According to the FortiGuard Threat Research and Response Lab, they recently captured a new malware sample that spreads through Microsoft Word documents. Initial investigation results show that this is a new variant of the spyware agent Tesla.
Agent Tesla was originally a simple keylogger, and researchers at network security company Zscaler stated in an analysis released in 2016 that it has officially become a complete spyware.
FortiGuard Labs captured another variant of Agent Tesla (based on the Microsoft .Net framework) in June 2017 and conducted a detailed analysis of it. At the time, researchers discovered that spyware was being spread through Microsoft Word documents containing malicious VBA macros that could be executed automatically. When the document is opened, the victim is prompted to click on the “Enable Content” button to display the content. Once clicked, spyware is automatically downloaded and installed invisible.
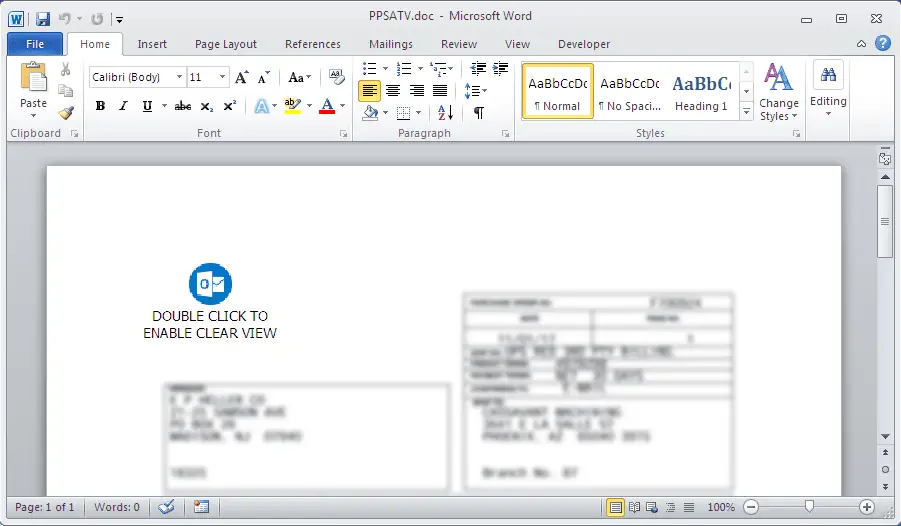
FortiGuard Labs stated that in recent activities, new variants have switched to being distributed through Microsoft Word documents that contain embedded exe files. When you open a document, everything except a blue icon is ambiguous. As you can see, it tells the victim through text that the “clear view” can be enabled by double-clicking the blue icon in the document. Once the victim is following this instruction, it will extract a “POM.exe” file from the embedded object into the infected system’s temporary folder and run it.

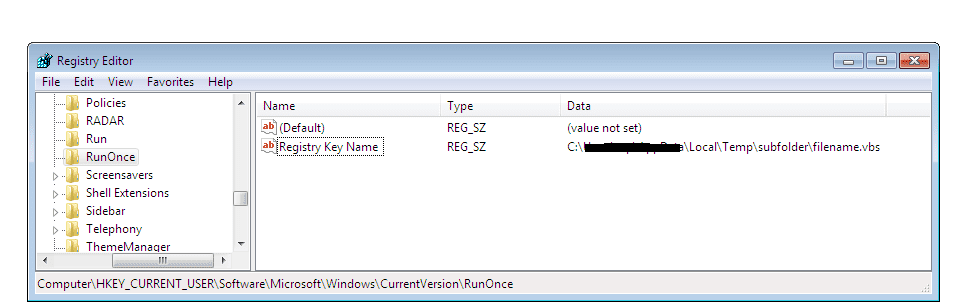
The FortiGuard Lab explains that POM.exe is written in MS Visual Basic and is an installer. At runtime, it puts two files (“filename.exe” and “filename.vbs”) in the “%temp%\subfolder” folder.
To establish persistence on infected systems, filename.vbs is first added to the system registry as a launcher. This action allows spyware to execute automatically each time the system is started.
FortiGuard Labs stated that the new variant has the same malicious features as the previously captured variants, including monitoring and collecting the victim’s keyboard input, system clipboard, victim screenshots, and collecting credentials for various installed software.
The difference is that the way data is submitted to the Command and Control (C&C) server has changed. The previous variant used HTTP POST to send the collected data, and the new variant has switched to using SMTPS to send the collected data to the attacker’s email address.
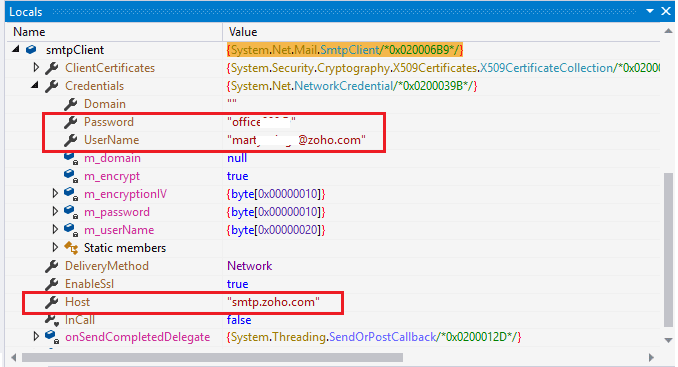
After an in-depth analysis, researchers at FortiGuard Labs discovered the SMTP credentials (“username” and “password”) and the SMTP server used by the attacker. This is a free Zoho e-mail account and the researcher immediately notified the e-mail service provider about this abuse.
Source, Image: Fortinet
