netassert v2.0.3 releases: network security testing for DevSecOps workflows
netassert
netassert: network security testing for DevSecOps workflows
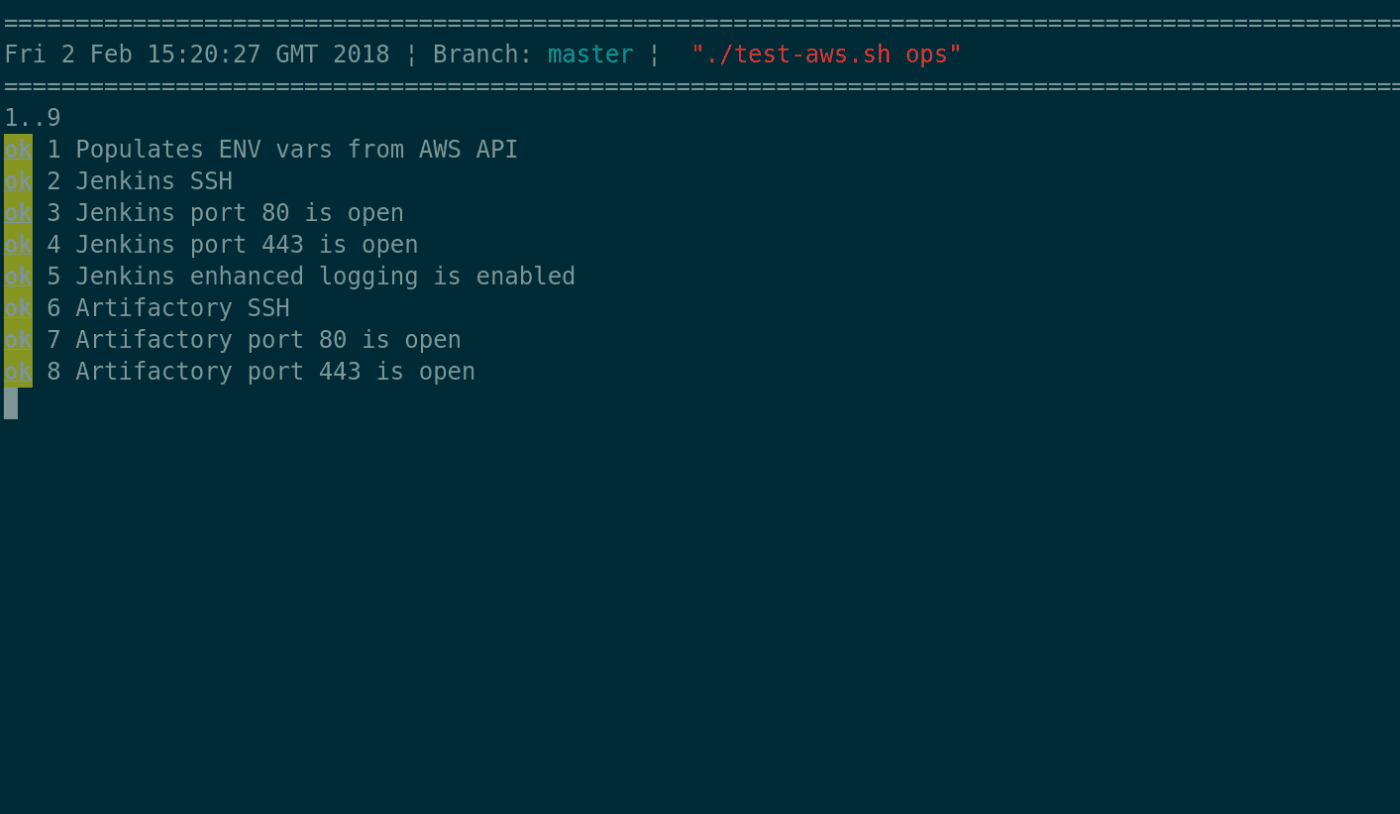
This is a security testing framework for fast, safe iteration on the firewall, routing, and NACL rules for Kubernetes (Network Policies, services) and non-containerised hosts (cloud provider instances, VMs, bare metal). It aggressively parallelizes Nmap to test outbound network connections and ports from any accessible host, container, or Kubernetes pod by joining the same network namespace as the instance under test.
Why?
The alternative is to exec into a container and curl, or spin up new pods with the same selectors and curl from there. This has lots of problems (extra tools in a container image, or tool installation despite immutable root filesystems, or egress prevention). netassert aims to fix this:
- does not rely on a dedicated tool speaking the correct target protocol (e.g. doesn’t need
curl, GRPC client, etc) - does not bloat the pod under test or increase the pod’s attack surface with non-production tooling
- works with FROM scratch containers
- is parallelized to run in near-constant time for large or small test suites
- does not appear to the Kubernetes API server that it’s changing the system under test
- uses TCP/IP (layers 3 and 4) so does not show up in HTTP logs (e.g.
nginxaccess logs) - produces TAP output for humans and build servers
More information and background in this presentation from Configuration Management Camp 2018.
Changelog v2.0.3
- 818908a fix: Upgrade to Go 1.21, test Kubernetes 1.25-1.28, refine engine & CLI
Install && Use
Copyright 2017 control-plane.io






