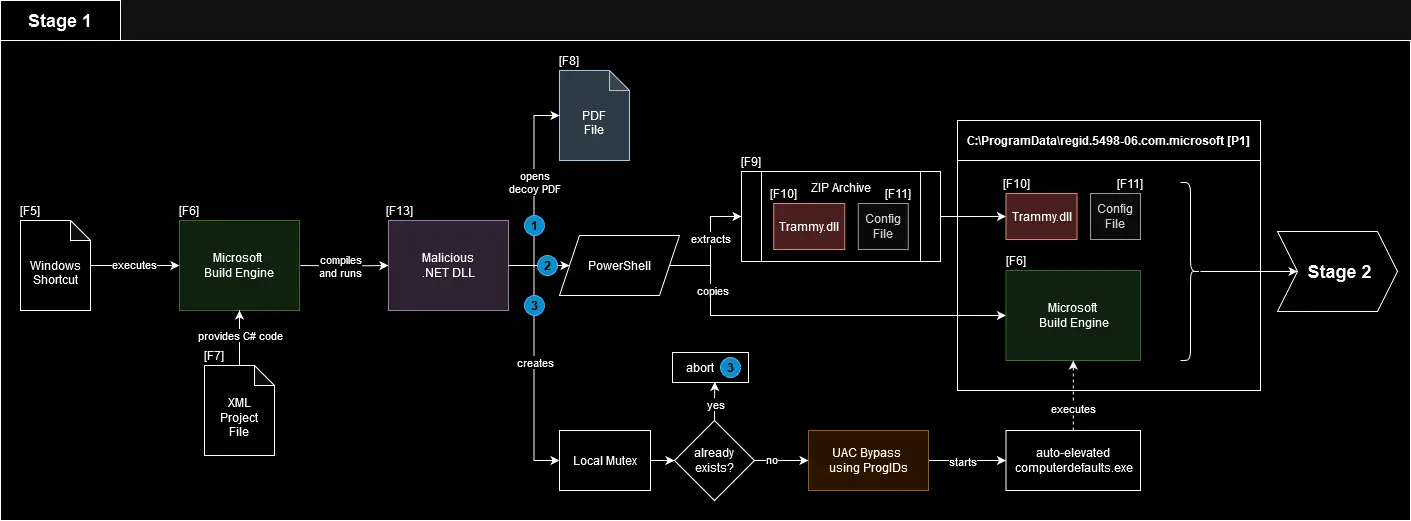
Utilizing Microsoft Build Engine to execute .NET DLLs | Image: G DATA
In a recent analysis by G DATA CyberDefense, a complex malware infection chain targeting Brazilian entities has been uncovered, utilizing obfuscated .NET loaders and advanced persistence techniques. The malware, linked to the BBTok banking trojan, employs a multi-staged approach, beginning with an ISO image delivered via email, disguised as a digital invoice commonly used in Brazil.
The infection chain begins with a malicious ISO image attached to phishing emails, masquerading as a legitimate digital invoice, “Documento Auxiliar da Nota Fiscal Electronica” (DANFE). Once the victim opens the ISO, the infection initiates through a Windows shortcut file (LNK) disguised with a PDF icon, luring the user into executing the malicious payload.

What sets this attack apart is the use of the Microsoft Build Engine (MSBuild.exe), a legitimate Windows tool that compiles malicious C# code directly on the infected machine. The malware compiles a .NET DLL, named Trammy.dll, from the embedded C# code, which is then executed to maintain persistence and continue the infection process. This method allows the malware to evade detection by traditional security tools, as the malicious payload is dynamically generated and executed on the victim’s system.
The malware further leverages a technique known as AppDomain Manager Injection, where the Trammy.dll is registered as an AppDomain Manager. This allows it to execute malicious code during the initialization of a new AppDomain, giving the attackers greater control over the infected environment. This advanced method of execution is rarely seen in common malware and highlights the sophistication of the attack.
The .NET loader Trammy.dll is obfuscated using a variant of ConfuserEx, making it challenging for traditional deobfuscation tools to retrieve the encoded strings. G DATA researchers used dnlib, a powerful .NET library, along with custom PowerShell scripts, to successfully deobfuscate the malware’s strings. By analyzing the decompiled code, the team was able to identify several key functions and map out the complete infection chain.
BBTok, the malware family behind this campaign, has a history of targeting Latin American countries, particularly Brazil. The attackers have tailored the malware to execute only if the victim’s IP address is located in Brazil, further complicating detection by global security systems. This geofencing technique ensures that the malware operates primarily in the intended region, minimizing exposure in non-targeted areas.
The malware also includes several persistence mechanisms, such as creating a mutex to prevent re-execution and setting up services that allow the malware to survive system reboots. Additionally, the malware attempts to disable Windows Defender and other security tools, ensuring it can operate without interference.
An interesting component of the infection chain is the use of CCProxy, a legitimate proxy server application. The malware extracts and configures CCProxy to facilitate communication between the infected machine and the command-and-control (C2) server. By disguising itself as a legitimate network process, the malware can exfiltrate data and receive commands from the attackers without raising suspicion.
Organizations are advised to implement strict email filtering to block malicious ISO files, regularly update their software to patch known vulnerabilities, and deploy advanced endpoint protection that can detect and respond to dynamic malware threats like this.
In addition, businesses should educate their employees about the dangers of phishing emails and the risks associated with downloading files from untrusted sources. The use of multi-factor authentication (MFA) and regular security audits can also help mitigate the risks posed by advanced banking trojans like BBTok.
Related Posts:
- Cybercriminals Target LatAm Banks: Mekotio, BBTok Lead the Charge
- Flax Typhoon Botnet Exploits 66 Vulnerabilities: A Global Threat to Critical Infrastructure
- Octo2 Malware Variant Threatens European Banks with Advanced Device Takeover Attacks