Netskope Threat Labs has uncovered a new malicious campaign that employs deceptive tactics to distribute the LegionLoader malware. This campaign leverages fake CAPTCHAs and CloudFlare Turnstile to trick victims into downloading malware, which ultimately leads to the installation of a malicious browser extension.
Since February 2025, Netskope Threat Labs has been monitoring various phishing and malware campaigns targeting users searching for PDF documents online. Attackers often use deceptive methods within these PDFs to redirect victims to malicious websites or induce them to download malware. In this newly discovered campaign, the attackers use fake CAPTCHAs and CloudFlare Turnstile as part of their strategy to deliver the LegionLoader payload.
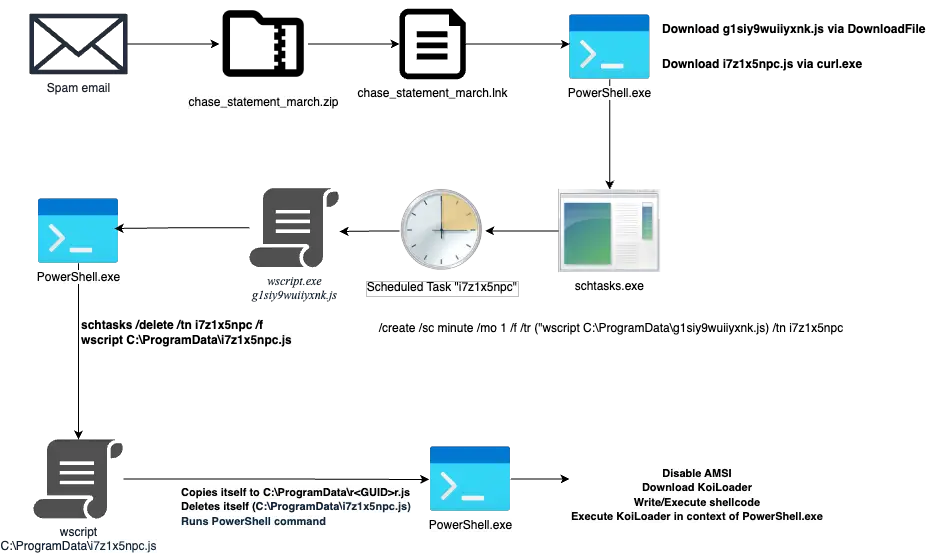
The infection chain involves several key steps:
- The initial infection starts with a drive-by download when a victim searches for a specific document and is lured to a malicious website.
- The downloaded document contains a fake CAPTCHA, which, when clicked, redirects the victim through a Cloudflare Turnstile CAPTCHA to a notification page.
- Victims are then prompted to enable browser notifications to proceed.
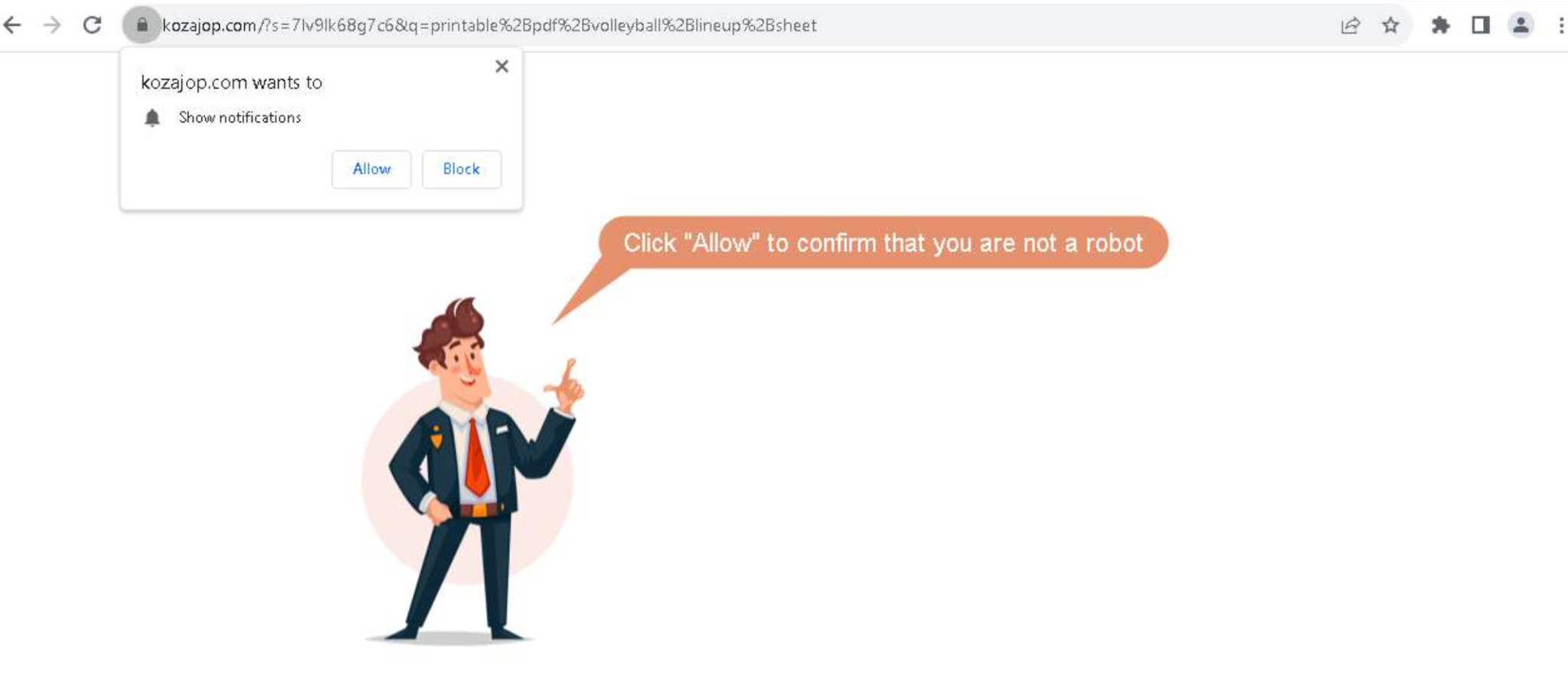
Malicious page requesting enablement of notification | Image: Netskope Threat Labs
If a victim blocks the browser notification request or uses a browser that doesn’t support notifications, they are redirected to download benign applications like 7-Zip and Opera. However, if the victim consents to receive browser notifications, they are redirected to a second Cloudflare Turnstile CAPTCHA. After completing this, they are directed to a page with instructions on how to download their intended document.
This download process involves having the victim open the Windows Run window, paste a command (copied to the clipboard) using Ctrl+V, and execute it. The command uses the command prompt to run cURL and download an MSI file, subsequently opening File Explorer to where the MSI file was downloaded. Running this MSI file executes the initial payload.
The attackers employ various techniques to evade detection:
- The infection chain uses a legitimate VMware-signed application that sideloads a malicious DLL to load and execute the LegionLoader payload.
- A new custom algorithm is used to deobfuscate the LegionLoader shellcode loader.
- The attacker’s website requires the use of cURL to download the MSI installer, and accessing the URL via a browser returns a message indicating the file was deleted due to service rule violations.
The final stage of the attack involves installing a malicious browser extension. This extension is capable of stealing sensitive user and computer information across multiple browsers, including Chrome, Edge, Brave, and Opera.
The report states that “The attacks have targeted more than 140 Netskope customers located mainly in North America, Asia, and Southern Europe across different segments, led by the technology and financial services sectors.”
The report concludes that attackers are actively targeting victims searching for PDF documents online and are using sophisticated techniques to deliver malware.