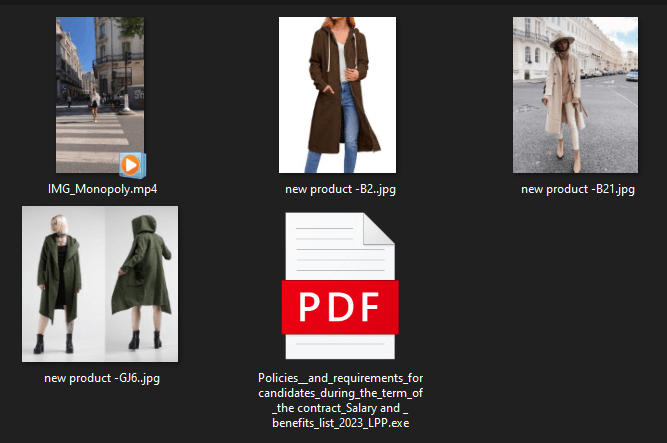
The contents of the malicious archive
Ducktail is a malware family that has been active since the second half of 2021 and aims to steal Facebook business accounts. According to security researchers from Kaspkery, in a recent campaign that ran between March and early October 2023, the attackers targeted marketing professionals using a new Delphi-based executable disguised as a PDF file.
The campaign began with the attackers sending out an archive containing images of new products by bona fide companies along with the malicious executable. When started, the malware would open a real, embedded PDF file that contained the job details. The attack was tailored to target marketing professionals looking for a career change.

The malware would then install a browser extension capable of stealing Facebook business and ads accounts. The extension disguised itself with the Google Docs Offline icon and description text and used a directory path that is used by the bona fide extension NordVPN.
The core exception script of the extension was obfuscated, but it was determined that it constantly sends the details of all open browser tabs to a command-and-control (C&C) server. If it detects Facebook-related URLs, it checks for ads and business accounts to try and steal them. In particular, the extension snatches cookies and details of accounts that the victim is signed in to on the device.
To bypass two-factor authentication, the extension uses Facebook API requests and a Vietnamese service that offers various auxiliaries for generating one-time access codes. This is probably how the hackers log in after the user’s authentication session has expired. Stolen credentials and cookies are forwarded to a C&C server registered in Vietnam.
In addition to the main script, the malware would save a corrupted version of the core script from prior attacks to the extension folder.
According to Kaspersky Labs, cybercriminals most often attacked users in India, but infection attempts were also stopped on devices of users in Kazakhstan, Ukraine, Germany, Portugal, Ireland, Greece, Jordan, Pakistan, Vietnam, UAE, USA, Peru, and Chile.
There are a few things you can do to protect yourself from Ducktail malware:
- Be careful about what emails you open and what attachments you download. If you receive an email from someone you don’t know, or if the email contains an attachment that you weren’t expecting, don’t open it.
- Keep your software up to date. Software updates often include security patches that can help protect your device from malware.
- Use a strong antivirus program and keep it up to date. Antivirus programs can help detect and remove malware from your device.
- Be careful about what websites you visit and what links you click on. Some websites may contain malicious code that can infect your device with malware.