New Attack Vector: Misconfigured Jupyter Servers Targeted for Illegal Streaming

Aqua Nautilus security researchers have uncovered a novel attack vector where threat actors exploit misconfigured servers, particularly JupyterLab and Jupyter Notebook environments, to hijack computing resources for illegal live sports streaming. This attack targets vulnerable development environments, capturing and redirecting live broadcasts to unauthorized platforms for profit.
The attackers utilize misconfigured Jupyter servers, often exposed to the internet without authentication, to gain unauthorized access. According to the report: “Threat actors exploited unauthenticated access to Jupyter Lab and Jupyter Notebook to establish initial access and achieve remote code execution.”
The attackers then deploy ffmpeg, a widely-used multimedia processing tool, to capture live sports broadcasts and redirect them to illicit streaming platforms. This technique, known as stream ripping, bypasses detection by masking the activity as benign server operations.
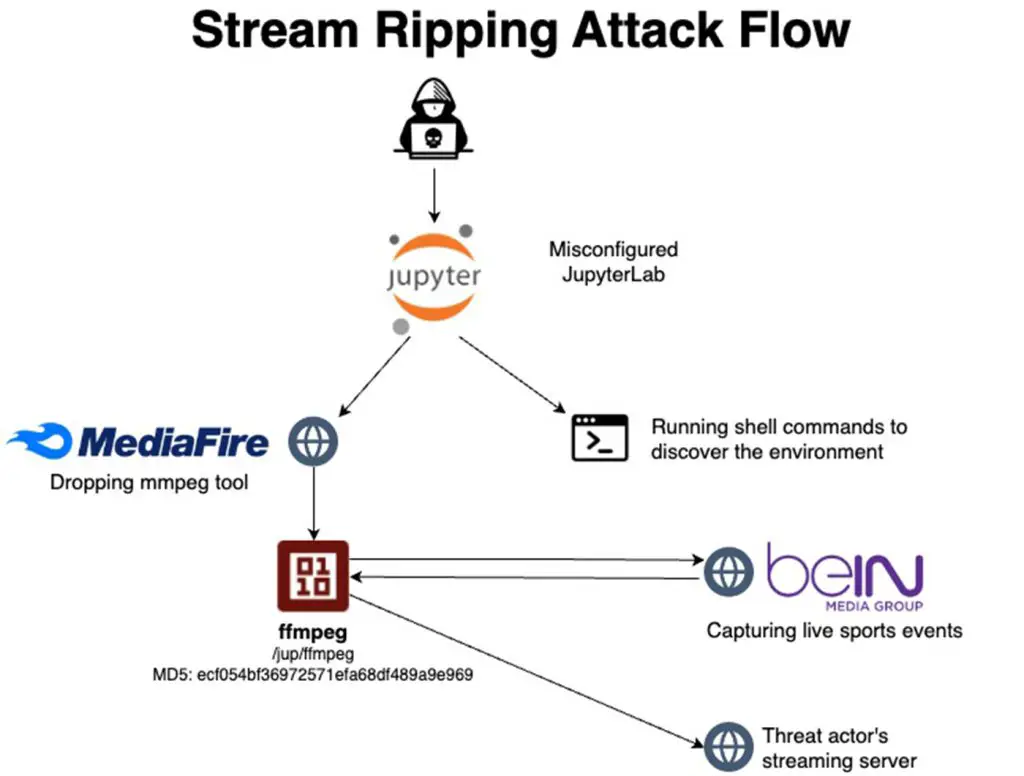
The entire attack flow | Image: Aqua Nautilus
Live sports streaming piracy is a growing threat to the entertainment industry, affecting broadcasters, sports leagues, and teams. Aqua Nautilus highlights: “Unauthorized broadcasts have become widespread, impacting not only big leagues but also smaller teams that rely on paid viewership.” This results in significant revenue losses and damages to legitimate platforms.
In this specific case, attackers targeted the Qatari beIN Sports network, capturing broadcasts of UEFA Champions League matches and redirecting them to external platforms such as ustream.tv. These platforms generate income through ad revenue and paid subscriptions, which the threat actors exploit for illicit financial gain.
JupyterLab and Jupyter Notebooks are popular tools for data science but are prone to misconfigurations that expose them to attacks. Key vulnerabilities include:
- Open Access: Servers connected to the internet without authentication.
- Token Mismanagement: Exposed tokens granting unauthorized access.
- Lack of Firewalls: Absence of network restrictions, leaving environments unprotected
According to Aqua Nautilus, approximately 15,000 Jupyter servers are exposed to the internet, with around 1% enabling remote code execution.
The researchers used their honeypot network and tools like Aqua Tracee and Traceeshark to analyze the attack. Traceeshark enabled detailed examination of over 8,000 events, revealing suspicious patterns such as repetitive ffmpeg executions and unusual IP activity. “The situation becomes suspicious when observing the process tree suggesting of numerous ffmpeg execution commands, especially with the unusual pattern of IP addresses involved,” the researchers noted.
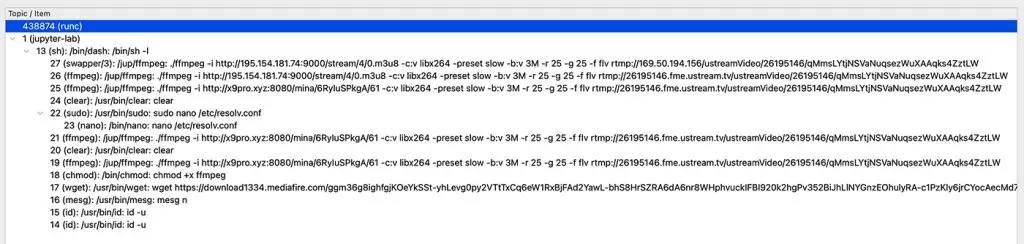
Traceeshark’s process tree | Image: Aqua Nautilus
The investigation revealed that the attackers downloaded ffmpeg from unverified sources and configured it to capture live streams discreetly. By tracing the commands, Aqua Nautilus identified ustream.tv as the final destination for these illegal broadcasts
While the immediate damage of such attacks might seem limited to the entertainment sector, Aqua Nautilus warns of broader risks: “the attackers gained access to a server intended for data analysis, which could have serious consequences for any organization’s operations. Potential risks include denial of service, data manipulation, data theft, corruption of AI and ML processes, lateral movement to more critical environments and, in the worst-case scenario, substantial financial and reputational damage.”
To mitigate these risks, Aqua Nautilus recommends:
- Secure Configuration: Use strong authentication, restricted IPs, HTTPS, and proper token management for Jupyter servers.
- Regular Updates: Ensure all servers and tools are updated to patch vulnerabilities.
- Network Monitoring: Deploy tools like Aqua Tracee to detect unusual activities in real-time





