New Malware Duo Bulbature and GobRAT Target Edge Devices Worldwide
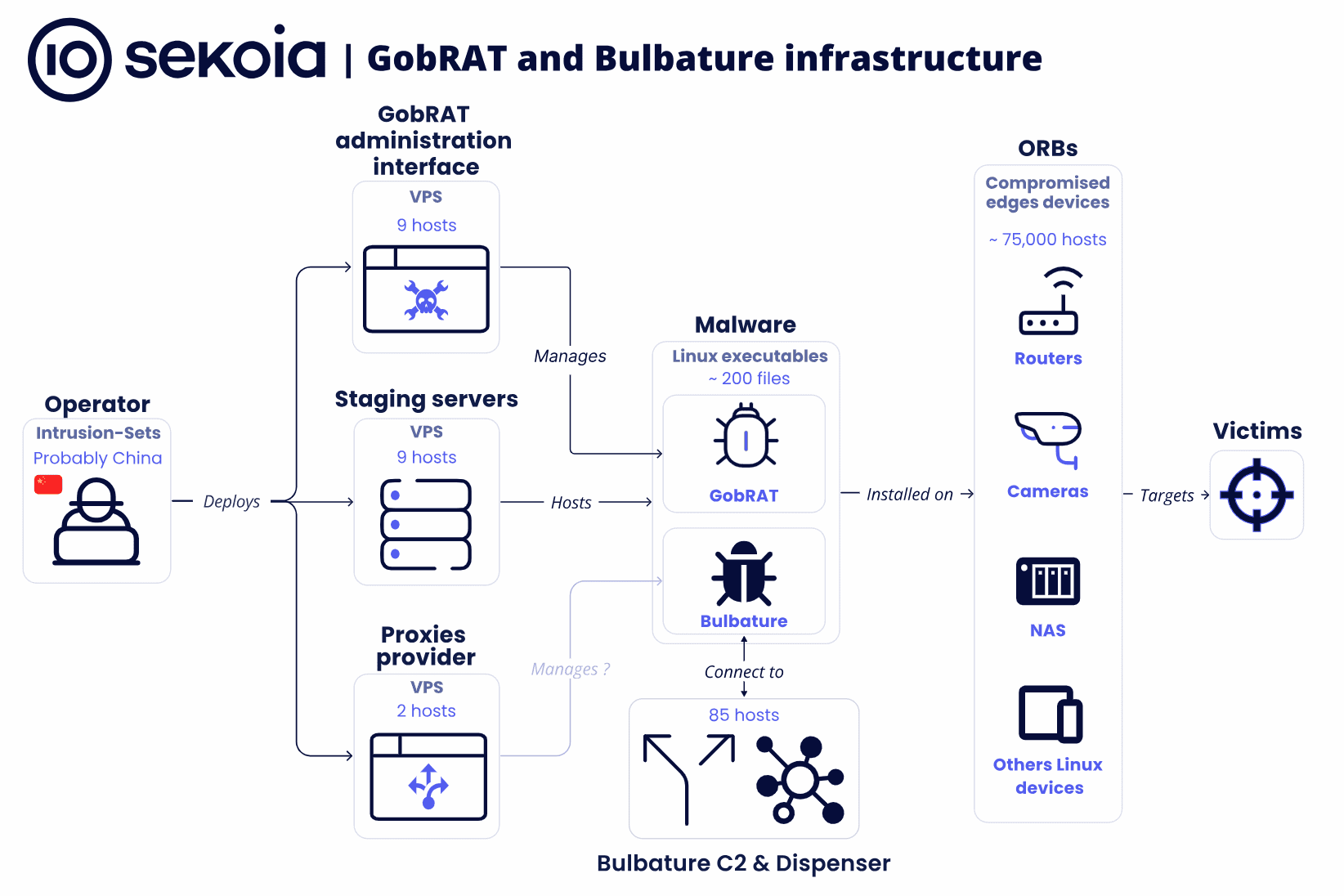
In a comprehensive report released by the Sekoia Threat Detection & Research (TDR) team, a new and intricate cyber threat has surfaced, targeting edge devices globally. The investigation, which began in 2023, delves deep into the workings of two sophisticated malware variants—GobRAT and Bulbature—that have wreaked havoc across critical networks, with a particular focus on infrastructure likely tied to Chinese state-sponsored operations.
The report reveals that since May 2023, a series of cyberattacks have targeted edge devices, transforming them into Operational Relay Boxes (ORB). These devices serve as conduits for a range of offensive cyber operations, from intelligence gathering to orchestrating Distributed Denial-of-Service (DDoS) attacks. The campaign has leveraged staging servers, compromising edge devices and deploying malware, including the already documented GobRAT and a newly uncovered threat known as Bulbature.
GobRAT, a backdoor written in Go, has been the subject of previous investigations by the JPCERT Coordination Center. This malware is a versatile tool, capable of executing a variety of commands, from reverse shell operations to DDoS attacks. GobRAT continues to be deployed in campaigns to gather intelligence and execute attacks from compromised edge devices, functioning as a Swiss-army knife for attackers.
While GobRAT’s capabilities are well-documented, Bulbature is the more enigmatic and potentially more dangerous of the two. First detected by Sekoia, Bulbature transforms compromised devices into ORBs, which are then used to relay attacks against final target networks. With its high level of obfuscation and use of advanced anti-analysis techniques, Bulbature has proven challenging to fully dissect. Despite this, analysts were able to trace its operations, revealing that it connects to Command-and-Control (C2) servers using complex network interactions, making its full behavior difficult to ascertain.
The infrastructure behind this campaign is vast and highly organized, comprising over 75,000 compromised hosts by mid-2023. These hosts span 139 countries, with the United States, Hong Kong, and Sweden being the most affected. The report indicates that these compromised devices are mainly Linux routers and network devices, targeted for their strategic importance in serving as exit nodes for the attacks.
The TDR team also identified a sophisticated proxy provider interface, which allows attackers to create on-demand proxy tunnels using protocols like WireGuard, OpenVPN, and SOCKS5. This dynamic proxy infrastructure enables attackers to rotate proxies frequently, obscuring their tracks and making detection and mitigation significantly more difficult.
While no official attribution has been made, the TDR report notes several indicators suggesting that this campaign may be linked to Chinese state-sponsored threat actors. The use of edge devices as ORBs has been a tactic associated with groups like APT31, and infrastructure related to the attacks has been traced back to Chinese autonomous systems. Furthermore, the victimology, which heavily targets North American and Asian networks, aligns with patterns observed in previous China-affiliated campaigns.





