Image: Wiz Threat Research
A newly discovered phishing campaign is targeting AWS accounts, according to a warning from security researchers at Wiz. The campaign involves deceptive emails leading users to a convincingly crafted fake AWS login page.
Recently, a Wiz Threat Research employee received a phishing email in their personal inbox. The email, designed to lure the recipient into revealing their AWS login credentials, was immediately recognized as a phishing attempt, prompting an internal investigation. While this particular instance was not believed to be a targeted attack or spearphishing, it nonetheless provided valuable insights into the methods being used by cybercriminals.
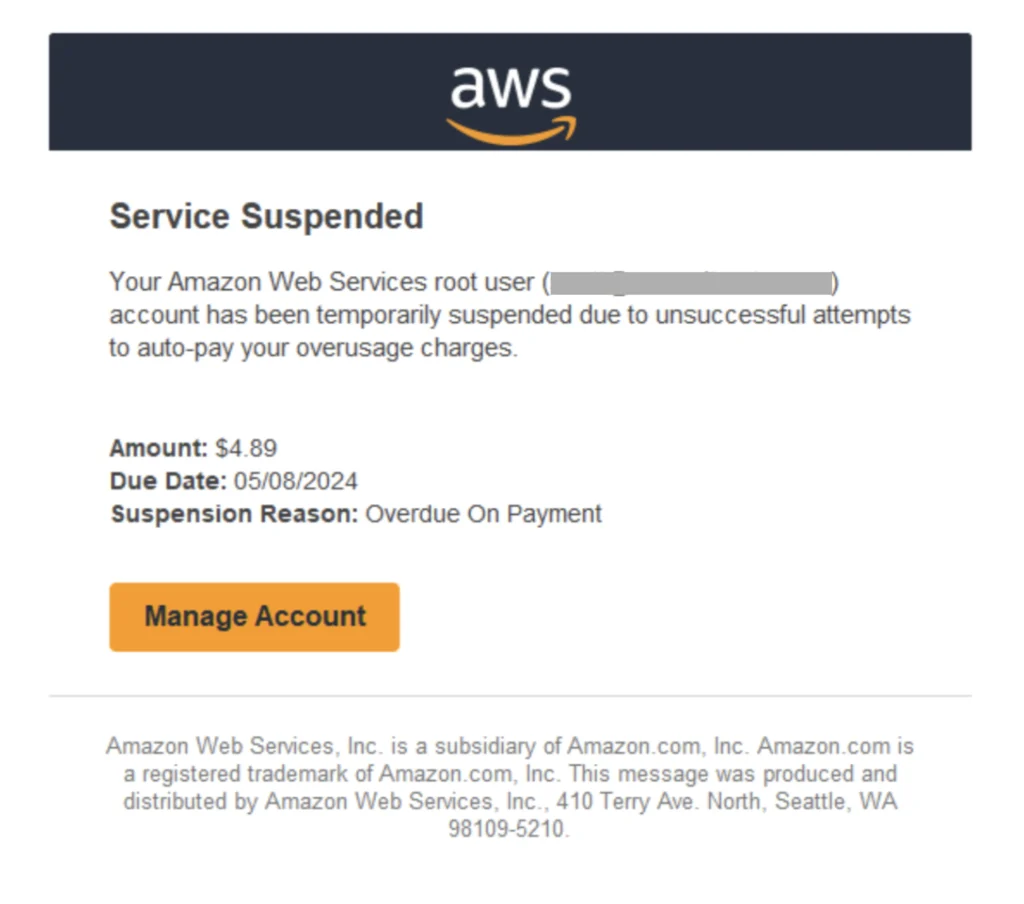
The phishing email was notably sparse, containing only a PNG image that, when clicked, redirected the user to a series of web pages ultimately leading to a fake AWS login page. The initial link, hosted on Squarespace, directed users through multiple redirects before landing on a credential harvesting page—a visual clone of the legitimate AWS sign-in page. The attackers went to great lengths to mimic the genuine AWS login experience, even crafting a URL designed to closely resemble the real AWS sign-in page.
The phishing email originated from the address admin@alchemistdigital[.]ae, a domain already flagged in open-source threat intelligence as associated with malware distribution. Interestingly, the email was sent using Amazon SES (Simple Email Service), suggesting that the attackers either owned or had compromised an AWS account to facilitate the phishing campaign.
Once redirected to the fake login page, victims were prompted to enter their AWS credentials. However, in a curious twist, the phishing page would return a 400 error unless the email address entered matched that of the original recipient. This suggests a level of customization in the attack, possibly indicating that the threat actors were attempting to fine-tune their phishing campaign to target specific individuals.
The fake login page also loaded a JavaScript file from a CloudFront distribution, further indicating that the attackers were leveraging AWS infrastructure in their phishing attempts. The use of AWS services in this manner is particularly concerning, as it not only exploits the trust users place in AWS but also makes the attack more difficult to detect.
During the investigation, Wiz Threat Research attempted to interact with the phishing infrastructure using a honeypot environment. However, before they could fully explore the attacker’s intent, the phishing page was taken down. It remains unclear what prompted the sudden takedown, but it is possible that AWS or Google, both of which had been alerted to the phishing activity, were involved in shutting down the malicious infrastructure.
The investigation revealed that the phishing domain (consoleportal[.]tech) resolved to CloudFlare and had previously resolved to IP addresses associated with Namecheap and Hostinger. Further analysis uncovered additional domains likely involved in AWS phishing campaigns, including officequalcomm[.]com, webportal[.]tech, and docshare[.]tech. These domains followed a similar subdomain format, such as signin.aws.{domain} or console.aws.{domain}, indicating a broader network of phishing sites designed to deceive AWS users.
Moreover, using domain lookalike search tools, Wiz Threat Research identified several other domains mimicking Amazon’s login page. While these domains are not definitively linked to the same threat actor, they are highly likely to be used in similar phishing campaigns, emphasizing the need for heightened vigilance among AWS users.
Related Posts:
- No Deal: Wiz Rejects Google, Sets Sights on IPO
- Alphabet to Acquire Cybersecurity Powerhouse Wiz for $23 Billion
- Microsoft AI researchers accidentally leaked up to 38TB of data: including secrets, private keys, passwords
- Researchers Detail Critical Vulnerability in AI-as-a-Service Provider Replicate