Trend Micro malware researchers found new KillDisk malware variants.This is called TROJ_KILLDISK.IUB that targets financial organizations in Latin America. “It may be a component of another payload or part of a bigger attack. We are still analyzing this new KillDisk variant and we will update this post as we uncover more details about this threat.”
TrendMicro said:
“We came across a new variant of the disk-wiping KillDisk targeting financial organizations in Latin America.” reads a preliminary analysis published by TrendMicro.
“Because KillDisk overwrites and deletes files (and doesn’t store the encryption keys on disk or online), recovering the scrambled files was out of the question.”
December 2015, KillDisk malware and ICS-SCADA malware BlackEnergy used in Ukraine attacks on, eventually leading to power outages. Also used in the same period as mining companies in Ukraine, railways, and banks. The malware was later included in other malicious code, including Petya ransomware.
December 2016, security firm Cyber X researchers have discovered a new variant of the malware variants can be implemented KillDisk ransomware function. The goal of this latest variation is to delete any files stored on the Windows machine, except system files and folders.
Trend Micro claims:
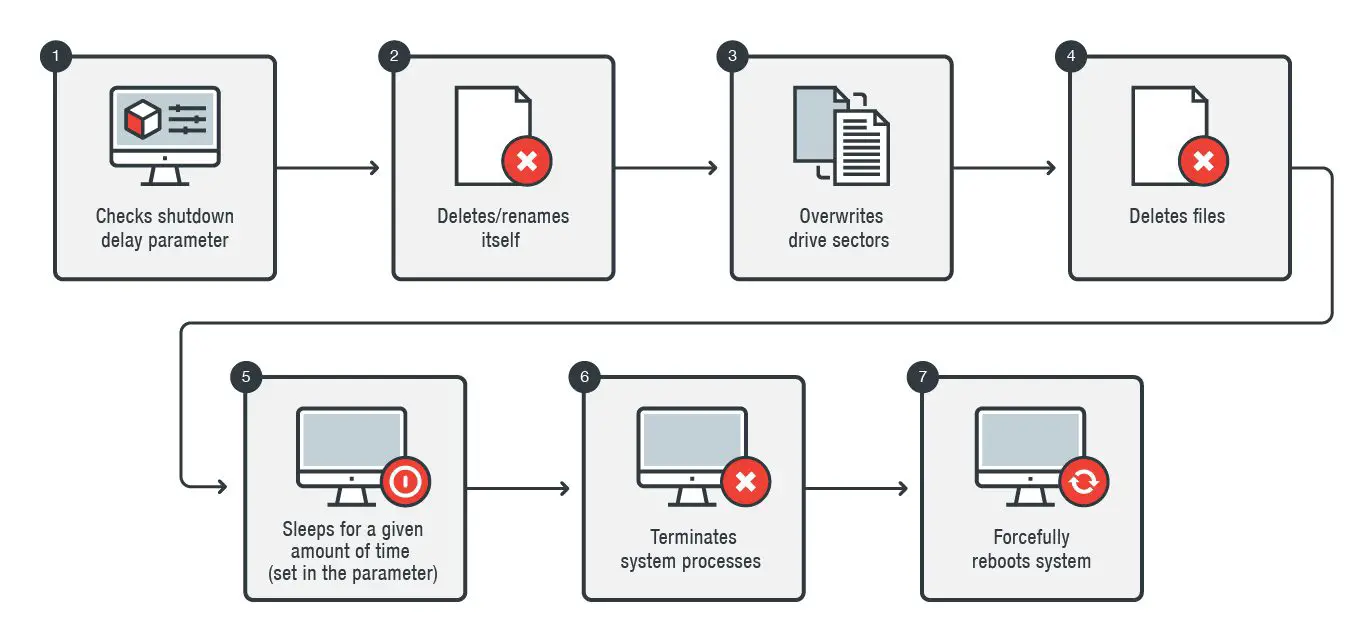
“The malware attempts to wipe \\.\PhysicalDrive0 to \\.\PhysicalDrive4. It reads the Master Boot Record (MBR) of every device it successfully opens and proceeds to overwrite the first 0x20 sectors of the device with “0x00”. It uses the information from the MBR to do further damage to the partitions it lists.” states Trend Micro. “If the partition it finds is not an extended one, it overwrites the first 0x10 and last sectors of the actual volume. If it finds an extended partition, it will overwrite the Extended Boot Record (EBR) along with the two extra partitions it points to.”
Once the malware deletes and overwrites the files and folders, it will try to terminate multiple processes to force a reboot of the computer. The goals of malware processing are:
- Client/server run-time subsystem (csrss.exe)
- Windows Start-Up Application (wininit.exe)
- Windows Logon Application (winlogon.exe)
- Local Security Authority Subsystem Service (lsass.exe)
Reference & Source: securityaffairs, TrendMicro