Image: IBM X-Force Red
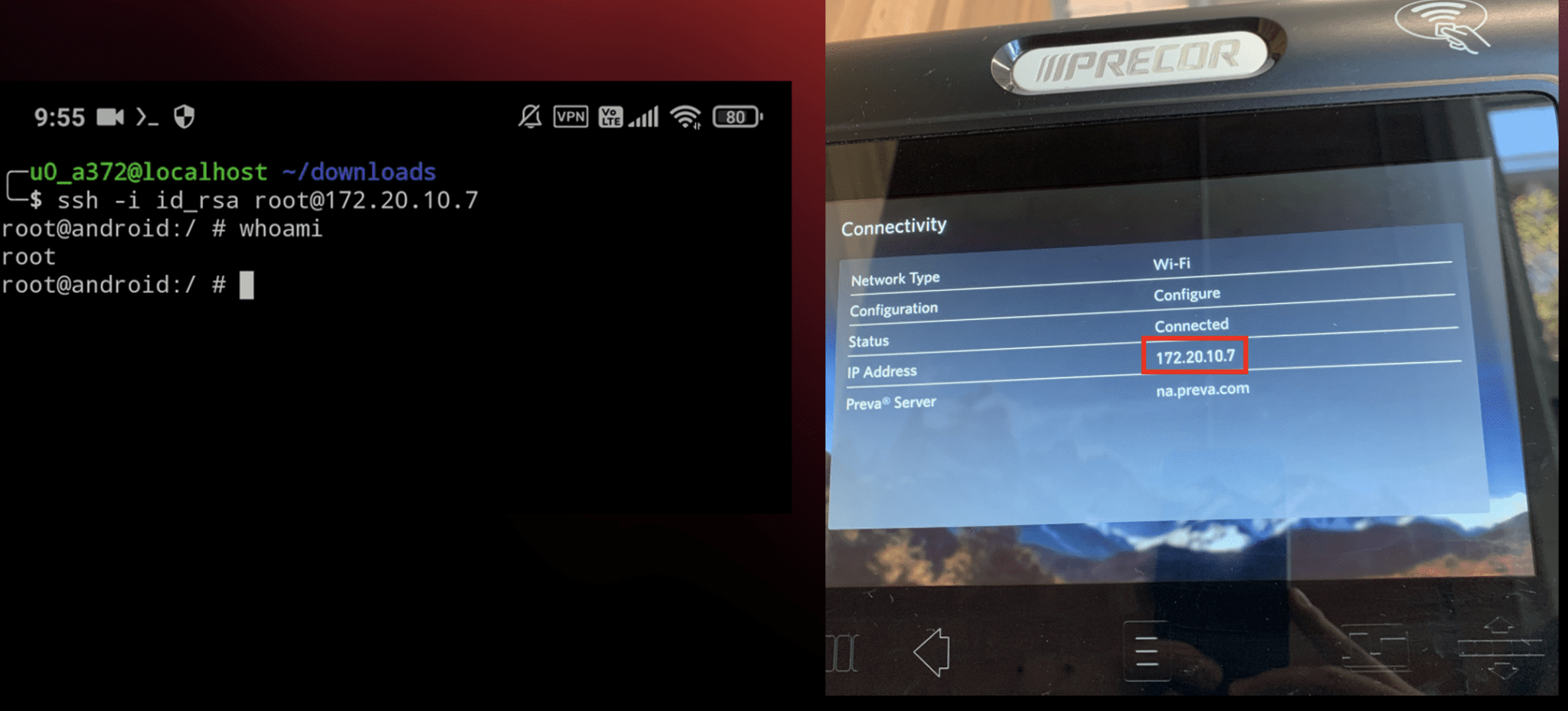
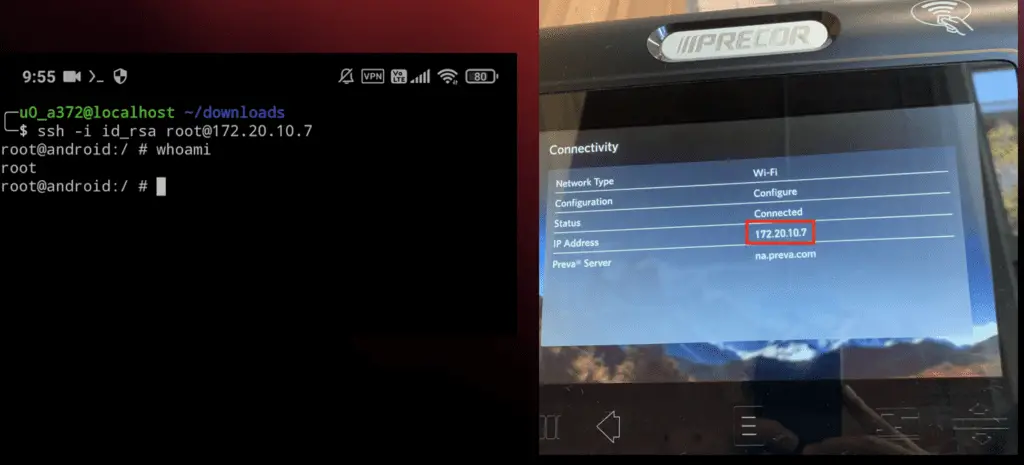
IBM X-Force Red, a team of cybersecurity researchers, has uncovered critical vulnerabilities in Precor smart treadmills, raising concerns about user safety and data security. The vulnerabilities, identified in three console models (P80, P62, and P82), could allow unauthorized actors to gain root access to the treadmill’s operating system. The vulnerability, identified as CVE-2023-49221, CVE-2023-49222, CVE-2023-49223, and CVE-2023-49224, highlights the severe risks associated with these findings.
Vulnerabilities Discovered:
- Exposed SSH Key Pair: Researchers found an exposed SSH key pair in the treadmill’s software update packages, potentially granting attackers remote root access.
- Weak Password Hashing: The root user account password was protected with a weak hashing algorithm, making it susceptible to cracking.
- Physical Safety Risk: With root access, an attacker could potentially manipulate treadmill functions, including abruptly stopping the belt, posing a physical risk to users.
The vulnerabilities affect Precor treadmill models with the following console versions: P80_7.2.11, P62_8.3.2, P82_8.3.2, and P82_9.2.3_M. Precor has released patched software for these versions and urges users to update their devices immediately.
To further protect users of smart gym equipment, the following measures are recommended:
- Ensure these devices operate on a separate, secured network to prevent unauthorized access.
- Disconnect the equipment from the internet if online features are not in use.