Necurs is the world most massive spam botnet and consists of millions of infected computers. It was used to spread malware such as Locky and GlobeImposter Trickbot. In April, the researchers found that Necurs’s manipulator used a new technique to circumvent detection—send messages to the victim containing compressed files. After decompression, files with the .URL extension appears. These files will be remotely transmitted using the Server Message Block (SMB) protocol. The server performs a payload to avoid specific spam filters successfully. Trend Micro recently discovered that the author of Necurs appeared to have upgraded their avoidance method after being discovered.
This time, a new round of spam from the botnet uses the Web query file IQY to evade detection. A text file IQY file with a specific format allows users to import data from an external source into an Excel spreadsheet, and Windows automatically executes them in Excel.
 Figure 1. E-mail with IQY attachments
Figure 1. E-mail with IQY attachments
Trend Micro revealed that Necurs uses the IQY file attachment spam subject and file name to include related vocabulary for promotions, offers, and discounts. Once executed, the IQY a file will query the URL indicated in its code, which will cause the data to be pulled from the destination URL into the Excel worksheet. The acquired data contains scripts that abuse the Excel Dynamic Data Exchange (DDE) feature to execute the command line and start the PowerShell process. Through this process, remote PowerShell scripts run without a file on the target system. This script is designed to download executable files, Trojan horse remote access applications and their final payload: the FlawedAMMYY backdoor. The malware should be built using the Ammyy Admin remote access Trojan leak code. As part of a recent attack, the script downloads an image file before the final payload. Security researchers said that this image is a disguised malware download program that is used to obtain cryptographic component files that contain the same major backdoor routines.
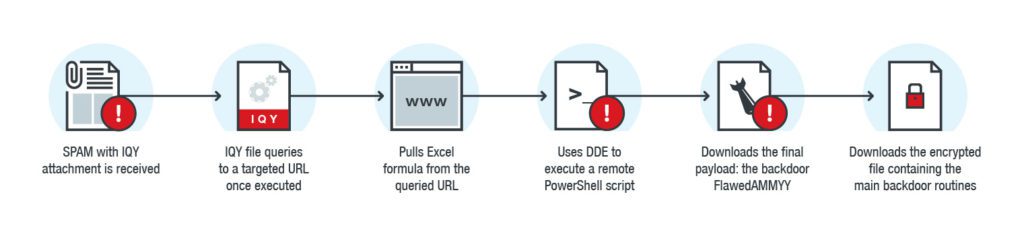 Figure 2. Chain of infection starting with an attached IQY file
Figure 2. Chain of infection starting with an attached IQY file
FlawedAMMYY is designed to execute a series of commands for remote malicious servers, including a file manager, view screen, remote control, audio chat, RDP SessionsService – install/start/stop/delete disable desktop background, disable desktop composition, disable visual effects and display The tool prompts the mouse cursor to flash.
Adding this new avoidance layer in Necurs brings new challenges because web queries usually appear in the form of manifest files, which makes the URL of the attached IQY file the only indication of malware activity. Also, its structure is the same as standard Web queries. Therefore, a security solution that can prevent malicious URLs can counter this threat.
To withstand these threats, strict security protocols and best practices are critical. Also, since this is a known attack vector, users will receive two warning messages when executing IQY file attachments. If these warnings are noted, they can stop the infection.
Source, Image: TrendMicro