Mobile Security Framework (MobSF) v3.7.6 Releases

Mobile Security Framework
Mobile Security Framework (MobSF) is an intelligent, all-in-one open source mobile application (Android/iOS/Windows) automated pen-testing framework capable of performing static and dynamic analysis. It can be used for effective and fast security analysis of Android, iOS and Windows Mobile Applications and supports both binaries (APK, IPA & APPX ) and zipped source code. MobSF can also perform Web API Security testing with it’s API Fuzzer that can do Information Gathering, analyze Security Headers, identify Mobile API specific vulnerabilities like XXE, SSRF, Path Traversal, IDOR, and other logical issues related to Session and API Rate Limiting.
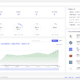
Screenshots
Static Analysis – Android APK
Static Analysis – iOS IPA
Static Analysis – Windows APPX
Dynamic Analysis – Android APK
Web API Fuzzer
Changelog v3.7.6
- Features or Enhancements
- Docker base image update to Ubuntu 22.04
- Dockerfile QA
- Migrated from Pip to Poetry for dependency management
- Migrate from setup.py to use poetry for build and publish
- Python 3.11 support
- Docker ADB connection improvements (host.docker.internal translation for localhost)
- IOS Swift RulesUpdates
ios_biometric_bool,ios_biometric_acl,ios_keychain_weak_acl_device_passcode,ios_keychain_weak_accessibility_value,ios_insecure_random_no_generator,ios_biometry_hardened - Android SCA rules update
- Entropies scan support for strings
- Regex Hardening: Fixes possible Regex DoS in rules and MobSF code base
- Tox QA
- Added poetry build test
- Updated mobsf PyPI publishing workflow
- Update local DBs
- URLs/Email extraction refactor
- Static and Dynamic Binary Analysis QA
- Refactor Dex permissions
- Refactor Androguard
apk.APK()usage - Fallback certificate analysis using apksigtool
- Use BeautifulSoup4 to prettify malformed XML
- Detect non standard XML namespace in AndroidManifest.xml, Fixes : #2198
- Updated android permissions list
- Updated android permission update check script
- Github Actions version update
- Apktool bump
- Bump httptools
- Bump yara-python-dex
- Docker image build test for PRs
- iOS Source Report Fix
- Removed unwanted pinned repository
- Frida APK Patcher (WIP)
- Fix for Recent Scans
scan not completedfor iOS zip - Fix for MachO stripped symbols false positive
- Fix bug in IPA download
- iOS/Android form validation fix
- Fix missing exported components
- Enterprise Feature Request
- String extraction from APK, Source, AAR, JAR, SO.
- Android strings sections to show source of strings extracted
- Strings extraction refactor
- Support for independent
.soscan - Dylib analysis support
- Dylib string extraction
- Improved iOS Plist secret extraction
- Support for Independent
.dylibscan - Symbols view for dylib and so
- Trackers support for so
- AAR/JAR obfuscation and debug check
- Independent Static Library(.a) ELF/MachO Analysis
- Mac FAT binary only supported on Mac
What’s Changed
- Update dynamic_analysis.html by @ajinabraham in #2218
- Hotfix: Handle Docker <-> ADB connectivity internally by @ajinabraham in #2219
- update apktool to 2.8.1 by @superpoussin22 in #2220
- update apktool by @superpoussin22 in #2225
- HOTFIX: Dynamic Analyzer Support Alert by @ajinabraham in #2227
- [HOTFIX] Regex + Rule Update by @ajinabraham in #2232
- [EFR06] Independent Shared Object (.so) Scan and Improved String search by @ajinabraham in #2228
- Update macho_analysis.py – SYMBOLS STRIPPED False Negative by @Karmaz95 in #2234
- [EFR-08] Dylib + Symbols + Other Features by @ajinabraham in #2239
- Fix missing exported components by @Abb4d0n in #2176
- [EFR09] AAR/JAR obfuscation and debug check + Exception Handed strings and symbols extraction by @ajinabraham in #2240
- [EFR10] Independent Static Library(.a) ELF/MachO Analysis by @ajinabraham in #2242
- Pip to poetry and Dockerfile update by @ajinabraham in #2244
- Docker Buildx test by @ajinabraham in #2247
- [HOTFIX] bs4 malformed xml parsing + xml namespace detection by @ajinabraham in #2248
- [HOTFIX] Migrate from setup.py to poetry, tox QA by @ajinabraham in #2249
Download & Tutorial
Copyright (C) 2015 Ajin Abraham