PWA phishing flow | Image: ESET
A recent report from ESET reveals a sophisticated series of phishing campaigns targeting mobile banking users across Czechia and beyond. These campaigns leverage the cross-platform capabilities of Progressive Web Applications (PWAs) and WebAPK technology to deceive victims into installing malicious apps on their smartphones, bypassing traditional security warnings.
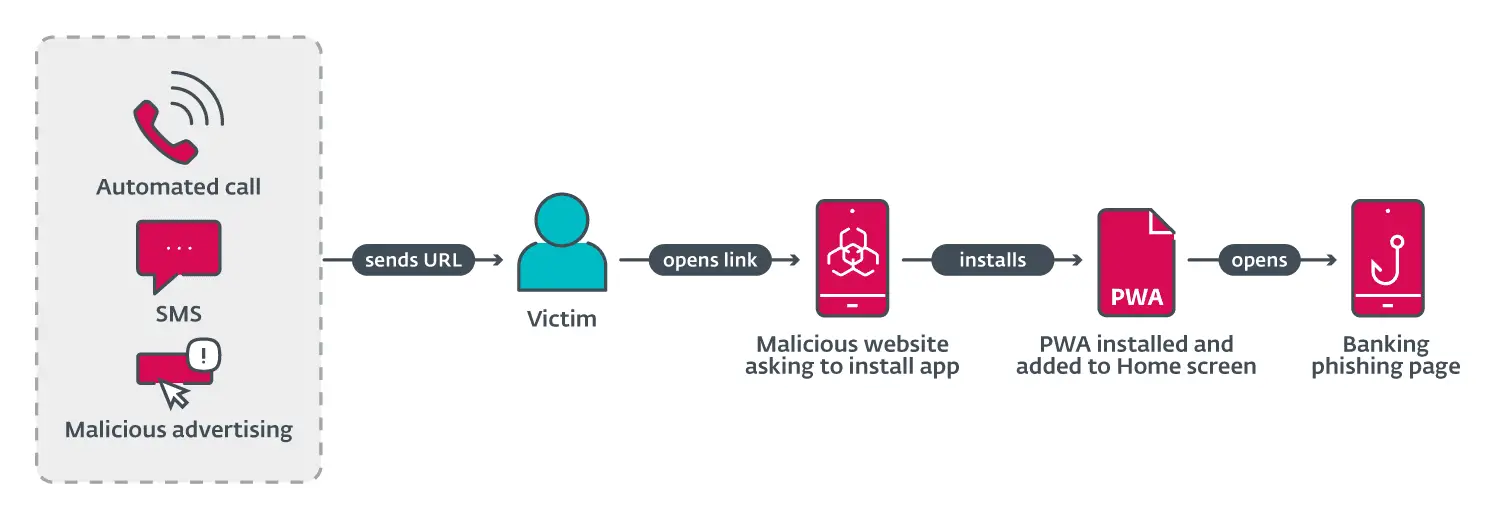
ESET’s analysis uncovered that the phishing campaigns utilized three primary methods to deliver malicious URLs to potential victims: automated voice calls, SMS messages, and malvertising on social media platforms like Facebook and Instagram. Each method was carefully crafted to appear legitimate, luring users into downloading fake banking applications.
- Automated Voice Calls: Victims received a call warning them about an out-of-date banking app, prompting them to select an option that triggered an SMS containing a phishing link.
- SMS Messages: These were sent indiscriminately to Czech phone numbers, containing a link that led to a fake Google Play store page.
- Malvertising: Threat actors registered ads on Meta platforms, enticing users to download a “critical update” or claim a limited-time offer by installing a new version of their banking app.

Once a victim clicked on the phishing link, they were redirected to a convincing imitation of the Google Play store page or a copycat website of the targeted banking application. Android users were prompted to install a WebAPK, a type of application generated by Chrome that closely resembles a native app, without triggering warnings about installing from untrusted sources. iOS users, meanwhile, were instructed through a fake pop-up to add a PWA to their home screen, again bypassing typical security prompts.
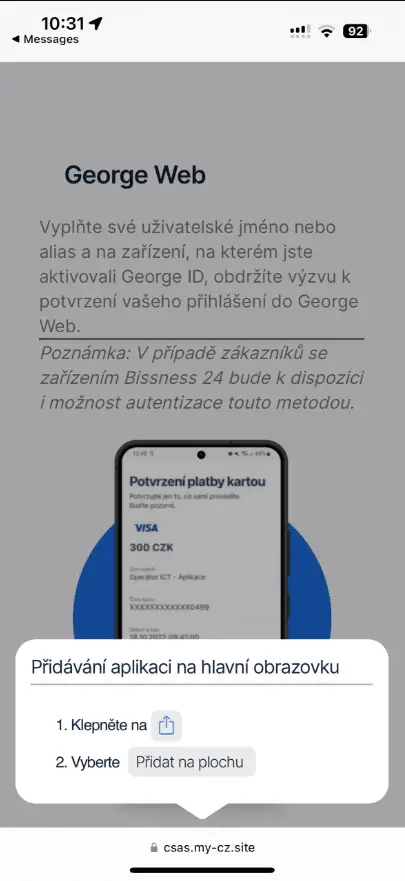
These malicious apps, once installed, displayed a phishing login page, capturing the user’s internet banking credentials. This sensitive information was then transmitted to the attackers’ command and control (C&C) servers.
ESET’s investigation revealed that two distinct groups were behind these phishing operations, each using different C&C infrastructures. One group relied on a Telegram bot to log stolen credentials into a private Telegram group chat, while the other operated through a traditional C&C server with an administrative panel. The latter group continued their activities even after initial takedowns, quickly setting up new domains and preparing additional phishing campaigns.
ESET has alerted the affected banks and coordinated the takedown of multiple phishing domains and C&C servers. However, the researchers warn that these campaigns are likely to continue evolving, with more copycat applications expected to emerge in the near future.
Related Posts:
- New Phishing Technique Exploits Progressive Web Apps for Credible Attacks
- Massive Android SMS Stealer Campaign Uncovered: Over 100,000 Malicious Apps Targeting Global Users
- Decoding the Web Injection Malware Campaign of 2023