Mole: Automatic SQL Injection Exploitation Tool
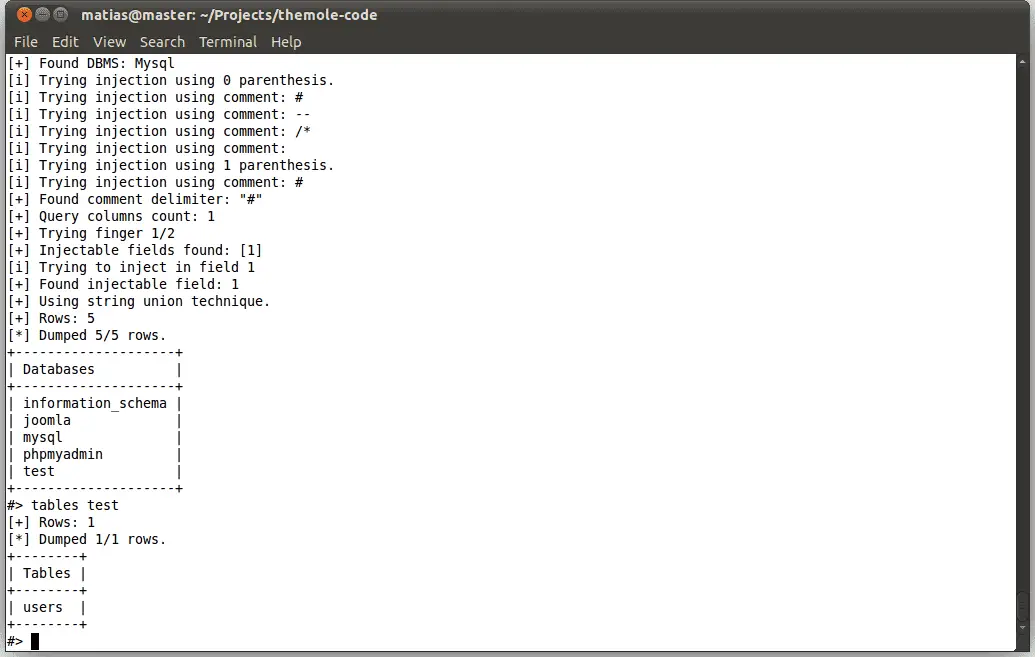
Mole is an automatic SQL Injection exploitation tool. Only by providing a vulnerable URL and a valid string on the site it can detect the injection and exploit it, either by using the union technique or a boolean query based technique. The Mole uses a command based interface, allowing the user to indicate the action he wants to perform easily. The CLI also provides auto-completion on both commands and command arguments, making the user type as less as possible.
Features
- Support for Mysql, Postgres, SQL Server and Oracle.
- Automatic SQL injection exploitation using union technique.
- Automatic blind SQL injection exploitation.
- Exploits SQL Injections in GET/POST/Cookie parameters.
- Support for filters, in order to bypass certain IPS/IDS rules using generic filters, and the possibility of creating new ones easily.
- Exploits SQL Injections that return binary data.
- The powerful command interpreter to simplify its usage.
Download
Usage
In order to execute The Mole, you require only python3 and python3-lxml. Once you execute it, a shell prompt will be printed, waiting for commands. You can additionally use some program arguments:

Copyright (C) Matías Fontanini, Santiago Alessandri, Gastón Traberg
Source: https://github.com/tiankonguse/




