msidump
MSI Dump – a tool that analyzes malicious MSI installation packages, extracts files, streams, and binary data, and incorporates YARA scanner.
On Macro-enabled Office documents we can quickly use oletools mraptor to determine whether a document is malicious. If we want to dissect it further, we could bring in oletools olevba, or oledump.
To dissect malicious MSI files, so far we had only one, but reliable and trustworthy lessmsi. However, lessmsi doesn’t implement the features I was looking for:
- quick triage
- Binary data extraction
- YARA scanning
Hence this is where msidump comes into play.
Features
This tool helps in quick triages as well as detailed examinations of malicious MSIs corpora. It lets us:
- Quickly determine whether file is suspicious or not.
- List all MSI tables as well as dump specific records
- Extract Binary data, all files from CABs, scripts from CustomActions
- scan all inner data and records with YARA rules
- Uses file/MIME type deduction to determine inner data type
It was created as a companion tool to the blog post I released here:
Limitations
- The program is still in an early alpha version, things are expected to break, and triaging/parsing logic to change
- Due to this tool’s heavy reliance on Win32 COM WindowsInstaller.Installer interfaces, currently it is not possible to support native Linux platforms. Maybe wine python msidump.py could help but haven’t tried that yet.
Download
git clone https://github.com/mgeeky/msidump.git
Use
- Perform quick triage of a suspicious MSI augmented with the YARA rule:
cmd> python msidump.py evil.msi -y rules.yara
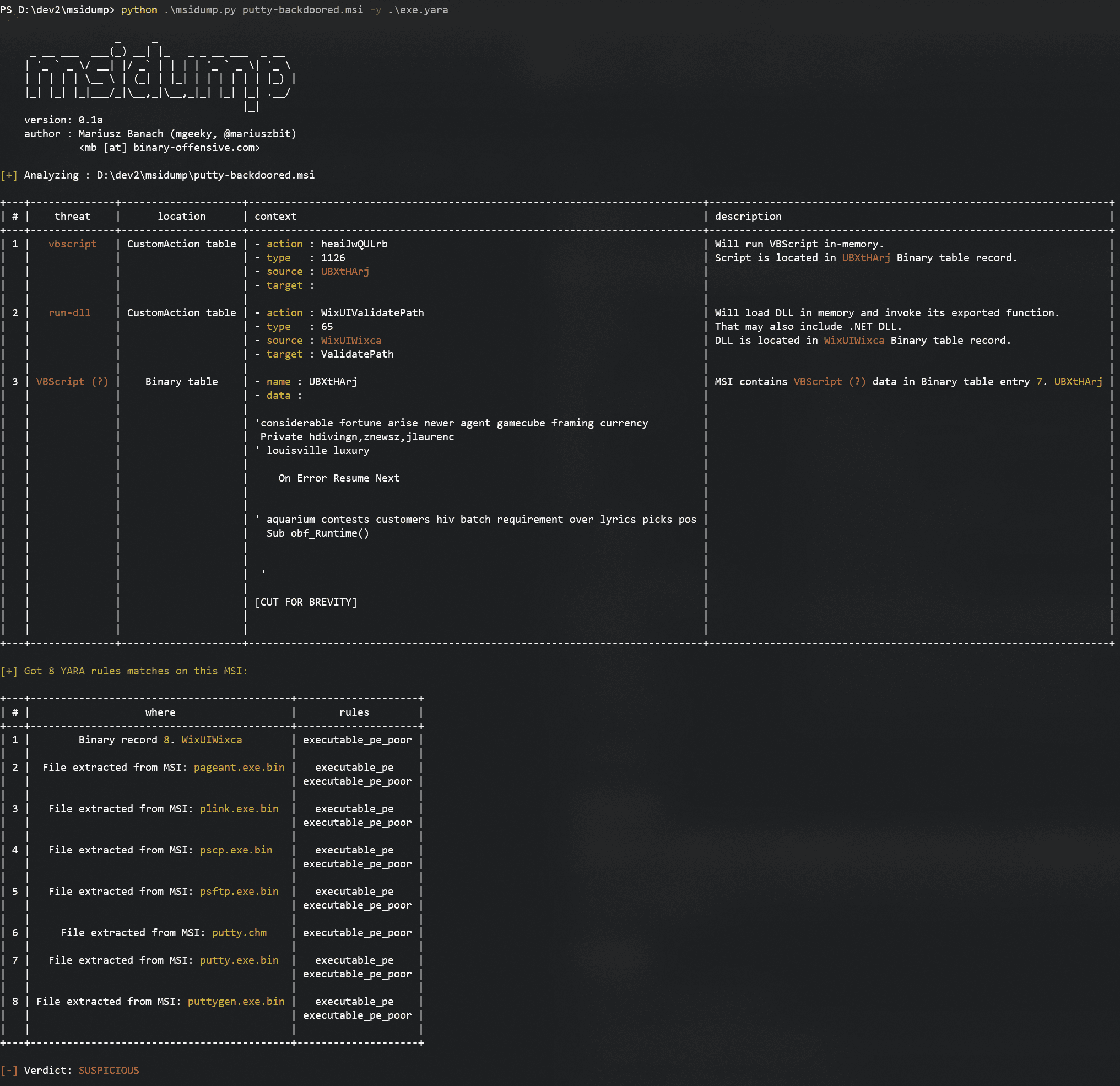
Here we can see that input MSI is injected with suspicious VBScript and contains numerous executables in it.
- Now we want to take a closer look at this VBScript by extracting only that record.
We see from the triage table that it was present in the Binary table. Let’s get him:
python msidump.py putty-backdoored.msi -l binary -i UBXtHArj
We can specify which to record dump either by its name/ID or its index number (here that would be 7).

Let’s have a look at another example. This time there is an executable stored in the Binary table that will be executed during installation:
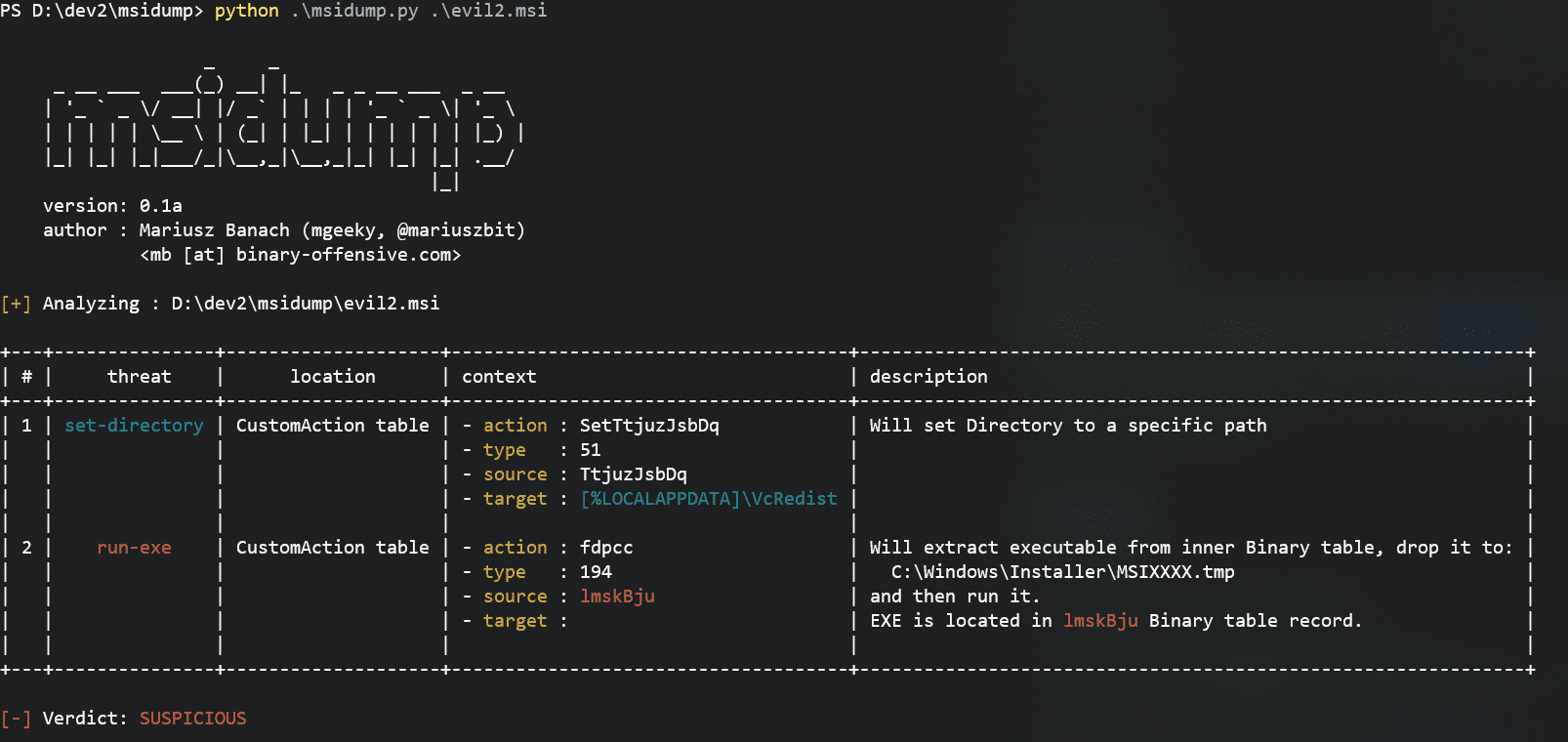
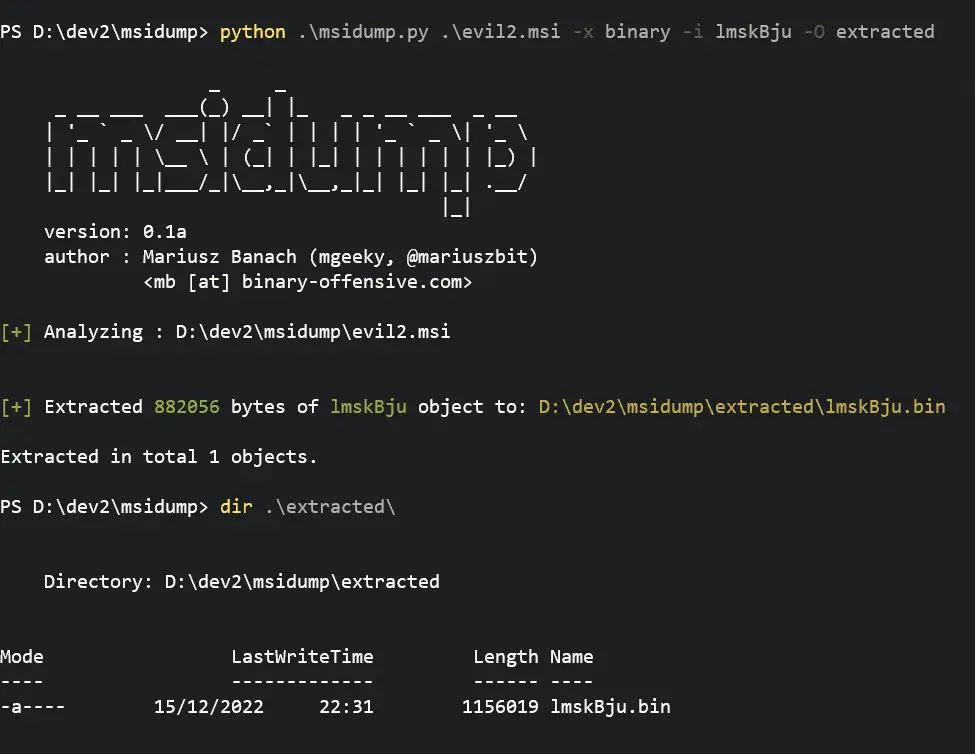
To extract that file we’re gonna go with
python msidump.py evil2.msi -x binary -i lmskBju -O extracted
Where
- -x binary tells to extract the contents of Binary table
- -i lmskBju specifies which record exactly to extract
- -O extracted sets output directory
For the best output experience, run the tool on a maximized console window or redirect output to the file:
python msidump.py […] -o analysis.log
Source: https://github.com/mgeeky/