multitor v1.3.0 releases: create multiple TOR instances
multitor
A tool that lets you create multiple TOR instances with a load-balancing traffic between them by HAProxy. It provides one single endpoint for clients. Support socks protocol and http-proxy servers: polipo, privoxy and hpts. In addition, you can view previously running TOR processes and create a new identity for all or selected processes.
The multitor has been completely rewritten on the basis of:
- Multi-TOR project written by Jan Seidl: Multi-TOR
- original source is (Sebastian Wain project): Distributed Scraping With Multiple TOR Circuits

Multitor was created with the aim of initializing many TOR processes as quickly as possible. I could use many instances for my daily use programs (web browsers, messengers and other). In addition, I was looking for a tool that would increase anonymity when conducting penetration tests and testing the security of the infrastructure.
Before using the multitor you need to remember:
- TOR does attempt to generate a bunch of streams for you already. From this perspective, it is already load balancing (and it’s much smarter at it than HAproxy)
- the main goal is masking from where we get by sending requests to multiple streams. It is not so easy to locate where an attacker comes from. If you used http/https servers e.g. proxy servers, you will know what is going on but…
- using multiple TOR instances can increase the probability of using a compromised circuit
- multitor getting some bandwidth improvements just because it’s a different way of connecting to TOR network
- in multitor configuration mostly HAProxy checks the local (syn, syn/ack) socket – not all TOR nodes (also exist nodes). If there is a problem with the socket it tries to send traffic to others available without touching what’s next – it does not ensure that the data will arrive
- TOR network is a separate organism on which the multitor has no effect If one of the nodes is damaged and somehow the data can not leave the exit node, it is likely that a connection error will be returned or, at best, the data will be transferred through another local socket
- HAProxy load balance network traffic between local TOR or http-proxy processes – not nodes inside TOR network
TOR is a fine security project and an excellent component in a strategy of defence in depth but it isn’t (sadly) a cloak of invisibility. When using the TOR, always remember about ssl (e.g. https) wherever it is possible.
Install
git clone https://github.com/trimstray/multitor cd multitor ./setup.sh install
Use
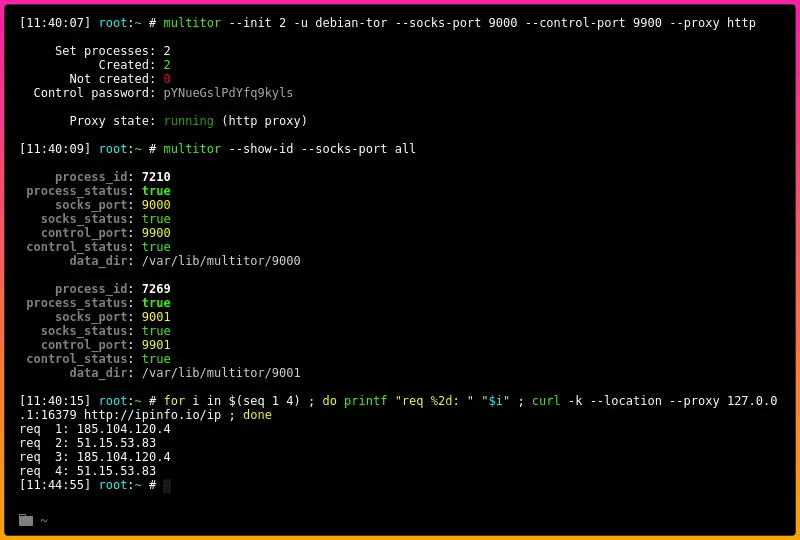
multitor --init 2 --user debian-tor --socks-port 9000 --control-port 9900 --proxy http
- symlink to bin/multitor is placed in /usr/local/bin
- man page is placed in /usr/local/man/man8
Parameters
Provides the following options:
Tutorial
Important
If you use this tool in other scripts where the output is saved everywhere, not on the screen, remember that you will not be able to use the generated password. I will correct this in the next version. If you do not use regenerate function of single or all TOR circuits with a password, you can safely restart the multitor which will do it for you.
Limitations
- each TOR, http-proxy and HAProxy processes needs a certain number of memory. If the number of TOR processes is too big, the oldest one will be automatically killed by the system
- Polipo is no longer supported but it is still a very good and light proxy. In my opinion, the best http-proxy solution is Privoxy
- I think this topic will be useful for You before using multitor – How to run multiple Tor processes at once with different exit IPs?
Copyright (C) 2018 trimstray
Source: https://github.com/trimstray/





