Last week’s report mentioned a new high-profile persistent threat organization called Dark Caracal, which is launching a global mobile spyware offensive. It mentions CrossRAT (version 0.1) cross-platform malware, a remotely controlled trojan that infects all current operating systems in the world, including Windows, Solaris, Linux, and MacOS. Hackers can remotely modify the computer’s file system, screenshots, run executable files and other operations.
According to the current findings, the organization’s hackers did not use known zero-day vulnerabilities to spread the malware but instead used the most basic social engineering methods to send links in social networking sites and web chat tools to lure users to open fake websites download malicious programs. CrossRAT is written in Java and allows engineers and researchers to decompile it.

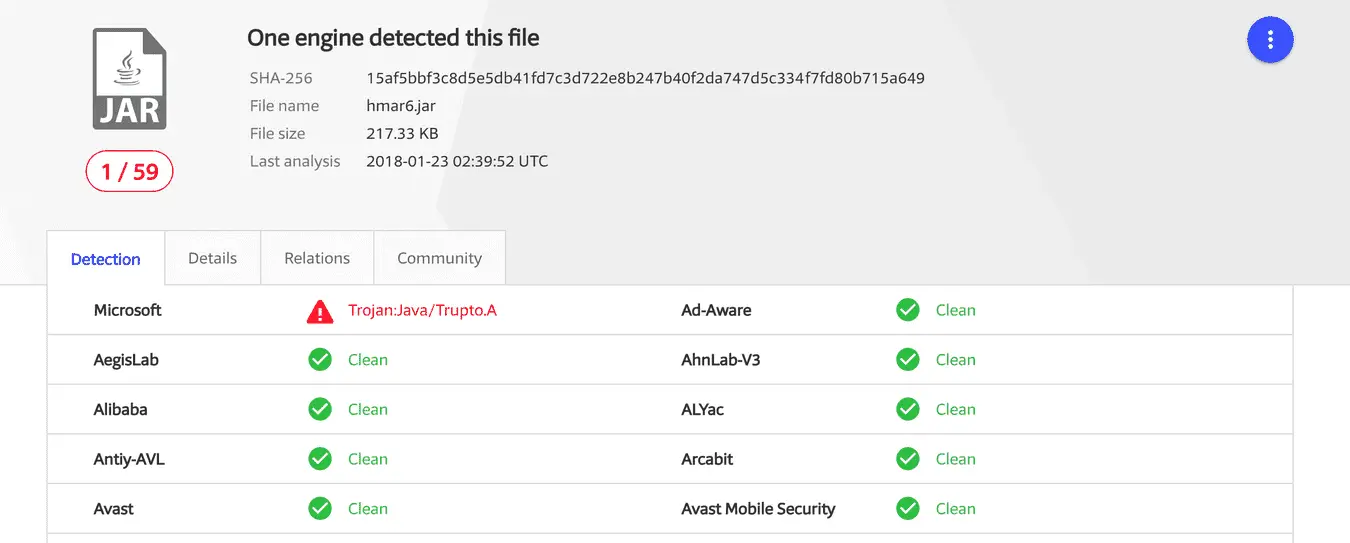
As of press time, only one out of 59 antivirus programs identified CrossRAT malware, and former NSA hacker Patrick Wardle was prepared to analyze its code and explain how it works. Once run on the target host, hmar6.jar file first determine the host operating system, and then run the appropriate procedures based on the operating system, while installing the operating system version of the phone host, the kernel version, and architecture. For different Linux systems, it will also analyze the different versions of the system file differences to determine what version of Linux. For Mac OS, it reconnects to the remote command server after each system reboot, and can then send related commands and data.
According to researchers, checks in with the C&C server for tasking. As noted the EFF/Lookout report the malware will connect to flexberry.com on port 2223, with the core information in the crossrat/k.class file and can not be modified.

CrossRAT includes some basic monitoring tools, only need to issue a command to the remote server to start the monitoring function. Patrick also found that although the open source Java library jnativehook was used in the CrossRAT program to record keyboard and mouse behavior, there was no preset command to start the keyboard recorder inside CrossRAT. This means CrossRAT is likely to be updated later to add more functionality.
How can I tell if I’m infected with CrossRAT?
A: First check to see if there is an instance of Java is running, that’s executing
mediamgrs.jar.On macOS or Linux use the ‘ps’ command:
$ ps aux | grep mediamgrs.jar user 01:51AM /usr/bin/java -jar /Users/user/Library/mediamgrs.jarOne can also look for the persistent artifacts of the malware. However, as the malware persists in an OS-specific manner, detecting this will depend what OS you’re running.
- Windows:
- Check the
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\registry key.- If infected it will contain a command that includes,
java,-jarandmediamgrs.jar.- Mac:
- Check for jar file,
mediamgrs.jar, in~/Library.- Also look for launch agent in
/Library/LaunchAgentsor~/Library/LaunchAgentsnamedmediamgrs.plist.- Linux:
- Check for jar file,
mediamgrs.jar, in/usr/var.- Also look for an
'autostart'file in the~/.config/autostartlikely namedmediamgrs.desktop.How can I protect myself from an infection?
As CrossRAT is written in Java, it requires Java to be installed. Luckily recent versions of macOS do not ship with Java. Thus, most macOS users should be safe! Of course if a Mac user already has Java installed, or the attacker is able to coerce a naive user to install Java first, CrossRAT will run just dandy, even on the latest version of macOS (High Sierra).
It is also worth noting that currently AV detections seem rather non-existent (1⁄59 on Virus Total). Thus having anti-virus software installed likely won’t prevent or detect a CrossRAT infection. However tools that instead detect suspicious behaviors, such as persistence, can help!
Source: digitasecurity