Diamond Model | Image:
In the ever-evolving landscape of cyber threats, a new formidable player has emerged: the Bluesky ransomware. This malicious software, first detected in June 2022, has rapidly gained notoriety for its effective exploitation of vulnerabilities, drawing parallels with infamous ransomware strains like Conti and Babuk. The DFIR Report‘s detailed analysis sheds light on an intrusion that exemplifies Bluesky’s alarming capabilities.
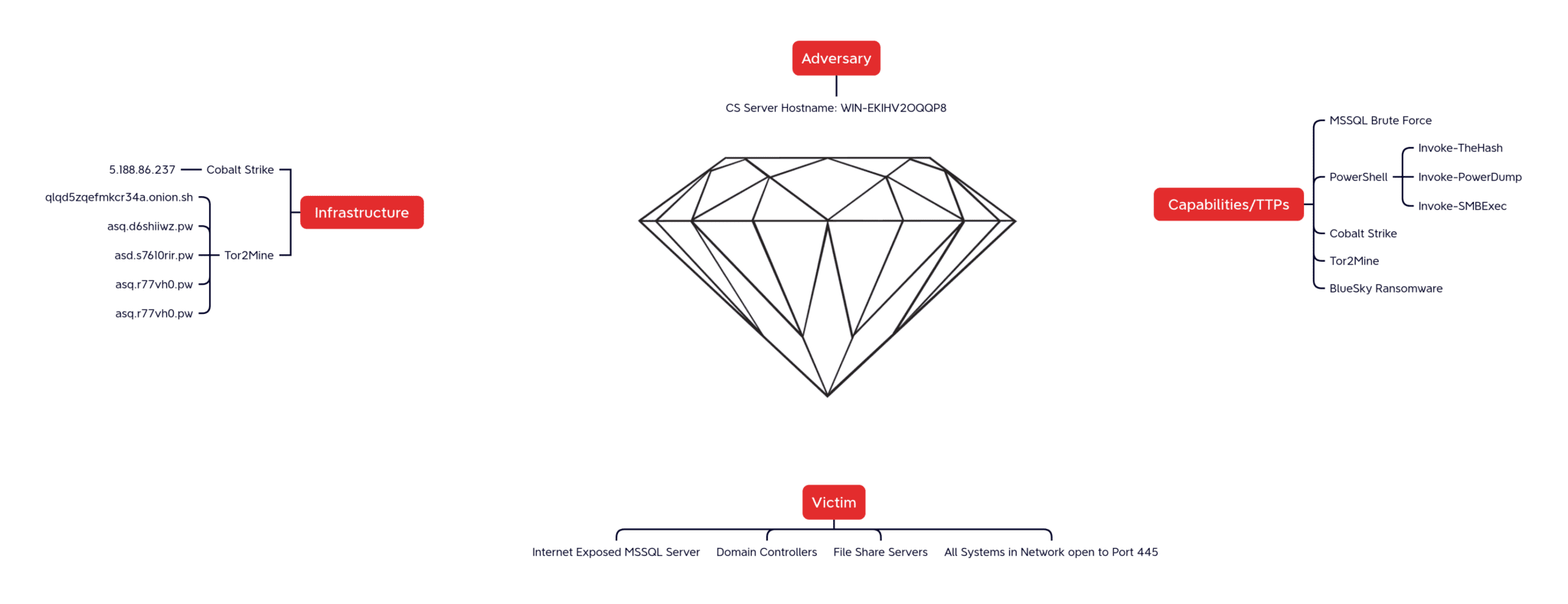
The incident in question transpired in December 2022, targeting a public-facing Microsoft SQL Server (MSSQL). Unlike typical ransomware attacks that capitalize on malware downloads for initial access, Bluesky’s operators opted for a more surreptitious approach. They executed a relentless SQL brute force attack, specifically aiming at the MSSQL “sa” (System Administrator) account. Upon cracking the password, the attackers unlocked “xp_cmdshell” on the server, a powerful tool that enables the execution of shell commands directly from SQL.
Post successful entry, the Bluesky actors wielded Cobalt Strike, a legitimate software tool repurposed for malicious intent, and Tor2Mine, a script known for Monero mining and XMRigCC deployment. The attackers’ proficiency was evident in their rapid progression within the network, managing to inject code into the legitimate winlogon.exe process and spawning additional PowerShell and cmd processes. These were used for SMB scans and further network discovery, all within an hour of initial access.

The Bluesky ransomware was unleashed about 30 minutes post initial breach. Its deployment was chillingly efficient, spreading across the entire network via SMB. Files were encrypted and renamed with the .bluesky extension, and a ransom note, “# DECRYPT FILES BLUESKY #.txt”, materialized on infected hosts. Astonishingly, the total time from intrusion to full-scale encryption was a mere 32 minutes.
The technical prowess of Bluesky’s operators was further highlighted by their lateral movements across the network, targeting domain controllers and file shares. They adeptly disabled antivirus solutions and established persistence through scheduled tasks and Windows services linked to their malicious payloads. Their use of PowerShell scripts for various operations, including disabling AV solutions and dropping miner payloads, demonstrated a high level of sophistication and understanding of the target environment.
The Bluesky ransomware case is a stark reminder of the evolving threat landscape in cyberspace. The rapidity and efficiency of the attack, combined with the use of sophisticated tools and techniques, underscore the need for robust cybersecurity measures. Organizations must prioritize strong password policies, regular software updates, network monitoring, and employee awareness to mitigate such threats.
In conclusion, Bluesky ransomware is not just another malware; it’s a harbinger of the sophisticated cyber threats that loom over the digital world. Vigilance, preparedness, and continuous adaptation are the keys to defending against such insidious cyber threats.