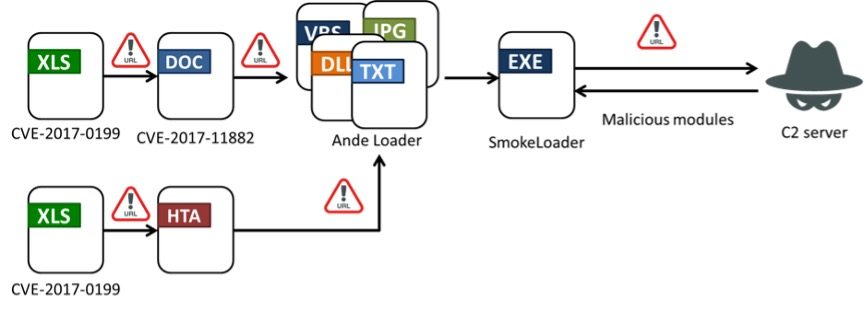
Attack flow | Image: FortiGuard Labs
A recent report by FortiGuard Labs has highlighted a targeted cyberattack involving the infamous SmokeLoader malware. This campaign, observed in September 2024, aimed at several industries in Taiwan, including manufacturing, healthcare, and IT. Known for its adaptability and advanced evasion tactics, SmokeLoader operated not just as a downloader but as an active agent, leveraging plugins to deliver multi-layered attacks.
The attack began with carefully crafted phishing emails. These messages, appearing legitimate, used local language nuances to enhance credibility. Each email carried an attachment disguised as a quotation but contained malicious code. Interestingly, these emails were sent to multiple recipients without altering the recipient’s name, a practice FortiGuard Labs noted as a recurring pattern in this campaign. The design of the email, including inconsistencies in font and color, hinted at copied content, signaling a hasty attempt to deceive.
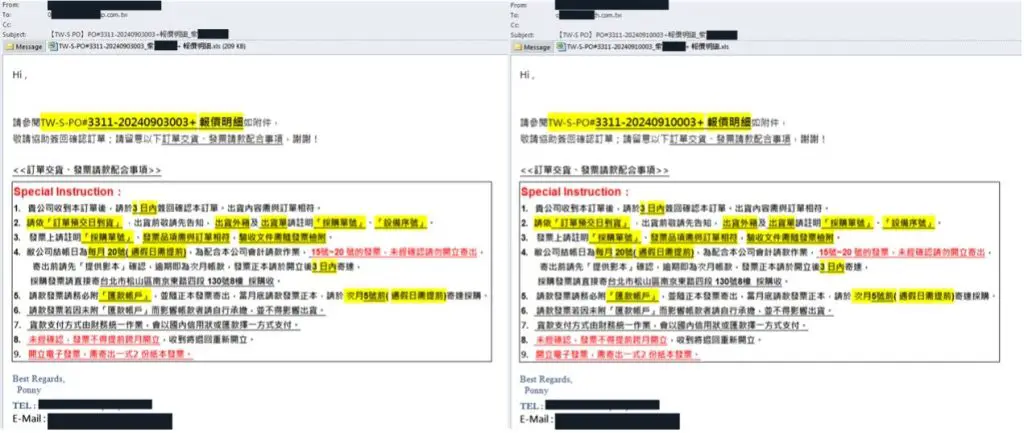
“While this email is persuasive, as it uses native words and phrases, these phishing emails are sent to multiple recipients with almost the same content,” FortiGuard Labs reported.
SmokeLoader exploited two known vulnerabilities: CVE-2017-0199 and CVE-2017-11882. The former, an Object Linking and Embedding (OLE) vulnerability in Microsoft Office, allowed the automatic execution of malicious documents. The latter exploited a flaw in the equation editor of Office, enabling the deployment of shellcode for further stages of the attack.
“After the decryption, the shellcode gets the necessary APIs and downloads the VBS file for the next stage,” the report detailed.
The attack chain utilized AndeLoader as an intermediary malware loader. This loader executed scripts with obfuscated PowerShell code that downloaded steganographic images containing base64-encoded injector data. Once decoded, this data facilitated SmokeLoader’s operation. SmokeLoader then employed its modular plugins for credential theft, process injection, and keylogging.
SmokeLoader’s C2 server delivered nine distinct plugins, including:
- Credential Stealers for browsers, FTP clients, and email software.
- Hooks for Keylogging via user32.dll to capture clipboard content and keystrokes.
- Cookie Clearing Modules forcing users to re-enter credentials, enabling data interception.
Each plugin’s architecture, whether 32-bit or 64-bit, demonstrated a high level of sophistication, making SmokeLoader an adaptable threat.
“This shows the flexibility of SmokeLoader and emphasizes that analysts need to be careful even when looking at well-known malware like this,” FortiGuard Labs concluded.
Organizations are urged to remain vigilant, patch known vulnerabilities, and educate employees about phishing tactics.
Related Posts:
- Sophisticated SmokeLoader Campaign Targets Ukrainian Sectors
- Financially Motivated Hackers UAC-0006 Resurface with New Attacks Targeting Ukraine
- Microsoft Warns of Sophisticated Identity Phishing Campaigns Misusing File Hosting Services
- New Agent Tesla Spyware Variant was spread via Microsoft Word documents