MuddyWater Strikes Again: New ‘DarkBeatC2’ Framework Targets Israel
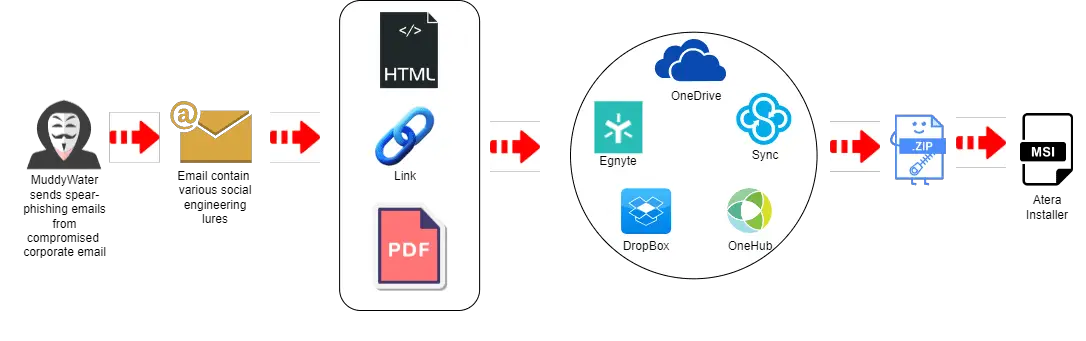
Deep Instinct’s Threat Research team has uncovered a sophisticated campaign spearheaded by MuddyWater, an entity known for its state-sponsored activities, unveiling a new tool in their arsenal: the DarkBeatC2 framework.
Amidst the backdrop of the “Swords of Iron War,” Iranian cyber operatives ramped up their hack-and-leak operations against Israeli private sector entities, marking an aggressive shift in their cyber espionage endeavors. This intensification mirrors the broader geopolitical strife, underscoring the cyber domain as a pivotal battlefield for national security confrontations.
The Deep Instinct report shines a spotlight on DarkBeatC2, a previously uncharted command-and-control (C2) framework attributed to MuddyWater, an Iranian threat group. This toolkit is a testament to the sophisticated nature of state-sponsored cyber operations, enabling remote manipulation and data extraction from compromised systems.

Updated MuddyWater campaign overview
Deep Instinct’s analysis reveals a complex tapestry of attacks, supply-chain vulnerabilities, and espionage tactics. Notably, the Iranian actors showcased an adeptness at leveraging information from previous breaches to facilitate subsequent supply-chain attacks, illustrating a cyclical pattern of compromise and exploitation.
The research underscores a concerning trend: the limited disclosure of technical details surrounding these cyber attacks within Israeli channels. While international entities have shared insights into the technical underpinnings of these operations, local Israeli response teams and the Israel National Cyber Directorate (INCD) have been more reserved, often only releasing general indicators of compromise (IOCs) without deeper contextual analysis.
Deep Instinct’s foray into the shared IOCs reveals a nuanced understanding of the attacks, linking various wipers and webshells to Iranian actors and their sophisticated operations. For instance, the investigation connected certain webshells to the FoxShell variant used by ScarredManticore, indicative of the targeted, meticulous nature of these attacks.
The investigation also highlights the strategic use of compromised domains and IP addresses by MuddyWater, revealing the depth of planning and coordination behind their campaigns. This includes the exploitation of educational and governmental institutions, demonstrating the broad spectrum of targets within the Iranian cyber strategy.
The centerpiece of Deep Instinct’s report, DarkBeatC2, emerges as a highly versatile C2 framework, enhancing MuddyWater’s capability to conduct espionage and sabotage operations. Its deployment signifies a leap in the operational sophistication of Iranian cyber activities, equipped with features for stealthy communication, data exfiltration, and remote command execution.
In conclusion, the DarkBeatC2 framework marks a significant development in the ongoing cyber confrontation between Iran and Israel. It not only sheds light on the technical prowess of Iranian cyber forces but also calls for an enhanced collective security posture among nations and organizations at the forefront of digital defense. As the cyber espionage landscape evolves, so too must our strategies to detect, deter, and defend against these insidious threats.





