MuddyWater’s Sneaky New Tactic: Hijacking RMM Software for Espionage
Security researchers from the 360 Advanced Threat Research Institute have recently uncovered that the Iranian hacking group MuddyWater is actively leveraging legitimate remote monitoring and management (RMM) software in its attacks. This group, active since 2017, primarily targets organizations in the Middle East, as well as in Europe and North America. Their attacks focus on government institutions, military entities, telecommunications, and oil companies.
RMM software, designed for IT support and maintenance, offers remote access and control capabilities, which MuddyWater has turned into a weapon. Since 2020, the group has been observed utilizing a range of popular RMM programs like Remote Utilities, ScreenConnect, and Atera Agent to carry out its nefarious activities.
Phishing: The Gateway to Compromise
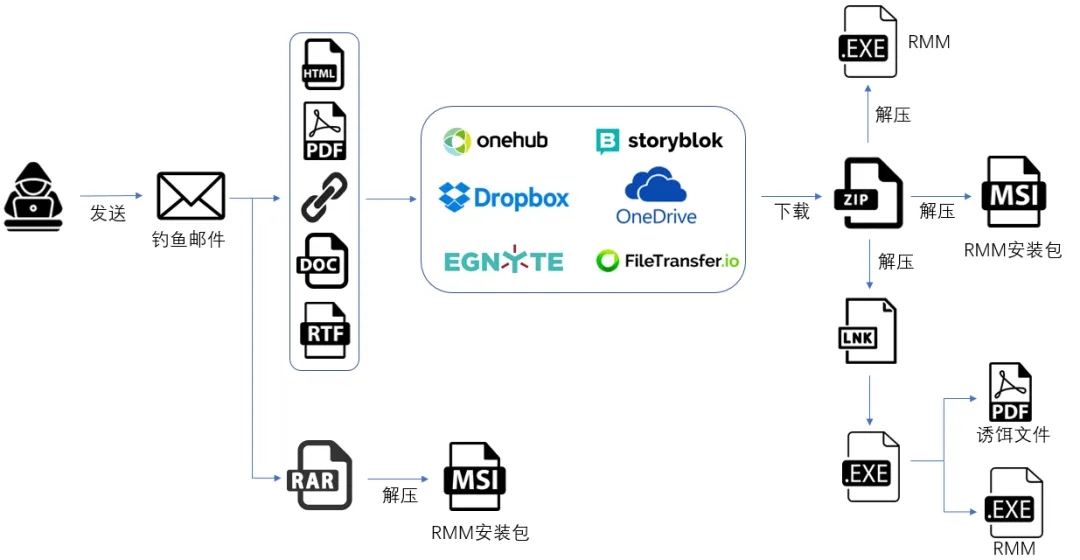
MuddyWater’s modus operandi typically starts with a carefully crafted phishing email. These emails, often containing attachments disguised as Arabic documents, lure unsuspecting victims into opening the door to their systems. Once opened, these attachments silently install the malicious RMM software, effectively handing over the keys to the attackers.
Once inside, the hackers can execute commands, upload and download files, and move laterally within the network – all while remaining undetected. This stealthy approach allows them to conduct espionage activities, steal sensitive data, and potentially cause significant disruptions.
A Continuously Evolving Threat
MuddyWater, known for its targeted attacks against government, military, telecommunications, and oil companies primarily in the Middle East but also globally, is continuously refining its techniques. Researchers have observed the group adding new tools to its arsenal, including Syncro, an RMM tool that can be spread through HTML files, making it even harder to detect.
The use of legitimate software for malicious purposes poses a serious challenge for defenders. Traditional security solutions may struggle to identify and block these attacks, as the software itself is not inherently malicious.
The Need for Vigilance
The 360 Advanced Threat Research Institute urges organizations to be extra vigilant. It’s crucial to raise employee awareness about phishing scams and the risks of opening unfamiliar files or links. Regular security updates and comprehensive endpoint protection are also critical in defending against such threats.
The MuddyWater campaign is a stark reminder that the cyber threat landscape is constantly changing. Even trusted tools can be weaponized by sophisticated attackers. It underscores the need for continuous vigilance and proactive security measures to protect against evolving threats. Remember, the next phishing email could be the gateway to a serious breach.
Related Posts:
- Iranian Hacker Group MuddyWater Abuses Legitimate Atera Software to Target Global Organizations
- MuddyWater APT Exploits MSP Tools to Target Global Victims
- MuddyWater Strikes Again: New ‘DarkBeatC2’ Framework Targets Israel
- Critical Fortinet Vulnerability Exploited: Hackers Deploy Remote Control Tools and Backdoors
- Deep Instinct Reveals Iranian APT MuddyWater’s Latest Cyber-weapon: MuddyC2Go