
Malicious website serving D3F@ck Loader
In a recently released analysis, eSentire’s Threat Response Unit (TRU) has uncovered a sophisticated new malware distribution campaign dubbed the D3F@ck Loader. This insidious threat is changing the cybersecurity landscape with its ability to bypass common security defenses, including Google Chrome, Microsoft Edge, Windows Defender, and SmartScreen.
How D3F@ck Loader Works
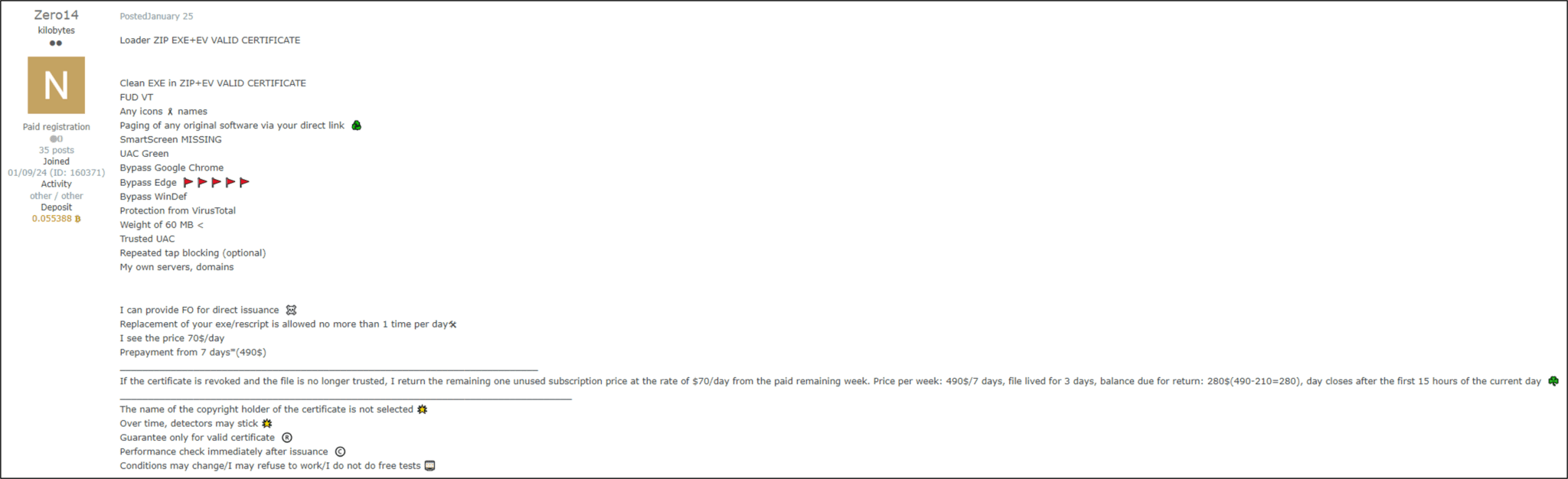
The D3F@ck Loader takes the “Malware-as-a-Service” (MaaS) model to a new level. Cybercriminals can purchase access to the loader for as little as $70 a day, granting them the ability to deliver dangerous malware payloads directly to unsuspecting victims.
The infection process often begins with malicious advertisements on Google Ads, mimicking legitimate software like Calendly or Rufus. Once a user clicks the ad, they are redirected to a fake website where the D3F@ck Loader is downloaded.

Critically, the loader abuses trusted Extended Validation (EV) certificates. These certificates, intended to signify the highest level of identity authentication, trick security software into believing the malware is a legitimate program.
Technical Insights
eSentire’s analysis reveals that the current version of D3F@ck Loader utilizes Inno Setup, a popular script-driven installation system, to create Windows installers. The loader exploits the Pascal scripting engine integrated within Inno Setup, using it to execute complex commands that install further malicious software, such as Raccoon Stealer and Danabot.
The loader operates by creating and executing batch scripts that manage the download and execution of additional payloads. These scripts are adept at avoiding detection, employing techniques to hide their actions from the user and bypass security checks. For instance, they manipulate command echoing and file visibility and even modify system settings to prevent security tools from interfering with the malware’s operation.
Case Analysis and Malicious Activities
In a specific case analyzed by TRU, the loader dropped a batch file named “performed.cmd” in the system’s temp directory, which fetched a URL using Curl and deleted itself after executing to cover its tracks. This script demonstrated the loader’s ability to control infected machines remotely, directing them to download further malicious payloads from a command and control (C2) server.
The sophistication of the D3F@ck Loader extends to its management of these payloads. It retrieves a .NET dropper from the C2 server, which then injects Raccoon Stealer into the RegAsm.exe process, a legitimate Windows component. This method allows the malware to operate under the guise of legitimate system processes, further complicating detection and removal.
Security Implications and Responses
The use of EV certificates by D3F@ck Loader represents a significant challenge for cybersecurity defenses. These certificates, which are supposed to guarantee a higher level of security, are being exploited by attackers to gain unwarranted trust from security systems and facilitate the spread of malware.
In response to these threats, eSentire’s TRU has successfully identified and reported malicious EV signatures associated with the loader, leading to their revocation. However, the continuous adaptation of threat tactics underscores the need for vigilant, advanced security measures and ongoing public awareness.