TA473 CSRF infection diagram
Researchers from Proofpoint have discovered a newly identified advanced persistent threat (APT) actor, TA473, exploiting the Zimbra vulnerability CVE-2022-27926 to target military, government, and diplomatic organizations in Europe involved in the Russia-Ukraine War. The threat group, also known as Winter Vivern, uses scanning tools like Acunetix to find unpatched webmail portals and deliver phishing emails with malicious URLs, which execute JavaScript payloads within the victims’ webmail portals.
TA473, which has been tracked by Proofpoint since 2021, has historically focused on European government, military, and diplomatic entities through phishing campaigns that deliver PowerShell and JavaScript payloads. However, the group expanded its targets in late 2022 to include elected officials and staffers in the United States.

Proofpoint observed an evolution in TA473’s phishing campaigns since 2021, with the threat actor employing opportunistic exploits and various phishing techniques, often originating from compromised email addresses.
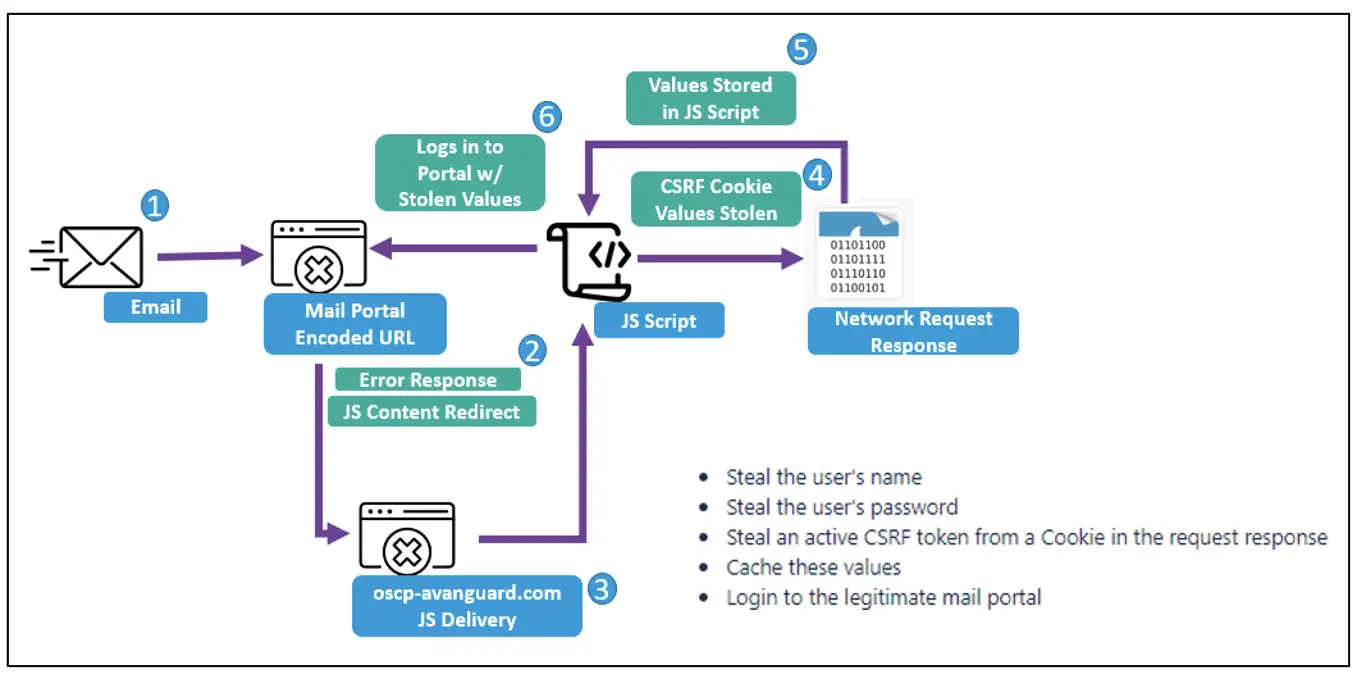
Beginning in early 2023, TA473 started exploiting the Zimbra vulnerability CVE-2022-27926 in phishing campaigns targeting European government entities. This vulnerability affects Zimbra Collaboration Suite version 9.0.0, which is used for hosting publicly facing webmail portals. By exploiting this vulnerability, TA473 can execute arbitrary web script or HTML via request parameters, which allows them to steal usernames, passwords, and active session and CSRF tokens from cookies.
Proofpoint researchers have identified several instances of customized CSRF JavaScript payloads delivered through the exploitation of CVE-2022-27926. The payloads are executed by servers hosting vulnerable webmail instances and often use multiple layers of Base64 encoding to obfuscate the functionality of the JavaScript. Once decoded, these payloads reveal the malicious intent, such as stealing usernames, passwords, CSRF tokens, and attempting to log in to legitimate mail portals using the stolen credentials.
“Proofpoint researchers strongly recommend patching all versions of Zimbra Collaboration used in publicly facing webmail portals, especially among European government entities. Additionally, restricting resources on publicly facing webmail portals from the public internet is highly recommended to prevent groups like TA473 from reconning and engineering custom scripts capable of stealing credentials and logging in to users’ webmail accounts,” the researcher wrote.