
Kaspersky researchers have discovered a new campaign by the Awaken Likho APT group, also known as Core Werewolf, which has been active since at least July 2021. The group is known to target Russian government agencies and industrial enterprises. This latest campaign, which began in June 2024, shows that the attackers have changed their software and techniques.
Previously, Awaken Likho leveraged the UltraVNC module for remote access, but their latest operations show a shift towards using MeshAgent, an agent for the legitimate MeshCentral platform. MeshCentral is an open-source solution designed for remote device management, but in the hands of these attackers, it becomes a potent weapon for gaining unauthorized control over compromised systems.
According to Kaspersky, “the attackers had significantly changed the software they used in their attacks. The attackers now prefer using the agent for the legitimate MeshCentral platform instead of the UltraVNC module.” This pivot marks a critical change in how the APT group operates, making their attacks harder to detect and mitigate.
During their investigation, Kaspersky’s team discovered a new implant delivered through phishing emails, a hallmark technique of Awaken Likho. Though they were unable to retrieve the original phishing emails, prior attacks suggest the use of self-extracting archives (SFX) and malicious modules to deliver the payload.
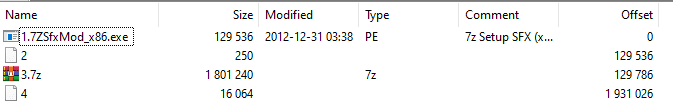
The implant analyzed was distributed in a SFX created using 7-Zip. As Kaspersky explained, “the archive contains five files, four of which are disguised as legitimate system services and command files.” These decoy files serve to mislead victims while the real payload works silently in the background.
Once extracted, the implant runs MicrosoftStores.exe, a file packed with a compiled AutoIt script. After deobfuscating this script, Kaspersky’s experts discovered it launches two key components: NetworkDrivers.exe, which is the MeshAgent, and nKka9a82kjn8KJHA9.cmd, a heavily obfuscated command file.
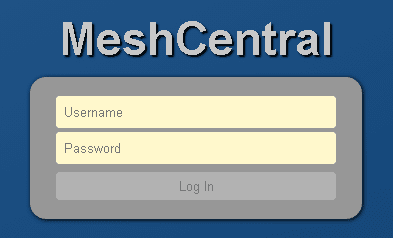
The ultimate goal of the implant is persistence. By creating a scheduled task named MicrosoftEdgeUpdateTaskMachineMS, the attackers ensure that MeshAgent reconnects to the command-and-control (C2) server. The server connection is established using the WebSocket protocol, as confirmed when “opening this address via HTTPS revealed the login form for the MeshCentral platform.”
The primary targets of this campaign remain consistent with previous Awaken Likho activities—Russian government agencies, contractors, and industrial enterprises. Based on the tactics, techniques, and procedures (TTPs) employed, Kaspersky attributes this campaign with high confidence to the Awaken Likho group.
The timing of these attacks, which began shortly after the start of the Russo-Ukrainian conflict, underscores the group’s political motivations. “Awaken Likho is one of the threat actors that ramped up its activity after the start of the Russo-Ukrainian conflict,” Kaspersky noted.
Organizations, especially those within the Russian government and industrial sectors, must remain vigilant as this APT group continues to refine its arsenal.
Related Posts:
- Kaspersky Uncovers 10,000 Cyberattacks: Global Organizations Targeted
- Kaspersky Report: Energy Industry becomes the largest area affected by vulnerabilities in industrial automation systems
- Kaspersky Report: Criminals earning millions through mining malware