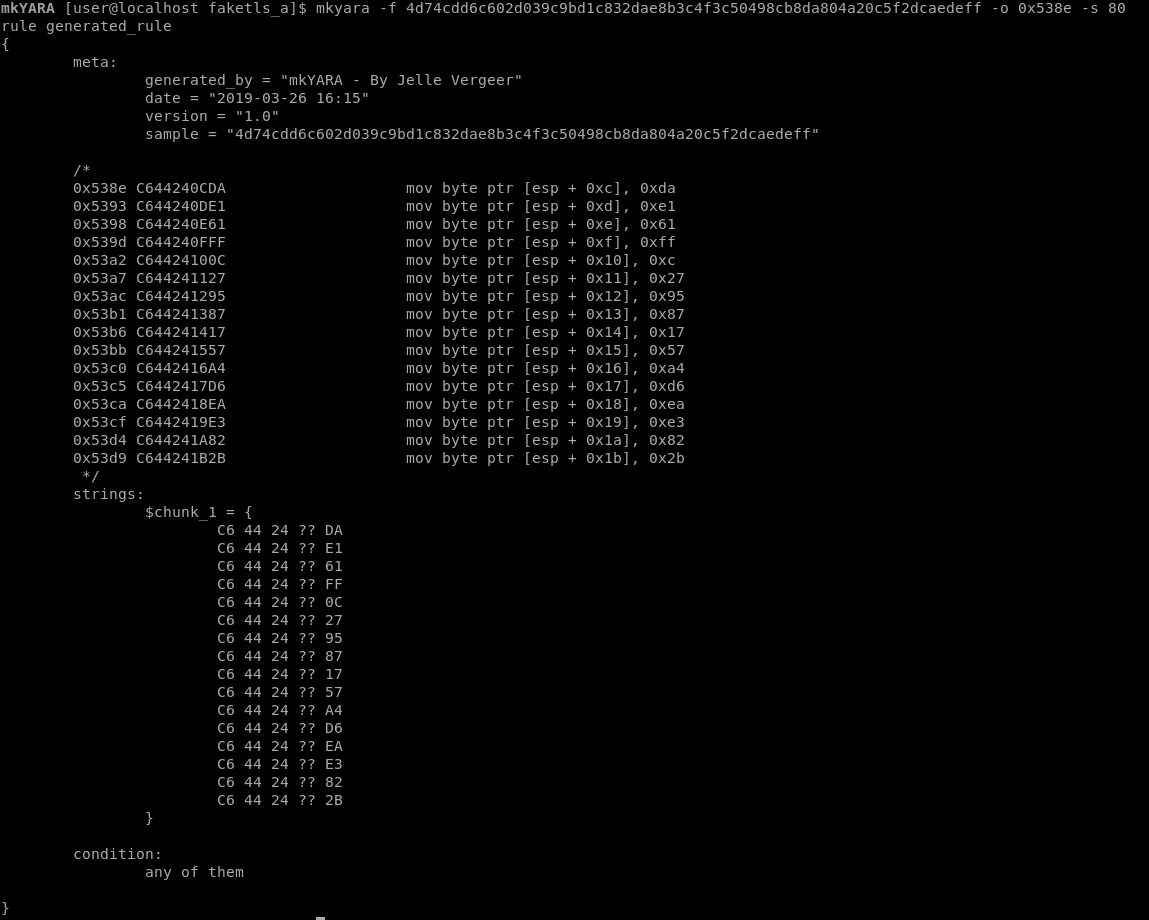
Writing YARA rules based on executable code within malware can be a tedious task. An analyst cannot simply copy and paste the raw executable code into a YARA rule, because this code contains variable values, such as memory addresses and offsets. The analyst has to disassemble the code and wildcard all the pieces in the code that can change between samples. mkYARA aims to automate this part of writing rules by generating executable code signatures that wildcard all these little pieces of executable code that are not static.
Installation
pip install mkyara
Usage
It comes with an IDA plugin to easily create YARA signatures by selecting a set of instructions and choosing one of the mkYARA -> Generate YARA rule options. Installation is as easy as installing the pip package and copying the mkyara_plugin.py to your IDA plugin directory.
Copyright (C) 2019
Source: https://github.com/fox-it/
