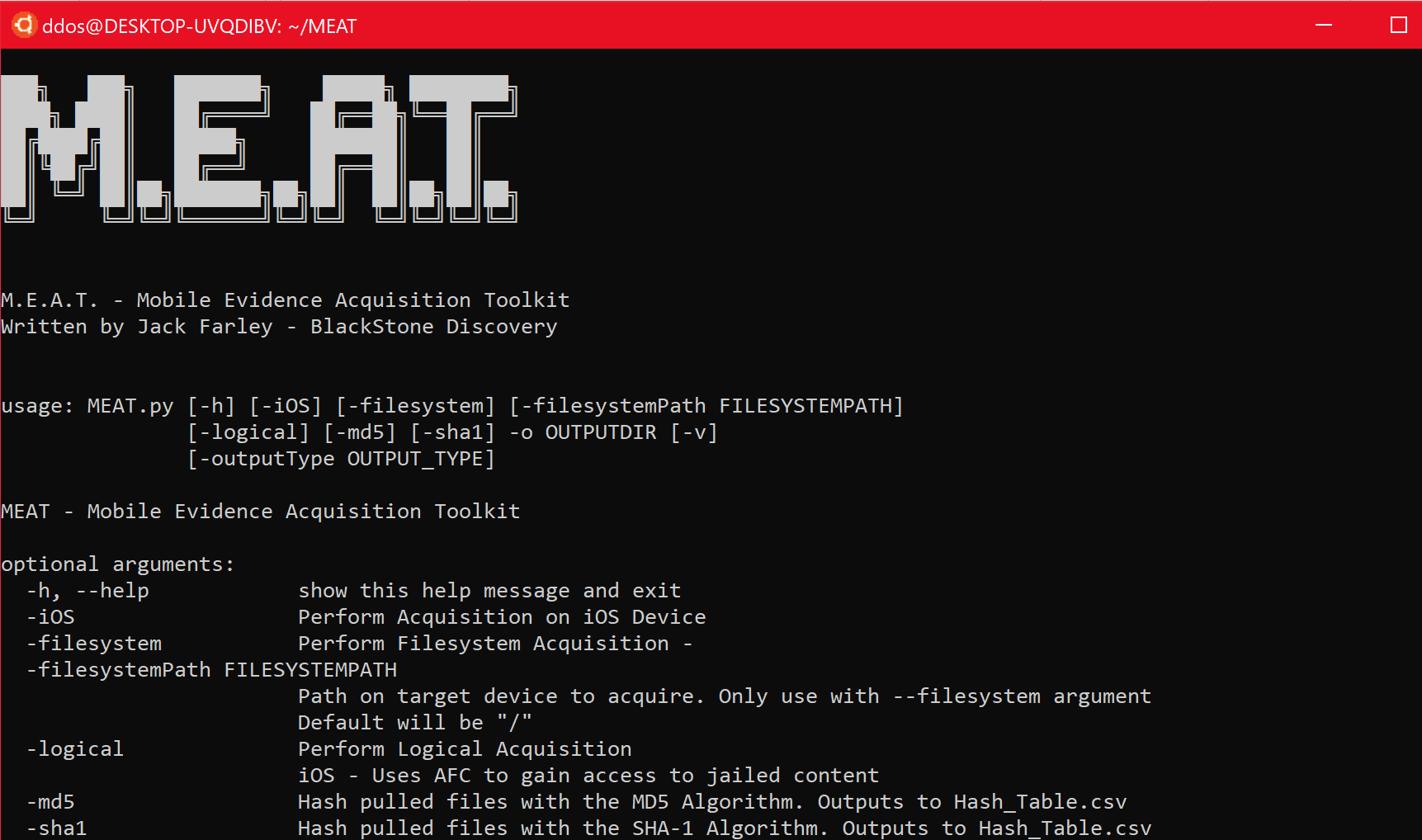
M.E.A.T. – Mobile Evidence Acquisition Toolkit
This toolkit aims to help forensicators perform different kinds of acquisitions on iOS devices (and Android in the future).
Devices tested on
iPhone X iOS 13.3 iPhone XS iOS 12.4
Types of Acquisitions Supported
iOS Devices
Logical
Using the logical acquisition flag on MEAT will instruct the tool to extract files and folders accessible through AFC on jailed devices. The specific folder that allows access is: \private\var\mobile\Media, which includes folders such as:
- AirFair
- Books
- DCIM
- Downloads
- general_storage
- iTunes_Control
- MediaAnalysis
- PhotoData
- Photos
- PublicStaging
- Purchases
- Recordings
Filesystem
iOS Device Prerequisites
- Jailbroken iOS Device
- AFC2 Installed via Cydia
Using the filesystem acquisition flag on MEAT will instruct the tool to start the AFC2 service and copy all files and folders back to the host machine.
This method requires the device to be jailbroken with the following package installed:
- Apple File Conduit 2
This method can also be changed by the user using the -filesystemPath flag to instruct MEAT to the only extract up a specified folder, useful if you’re doing app analysis and only want the app data.
Install
git clone https://github.com/jfarley248/MEAT.git
cd MEAT
pip3 install -r requirements.txt
Use
 Copyright (C) 2020 jfarley248
Copyright (C) 2020 jfarley248
Source: https://github.com/jfarley248/