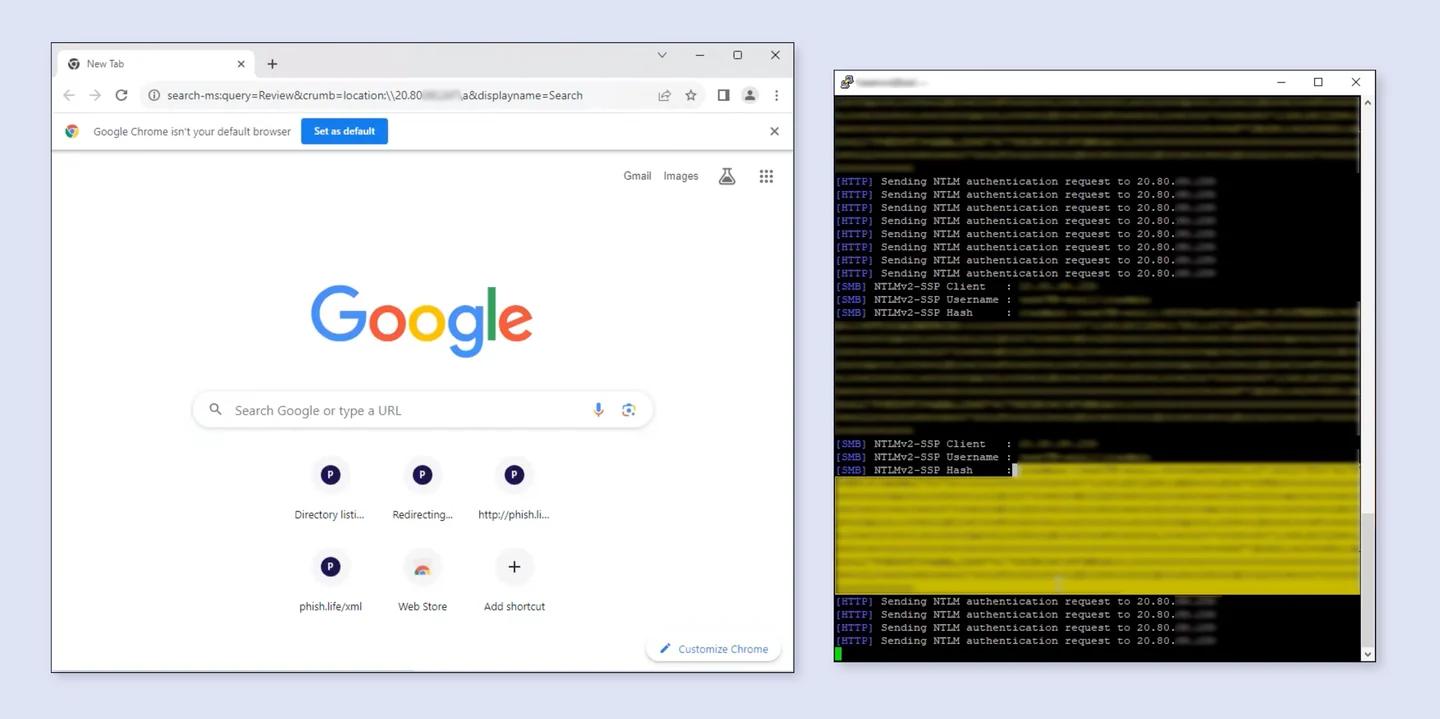
After the victim clicked on the link, the attacker got the victim's hashed passwords.
In a recent discovery, Varonis Threat Labs has unveiled three new ways that cyber attackers can exploit to access NTLM v2 hashed passwords, putting countless systems and user data at risk. Among these vulnerabilities, one stands out as particularly critical: CVE-2023-35636, an Outlook exploit that exposes sensitive information.
Understanding CVE-2023-35636 and NTLM v2
CVE-2023-35636 is a security vulnerability found in Microsoft Outlook, specifically in the calendar sharing function. This exploit enables attackers to intercept NTLM v2 hashes, which are used for authentication in Microsoft Windows systems. NTLM v2, although more secure than its predecessor, is still susceptible to offline brute-force and authentication relay attacks.
How Attackers Exploit NTLM v2 Hashes
Attackers can use NTLM v2 hashes in two primary attack scenarios:
1. Offline Brute-Force Attack: In this type of attack, attackers have access to the NTLM v2 hash and attempt to crack the user’s password by trying various combinations until a match is found. This attack is virtually undetectable as it leaves no network traces.
2. Authentication Relay Attack: In an authentication relay attack, attackers intercept NTLM v2 authentication requests and relay them to a different server, potentially gaining unauthorized access to the victim’s intended server.

Outlook Exploit: How it Works
The Outlook exploit involves adding specific headers to an email, directing Outlook to share content and contact a designated machine. This manipulation creates an opportunity for attackers to intercept NTLM v2 hashes during the authentication process. The exploit requires two headers: “Content-Class” and “x-sharing-config-url,” which point to the attacker’s machine.
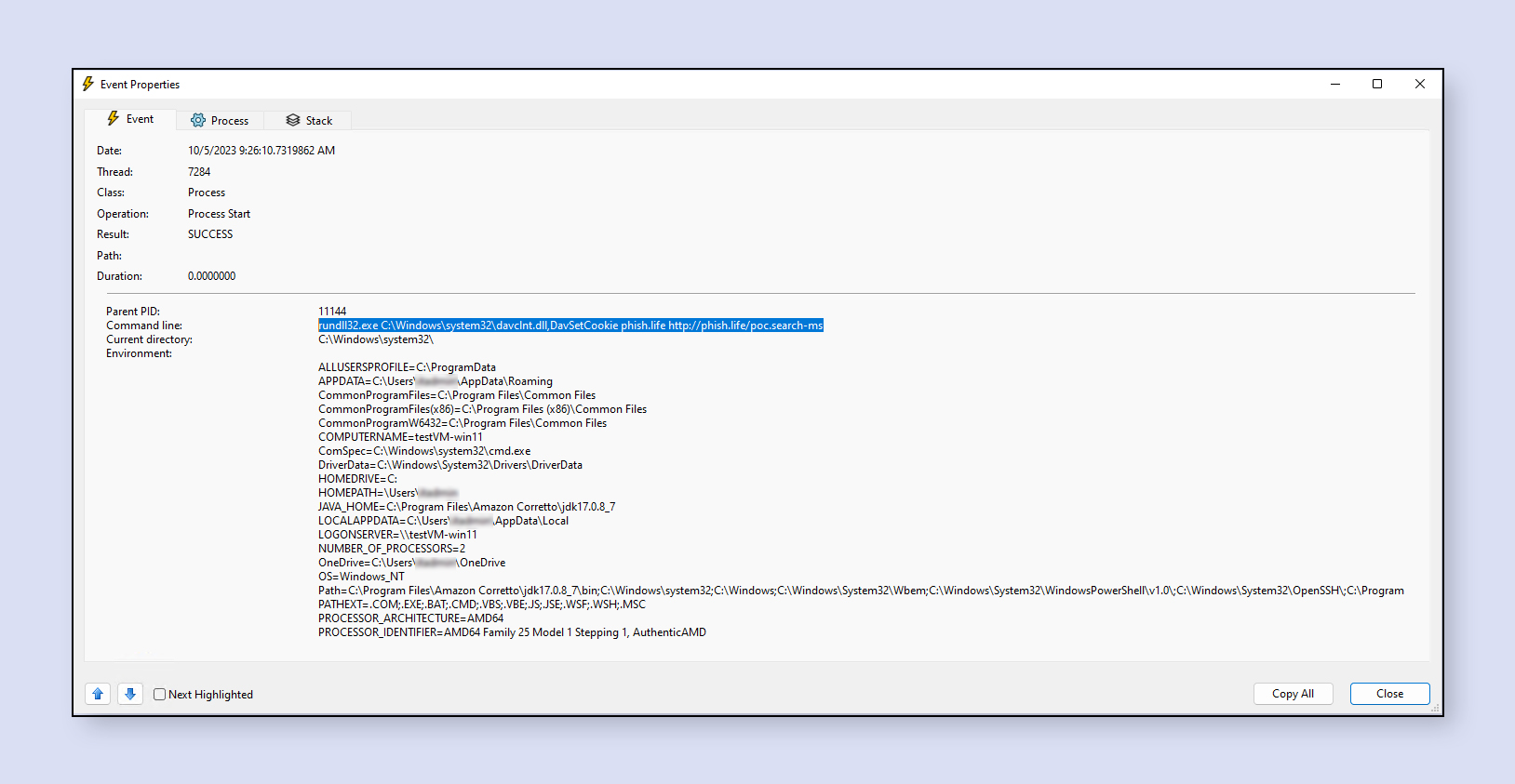
Other Attack Vectors: WPA and Windows File Explorer
Apart from Outlook, attackers can leverage Windows Performance Analyzer (WPA) and Windows File Explorer to gain access to NTLM v2 hashes. By exploiting URI handlers and specific parameters, attackers can trick these applications into revealing sensitive information.
Protecting Against NTLM v2 Attacks
Microsoft has addressed the Outlook vulnerability (CVE-2023-35636) with a patch released on December 12, 2023, categorizing it as “important.” However, the vulnerabilities associated with WPA and Windows File Explorer have been deemed of “moderate severity” by Microsoft.
To safeguard your systems and data from NTLM v2 attacks, consider implementing the following security measures:
1. SMB Signing: Enable SMB signing to protect SMB traffic from tampering and man-in-the-middle attacks. This feature digitally signs all SMB messages, allowing recipients to detect and reject any tampered messages.
2. Block Outgoing NTLM v2: Starting with Windows 11 (build 25951), you can block outgoing NTLM authentication, adding an extra layer of security.
3. Force Kerberos Authentication: Whenever possible, enforce Kerberos authentication and block NTLM v2 at both the network and application levels. This helps prevent the use of NTLM v2 where it is not required.
By taking these precautions, you can significantly reduce the risk of falling victim to NTLM v2 attacks and ensure the safety of your systems and data.