
Rapid7 Labs and its Managed Detection and Response (MDR) team uncovered a sophisticated modular Java-based Remote Access Trojan (RAT) deployed in a multi-stage attack targeting Cleo file transfer software. This campaign, exploiting a known vulnerability (CVE-2024-50623), represents a significant leap in the capabilities of modern threat actors.
The attack begins with the exploitation of Cleo’s XML-based configuration files. Malicious XML payloads define commands that trigger a chain of events, eventually executing an encoded PowerShell script. Rapid7 explained, “The script establishes a TCP connection to a suspicious external host and retrieves a payload, which is decrypted into a JAR file and executed within Cleo’s embedded Java runtime.”
This embedded Java runtime bypasses system-wide Java installations, making detection and mitigation more challenging.
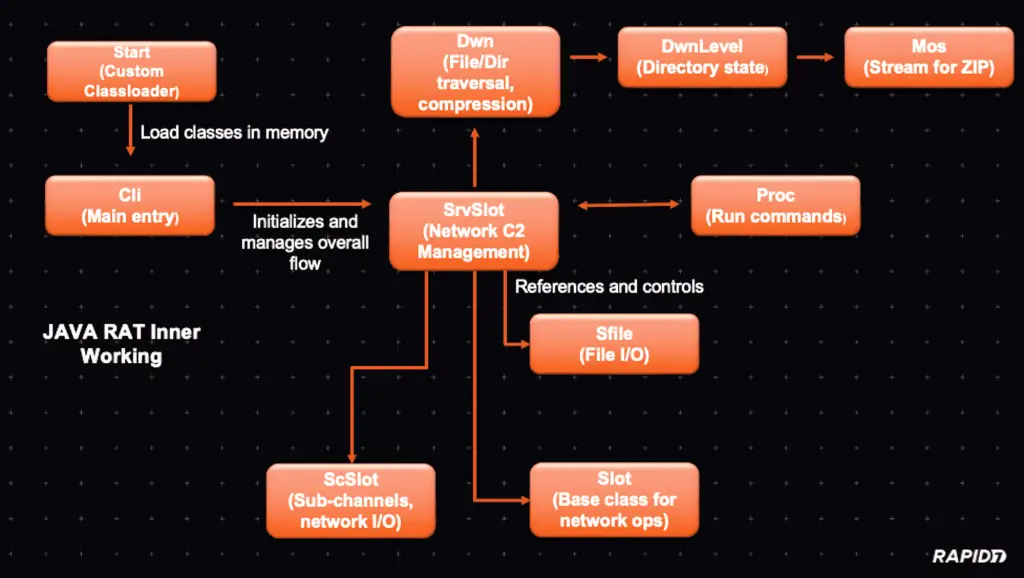
The Java RAT, observed in the Cleo exploitation campaign, demonstrates a highly modular design. Rapid7 researchers noted, “Its modular architecture includes components for dynamic decryption, network management, and staged data transfer.” Key capabilities include:
- System reconnaissance: Gathering system, user, and network information.
- File exfiltration: Compressing and transferring files to attacker-controlled servers.
- Command execution: Running shell commands and parsing their output.
- Encrypted communication: Ensuring stealthy data transfer with packet-level encryption.
The RAT’s core revolves around a custom class loader named “start“, which dynamically loads classes from encrypted archives. This mechanism enables the RAT to fetch critical code at runtime, keeping its initial footprint minimal.
After successful deployment, attackers used reconnaissance commands like systeminfo and whoami to map the environment. Rapid7 also observed “OverPass-The-Hash” attacks, leveraging NTLM hashes to obtain Kerberos tickets and access additional network resources.
The campaign’s network activity involved connections to multiple IP addresses, including:
- 185.181.230[.]103
- 89.248.172[.]139
These IOCs serve as critical detection points for organizations using Cleo software.
Rapid7 emphasized the importance of timely detection and response, stating, “This isn’t necessarily the only payload that has or will be deployed in attacks targeting Cleo software.” Organizations must prioritize patch management, monitor suspicious network activity, and strengthen their defenses against modular malware.
Related Posts:
- CVE-2024-50623: Critical Vulnerability in Cleo Software Actively Exploited in the Wild
- PoC Exploit Code Releases Cleo Zero-Day Vulnerability (CVE-2024-50623)
- Researcher warns: Java-Based Stealer Spreads via Cracked Software
- Excel File Unleashes Sophisticated Cobalt Strike Cyberattack
- AsyncRAT Malware Campaign Exploits Bitbucket to Deliver Multi-Stage Attack