According to the Network Security Research Lab at 360 disclosed on March 15, a new type of backdoor is targeting Linux systems through a Log4J vulnerability, capable of incorporating targeted devices into botnets and acting as a tunnel to download and install rootkits.

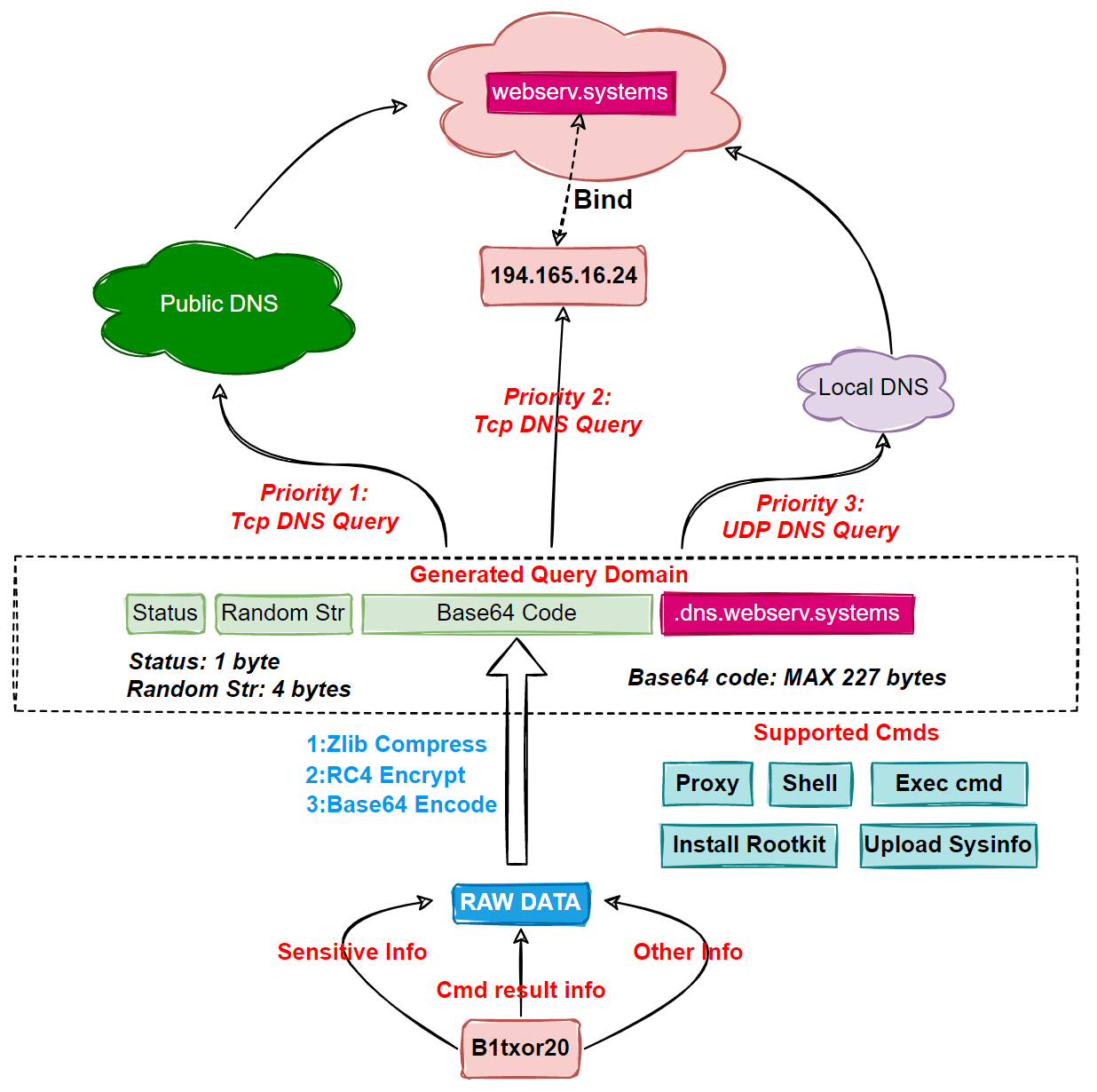
According to reports, on February 9, 360Netlab’s honeypot system captured an unknown ELF file spread through the Log4J vulnerability. The network traffic generated by this file triggered DNS tunnel alerts in the system, and upon inspection, it was determined to be a brand new family of botnets. The security team named it B1txor20 based on its use of the filename “b1t”, the XOR encryption algorithm, and the 20-byte RC4 algorithm key length.
B1txor20 uses a technique called DNS Tunnel to establish a communication channel with the C2 server by encoding data in DNS queries and responses. Although many developed features are not put into use (in IDA, there is no cross-reference); some features have bugs, the ability to get a shell, execute arbitrary commands, install rootkits, open SOCKS5 proxies, and upload sensitive information back to the C2 server is currently supported by B1txor20 Linux backdoor. Once the device is successfully compromised, the B1txor20 Linux backdoor utilizes the DNS tunnel to retrieve and execute commands sent by the server.
The researchers also found that some developed features were not enabled, therefore, it is guessed that the developers of B1txor20 will continue to improve and open different functions according to different application scenarios.