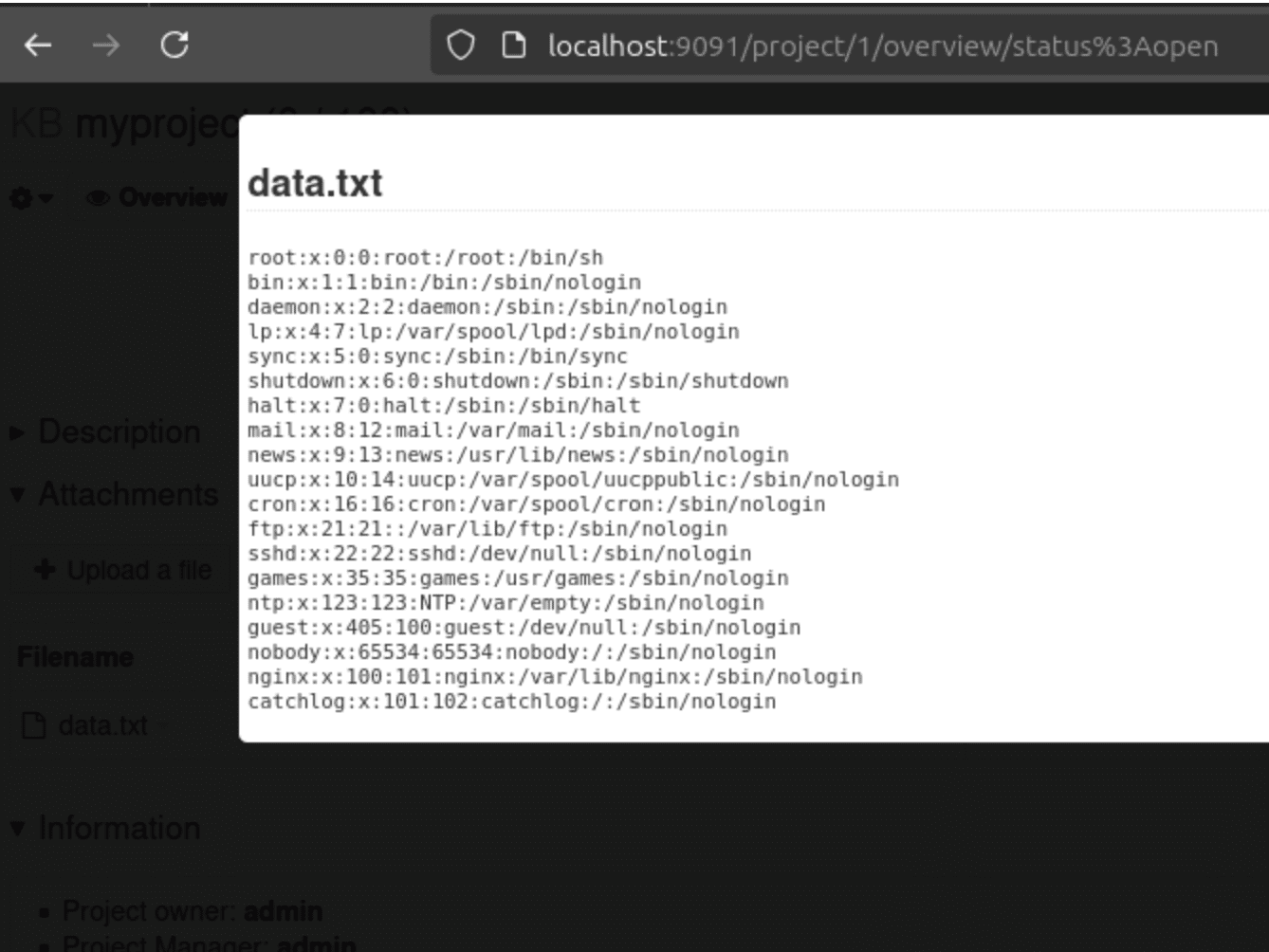
Two severe vulnerabilities have been discovered in Kanboard, a project management software that adheres to the Kanban methodology. Both vulnerabilities, identified by Deutsche Telekom Security GmbH, pose significant threats to servers running affected Kanboard versions, allowing authenticated administrators to read, delete, and execute arbitrary code on the server.
The first vulnerability, CVE-2024-51747 (CVSS 9.1), allows an authenticated attacker with administrative privileges to read and delete arbitrary files on the server. This vulnerability arises from insufficient sanitization of file paths, enabling attackers to exploit path traversal techniques.
The second vulnerability, CVE-2024-51748 (CVSS 9.1), allows an authenticated attacker with administrative privileges to execute arbitrary PHP code on the server. This vulnerability stems from improper handling of language settings, allowing attackers to inject malicious code into the application.
Kanboard users are strongly encouraged to upgrade to version 1.2.42, which addresses these vulnerabilities by sanitizing path entries and applying stricter validation to the application_language setting. Additionally, administrators should limit access to the Kanboard server and monitor logs for any unusual activity related to file manipulation or unauthorized language setting changes.
Related Posts:
- Microsoft reveals some details of the Russian hacking group’s attack on Ukraine
- SAP Patches Multiple Vulnerabilities in November 2024 Security Patch Day
- CVE-2024-11068 (CVSS 9.8): Critical D-Link DSL-6740C Flaw, Immediate Replacement Advised
- Dell Enterprise SONIC OS Patches Critical Security Vulnerabilities