The NETSCOUT ASERT team, renowned for its unparalleled insight into the world’s internet traffic, has recently unearthed alarming patterns of behavior indicative of an upsurge in malicious botnet activities. This discovery sheds light on a concerning trend that is reshaping the battleground of cyber warfare.
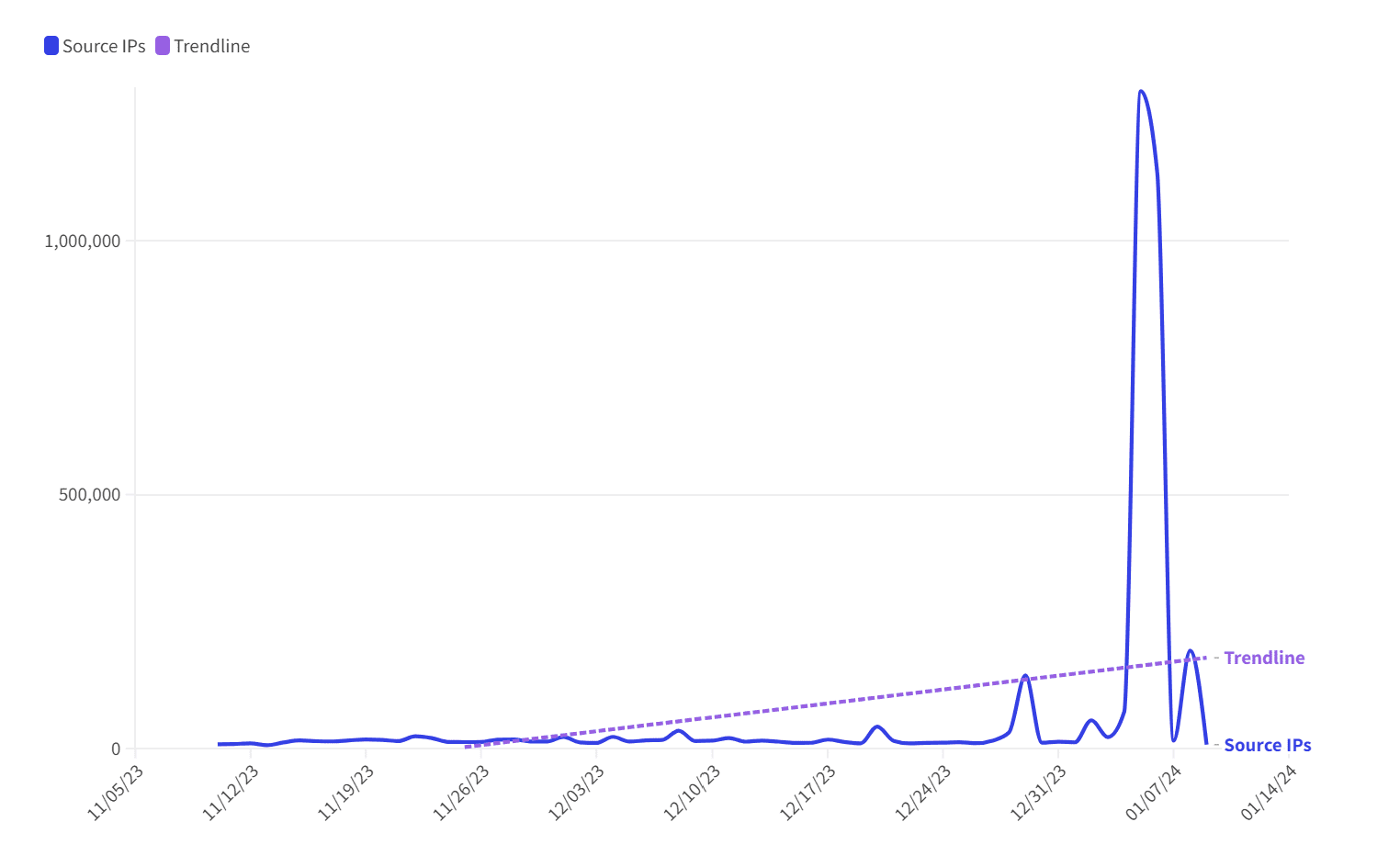
On an average day, internet traffic scans typically originate from approximately 10,000 devices, occasionally peaking at 20,000. But in a startling departure from the norm, December 2023 witnessed a series of spikes in device activity, signaling an ominous trend. The number of devices involved in these reconnaissance scans escalated to 35,144 on December 8 and further soared to 43,194 by December 20. The pattern continued with an unprecedented spike to 143,957 distinct devices on December 29, nearly ten times the usual level.

The surge in device activity can be traced back to five primary countries: the United States, China, Vietnam, Taiwan, and Russia. It appears that attackers are leveraging cheap or free cloud and hosting servers to construct botnet launch pads, exploiting trials, free accounts, or low-cost options for anonymity and operational ease.
These adversaries are utilizing their newly forged botnets to perform exhaustive scans of the global internet, targeting specific ports that are likely vulnerable to exploitation. The most commonly scanned ports include 80, 443, and 3389, among others, painting a picture of a meticulous search for vulnerabilities and potential attack vectors. Furthermore, there is evidence suggesting an impending threat to email servers, as indicated by increased scanning of ports 636, 993, and 6002.
This surge in botnet activity, particularly in the cloud, heralds a new era in cybercrime. The dramatic rise in the use of botnets points to an adversary in the reconnaissance phase, actively seeking weaknesses to exploit. This trend underscores the vital importance of robust DDoS protection as a frontline defense against these emerging threats. As we step into this new battlefield, it is clear that the fight against these formidable botnet armies is only just beginning.