Image: XLabs
Cybersecurity researchers from XLabs have identified a sophisticated new variant of the Melofee backdoor, a C++ malware targeting Red Hat Enterprise Linux (RHEL) 7.9 systems. Initially exposed by ExaTrack in 2023 and linked to the notorious APT group Winnti, this variant of Melofee employs advanced techniques to maintain persistence, conceal itself, and exfiltrate data, marking a concerning evolution in Linux-targeted malware.
XLabs discovered this new Melofee sample on July 27, 2024, when their Cyber Threat Insight and Analysis System (CTIA) flagged a file from an IP address associated with suspicious activities. The report notes, “This latest variant has notable upgrades,” including an RC4-encrypted kernel driver designed to mask traces of files, processes, and network connections.
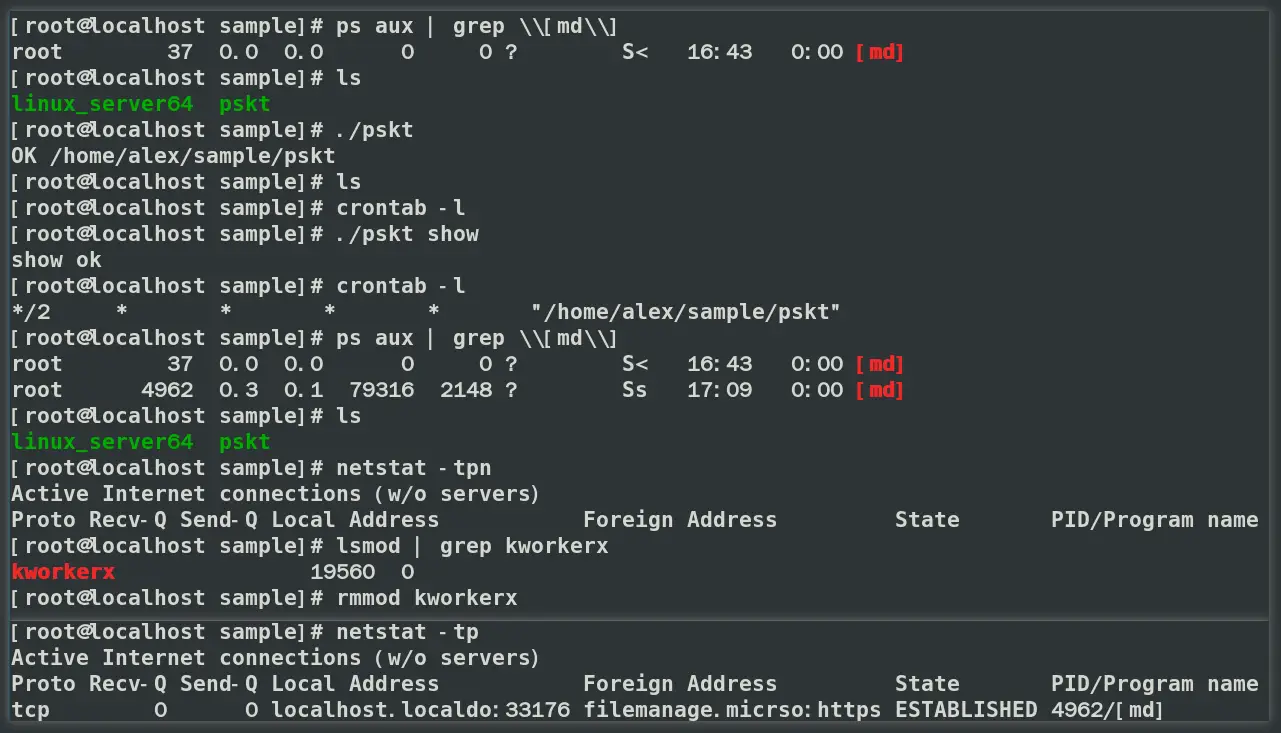
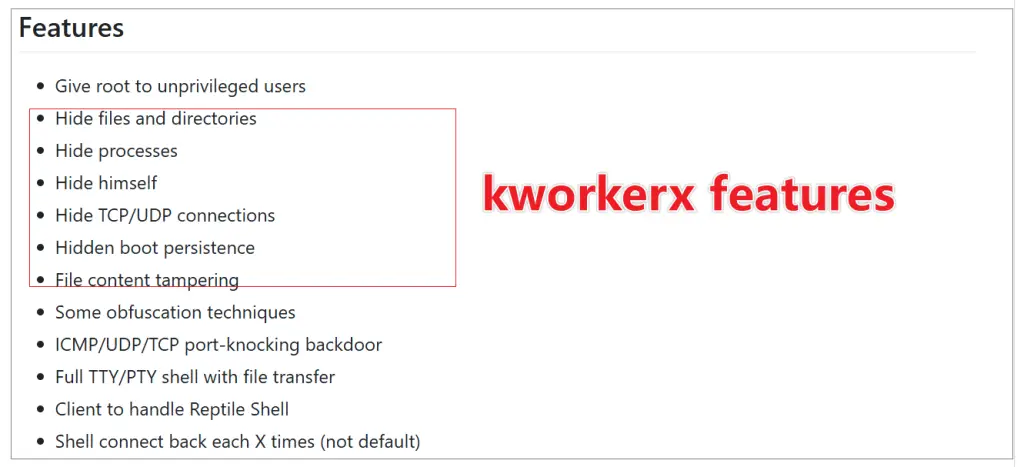
Melofee operates in two primary modes: Infection Mode and Management Mode. When launched without parameters, it enters Infection Mode, installing a kernel driver called kworkerx. This module’s role is to “effectively hide all network traffic on port 443” and to conceal files, processes, and directories by hooking key system functions.
A notable characteristic of this variant is its encrypted command-and-control (C2) configuration, which directs the malware to connect to filemanage.micrsofts-file.com. According to XLabs, this domain’s second-level name is a close imitation of Microsoft’s, likely a deliberate attempt to blend in. However, the association of this C2 address with legitimate domains is likely a result of automatic IP resolutions from domain registrars. “Labeling it as malicious likely constitutes a false positive,” the report explains, adding that this is a common issue for domain parking IPs, which often get misattributed in security contexts.
Melofee’s kworkerx module is a modified version of the open-source project Reptile, known for its backdoor and hiding capabilities. The module uses hooks in system functions like tcp4_seq_show to hide network communications, while other hooks in directory and file management functions ensure complete invisibility on the system. This makes it exceptionally challenging to detect without direct analysis of system internals. XLabs detailed the module’s versatility: “Using the ioctl function with specific parameters enables fine-grained control over its concealment capabilities.”
Once embedded, Melofee allows attackers to issue a wide range of commands to the infected system, including starting a shell, managing files, and launching new processes. “After installing the driver module, Melofee decrypts the C2 configuration and establishes communication, waiting to receive and execute commands,” XLabs revealed, describing the backdoor’s seamless integration with system-level functions.
XLabs warns that network administrators should be vigilant, checking for potential infection signs like the /tmp/lock_tmp1 file and the presence of the kworkerx module.
Related Posts:
- Kiteshield Packer Emerges as a Significant Threat in Linux Malware Landscape
- Two New Variants of the Spectre Vulnerability were found by Security researchers
- Microsoft April Patch Tuesday includes mitigate Spectre Variant 2 for AMD processors