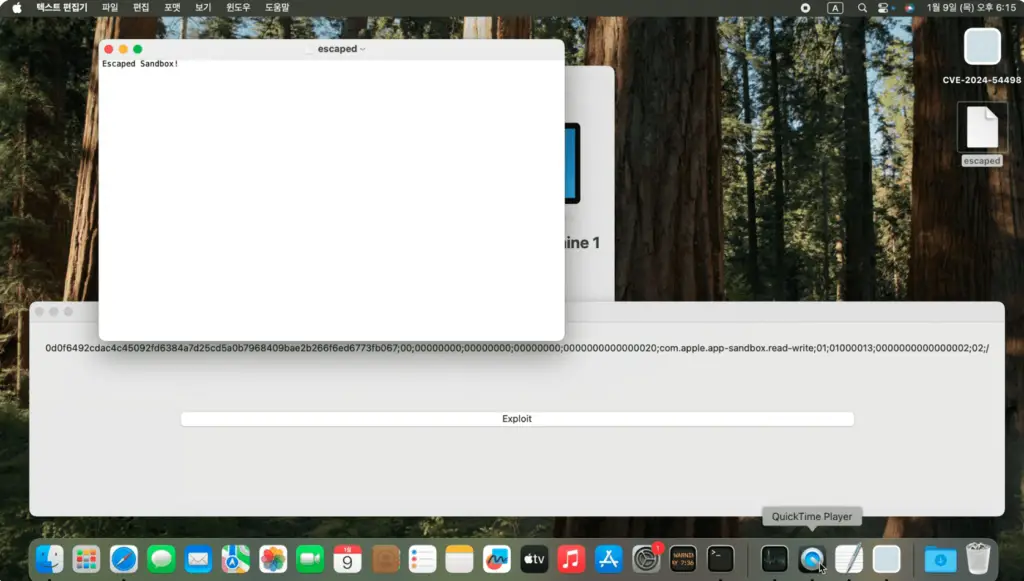
Recently, security researcher @wh1te4ever has revealed a proof of concept (PoC) exploit for CVE-2024-54498, a vulnerability that allows applications to escape the confines of the macOS Sandbox. The PoC, published on GitHub, demonstrates how malicious actors could leverage this flaw to gain unauthorized access to sensitive user data.
The macOS Sandbox is a critical security feature that restricts applications from accessing or modifying files and resources outside their designated area. This safeguard protects users from malicious software that might attempt to steal personal information, corrupt system files, or install malware. However, the CVE-2024-54498 vulnerability, with a CVSS score of 8.8 (High severity), allows applications to bypass these restrictions, effectively granting them free rein over the user’s system.
According to @wh1te4ever, the exploit utilizes the sharedfilelistd process to break out of the Sandbox. A video demonstration showcasing the exploit in action was also shared on YouTube, highlighting the potential risk to users who have not updated their systems.
Apple has addressed this vulnerability in the following updates:
- macOS Sequoia 15.2
- macOS Ventura 13.7.2
- macOS Sonoma 14.7.2
Users are strongly urged to update their macOS systems to the latest versions immediately to mitigate the risk posed by this vulnerability. Delaying updates could leave systems vulnerable to attacks that exploit CVE-2024-54498, potentially leading to data breaches and system compromise.
While publishing PoCs can help researchers and organizations better understand and mitigate vulnerabilities, it also provides a roadmap for malicious actors to exploit the issue.
Related Posts:
- BlueNoroff’s New MacOS Threat: “Hidden Risk” Targets Crypto Enthusiasts
- Pig-Butchering Scams: A Rising Threat to Investors in India and Globally
- Three 0-Day Vulnerabilities in Apple Products
- Windows Sandbox Gets Supercharged: Clipboard and File Sharing Arrive