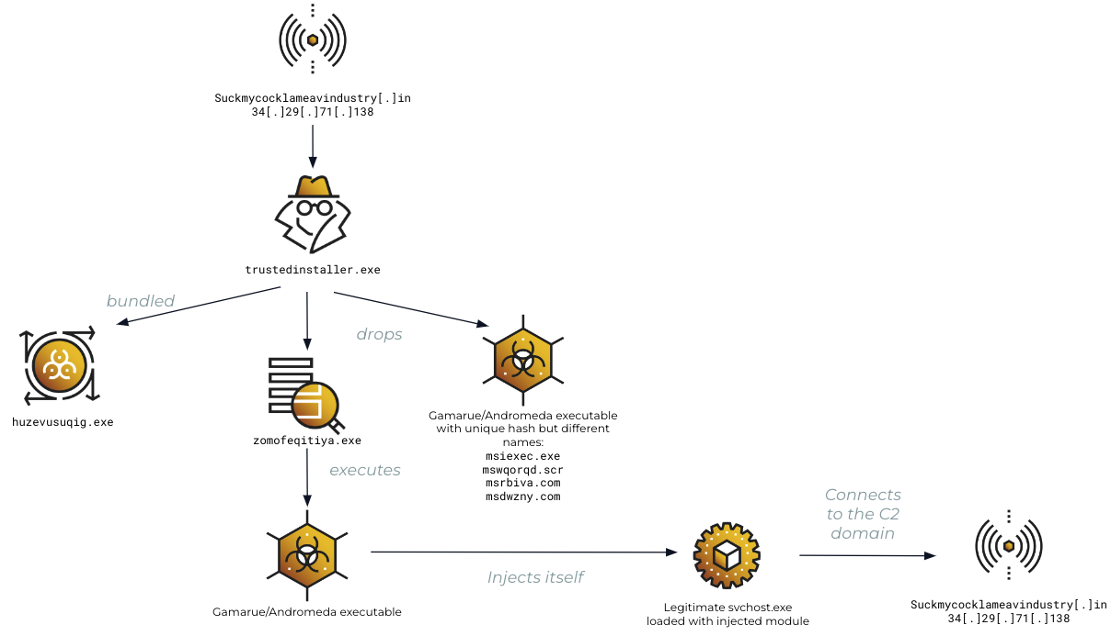
Graphical Flow of Attack Chain | Image: Cybereason
In a recent report, the Cybereason Security Services Team unveiled the discovery of a new cluster of Command-and-Control (C2) servers linked to the infamous Andromeda (aka Gamarue) malware family. This malware, active since at least 2011, is known for its modular design and adaptability, making it a versatile tool for cybercriminals. Cybereason’s latest findings reveal its targeted activities in the Asia-Pacific (APAC) region, with a focus on manufacturing and logistics industries.
Andromeda, historically distributed via malicious email attachments, infected USB drives, and secondary payloads, continues to evolve. “The backdoor has the capability to download and execute additional malware, steal sensitive information such as passwords, and create a backdoor for remote access,” Cybereason explained. This flexibility has made it a consistent choice for industrial espionage campaigns.
The report sheds light on the sophisticated methods employed by the threat actor. Initial infection vectors prominently include “USB drop attacks,” where compromised USB drives automatically execute malicious files upon connection. Once infected, rundll32.exe is utilized to load disguised DLLs—often named with patterns like ~$W*.USBDrv or ~$W*.FAT32.
A key finding highlights how “desktop.ini” files, often disguised as innocuous system files, serve as payloads to initiate the malware’s activities. These files are frequently downloaded via WebDAV exploitation, with network activity indicating connections to malicious domains registered with certificates under common names such as *.malware.com.
The new cluster of C2 servers showcases sophisticated infrastructure. One C2 domain, suckmycocklameavindustry[.]in, resolved to multiple IP addresses during Cybereason’s investigation. This adaptability enables dynamic command delivery, ensuring uninterrupted communication between the malware and its operators.
Cybereason’s team emphasized, “We determined that we had identified a cluster of IP addresses being used as C2 in conjunction with the Andromeda backdoor,” providing crucial insights into the operational reach of this threat.
The report identifies potential links to the notorious Turla group (aka UNC4210). “This particular campaign appears to repurpose an old Andromeda sample whose C2 was hijacked by UNC4210,” the report noted, with connections to previous malicious domains and activities observed.
This campaign focuses on disrupting manufacturing and logistics companies in the APAC region, with industrial espionage as the suspected motive. The attackers leverage Andromeda’s modular design to infiltrate networks, exfiltrate sensitive data, and execute further payloads.
Related Posts:
- Cybereason Uncovers Widespread Exploitation of Apache ActiveMQ Vulnerability
- Cuckoo Spear Threat Alert: APT10 Targets Japan’s Critical Infrastructure
- Cybereason found new malware, Fauxpersky that disguised as Kaspersky anti-virus software