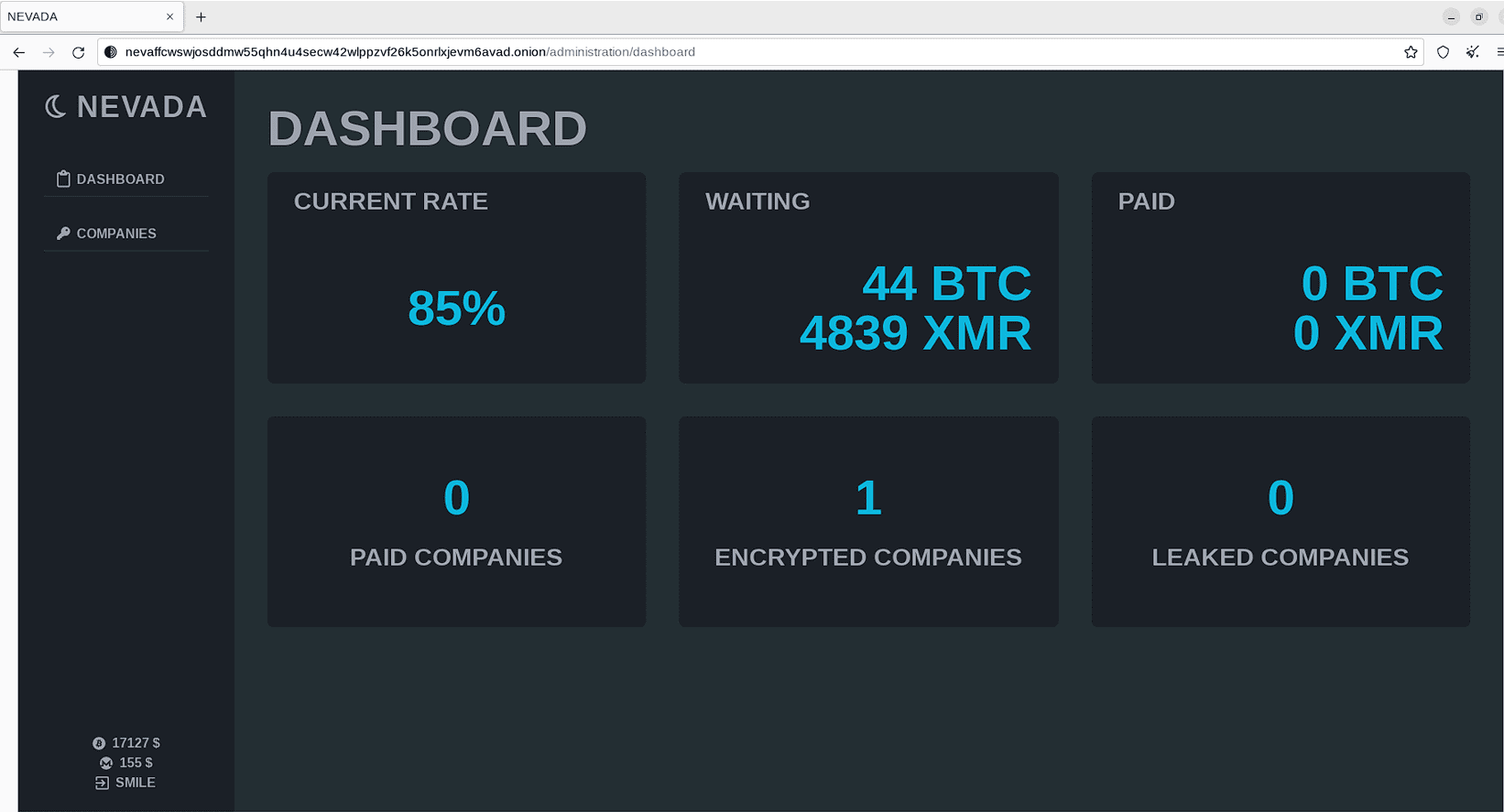
The status of the ransom payments |
Nevada Ransomware, identified by Resecurity’s threat research and intelligence team, is rapidly gaining notoriety for its advanced functionality and enticing affiliate program. Resecurity delves into the intriguing world of Nevada Ransomware, exploring its origins, tactics, and the potential risks it poses to organizations worldwide.
The Nevada Ransomware first made waves when an actor known as ‘nebel’ introduced it to the cybercriminal underground on December 10th, 2022. This initial revelation was accompanied by an open invitation for new affiliates to join their ranks. What sets Nevada Ransomware apart is its alluring offer: affiliates stand to earn a remarkable 85% of the ransom proceeds, with the potential for further increases to an impressive 90% based on their progress.
The amalgamation of ‘the best’ aspects from existing Ransomware-as-a-Service (RaaS) platforms hints at Nevada Ransomware’s origin. Resecurity’s analysis suggests that this project may have roots in one of the now-defunct ransomware projects, resurrected under a new brand.
Notably, Nevada Ransomware appears to be intent on broadening its reach beyond the Russian-speaking realm. While the initial post introducing the ransomware was published in Russian, it also featured translations in both English and Chinese. However, it’s interesting to note that despite this outreach, the actors claimed not to work with English-speaking affiliates. Resecurity’s assessment, on the other hand, reveals a more inclusive approach, with affiliates hailing from diverse regions, including ex-USSR, the European Union, Islamic Republic of Iran, and China.
One distinguishing feature of Nevada Ransomware is its stringent vetting process for affiliates. Access to the affiliate panel, hosted on the TOR network, is only granted following a thorough evaluation. This meticulous selection process is implemented to ensure that affiliates are credible and pose no risk to the project’s security.
Once an affiliate gains access to the panel, they can initiate the process of creating a new victim. The operator is required to furnish essential victim details, including name, geography, and revenue, along with specifying the desired ransom amount. Victims are then listed in the panel, enabling further communication through a live chat interface.

This live chat feature, reminiscent of other notorious ransomware projects such as Blackhat, Lockbit, and Hive, is often used to exert pressure on victims, compelling them to pay the ransom. Each victim is allocated a dedicated workspace within the panel, streamlining communication and tracking.
The affiliate panel also provides comprehensive statistics on ransom payments, offering a clear overview of the project’s financial activities. This transparency ensures that both the operators and affiliates have insight into the progress of their illicit endeavors.
Nevada Ransomware exhibits a high degree of technical sophistication. The malware is available in both Windows and Linux versions. Notably, the Windows version is written in the Rust programming language, allowing execution via a console with predefined flags. Similarly, the Linux version leverages Rust and can be executed with several flags.
After successfully encrypting a victim’s data, Nevada Ransomware leaves behind a ‘readme.txt’ file in each affected folder. Interestingly, the ransomware includes exceptions during the encryption process. Folders containing at least one sub-folder named “nevada” are spared from encryption, illustrating a peculiar behavior in its targeting strategy. Additionally, files with extensions such as “.exe,” “.ini,” “.src,” and “.lnk” located within folders are not encrypted by default; they require the operator to specify a flag (“-file”) when executing Nevada Ransomware via a console.
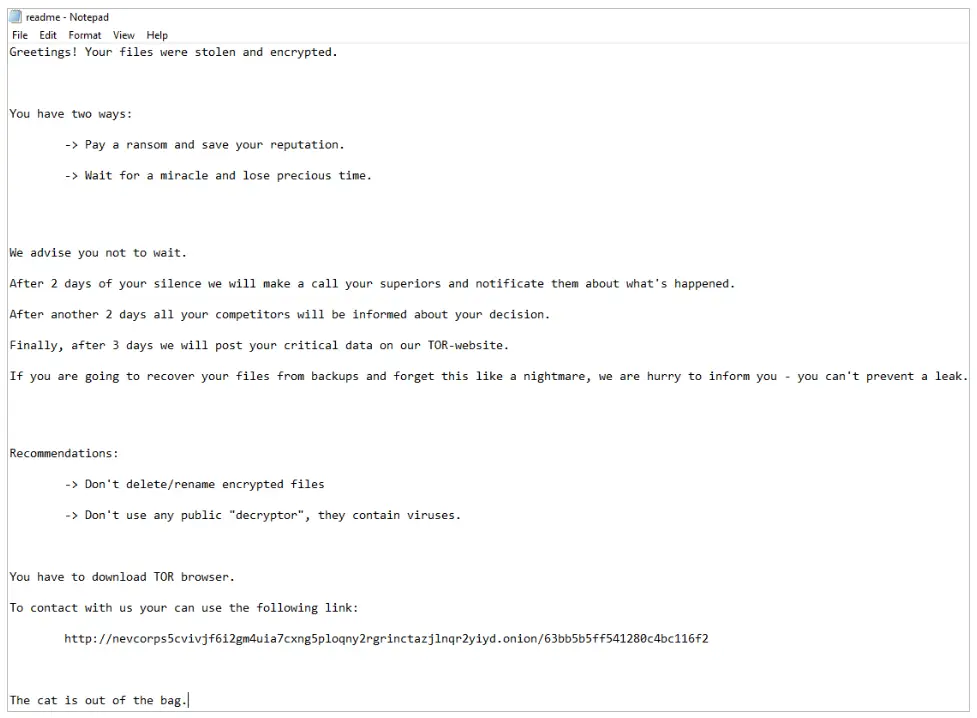
Nevada Ransomware has quickly risen through the ranks to become a prominent threat in the world of cybersecurity. Its enticing affiliate program, multilingual approach, and advanced technical capabilities make it a formidable adversary. The group behind Nevada Ransomware is not only developing ransomware but actively engaging in the acquisition of compromised access and post-exploitation activities, emphasizing the need for organizations to bolster their cybersecurity defenses.