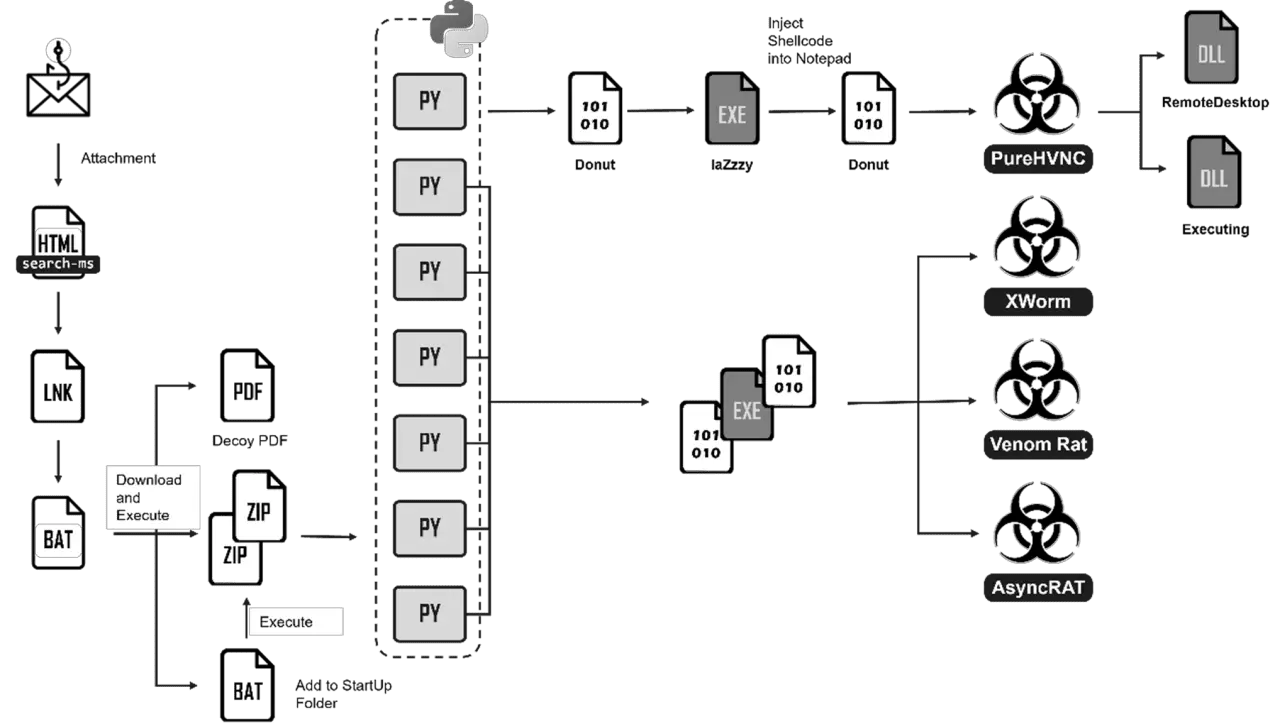
Attack flow | Image: FortiGuard Labs
Cybersecurity researchers from FortiGuard Labs have discovered a sophisticated phishing campaign that utilizes a multi-stage execution flow and various evasion techniques to deliver multiple strains of malware, including the remote access trojan (RAT) PureHVNC. This campaign specifically targets employees, luring them with a seemingly urgent email from a customer that contains a malicious HTML attachment.
The phishing campaign initiates with a carefully crafted email that masquerades as a service inquiry from a customer. The email uses urgent language to manipulate recipients into opening a malicious HTML attachment, setting off a chain of events that leads to the deployment of several potent malware variants.
The campaign’s entry point is an HTML file attached to the phishing email. When opened, the file exploits the “search-ms” functionality to query a malicious LNK file on remote file shares. Disguised as a harmless PDF icon in Windows Explorer, this LNK file contains a command that runs a remote batch file using conhost.exe as the parent process—an evasion technique designed to avoid detection by leveraging a legitimate Windows process.
The batch file, named new.bat, is heavily obfuscated to evade detection. Using a combination of encoding tricks and string obfuscation, the script appears to be in UTF-16 encoding with Chinese characters, further complicating analysis. The script begins by opening a decoy PDF file while silently downloading two ZIP files via PowerShell. These ZIP files contain the Python environment and a series of malicious Python programs, which are extracted and hidden in the user’s profile directory.
The final stage involves running the Python programs in sequence, each one loading and executing shellcode designed to bypass detection mechanisms and deploy the main payload—PureHVNC.
Each Python file in the campaign is meticulously obfuscated using a Python obfuscator named “Kramer,” available on GitHub. Kramer encrypts the source code with a randomly generated key, adding an additional layer of protection against reverse engineering. The shellcode, generated by a tool called “donut,” is designed to decrypt and execute the next stage payload while bypassing Windows security features like AMSI and WLDP.
The second stage of the attack introduces the shellcode loader, “laZzzy,” which disguises itself as a legitimate Microsoft Management Console (MMC) application. This loader uses advanced injection techniques to execute the final payload within notepad.exe, a benign-looking process, thereby avoiding detection.
Among the malware deployed in this campaign, PureHVNC stands out for its sophisticated capabilities. As a .NET application, PureHVNC is heavily obfuscated using the .NET Reactor, making it difficult to analyze. Its primary function is to decrypt its payload using AES encryption and then decompress it with Gzip, extracting and loading a DLL payload into memory.
Once activated, PureHVNC initiates a series of actions aimed at maintaining persistence and gathering intelligence. It sets a registry run key using PowerShell or prevents the system from sleeping, ensuring that the malware remains active. It then communicates with a Command and Control (C2) server to report system information, including details about installed antivirus products, system specifications, and user information.
PureHVNC specifically targets high-value assets, such as cryptocurrency wallets, password managers, and two-factor authentication (2FA) applications. It scans for paths associated with these applications and checks the registry for installed software, focusing its efforts on stealing sensitive data.
The attack doesn’t stop with PureHVNC. The C2 server can deliver additional plugins that extend the malware’s capabilities. Two notable plugins identified in this campaign are:
- Plugin 1: PluginRemoteDesktop
This plugin enables remote control of the victim’s system. It communicates with the C2 server to execute commands that allow the attacker to manipulate the victim’s desktop environment, capturing screenshots, controlling the mouse, and more.
- Plugin 2: PluginExecuting
PluginExecuting is designed for executing additional files, updating the malware, or even uninstalling it to cover tracks. It supports several commands, including those for downloading and executing new malware, using process hollowing to inject malicious code into legitimate processes.
Organizations are urged to remain vigilant against such threats, ensuring that employees are educated about the dangers of phishing emails and that robust security measures are in place to detect and mitigate multi-stage attacks. As this campaign demonstrates, even the most seemingly innocuous email can be the starting point for a devastating breach.
For more detailed information, the full report is available on FortiGuard Labs’ website.
Related Posts:
- Beware the Windows Search Scam: Clever Phishing Campaign Exploits User Trust
- Google Gmail adds new security feature to prevent phishing attacks
- Beware of “How to Fix” Button: New Phishing Emails Trick Users into Executing Malicious Commands