
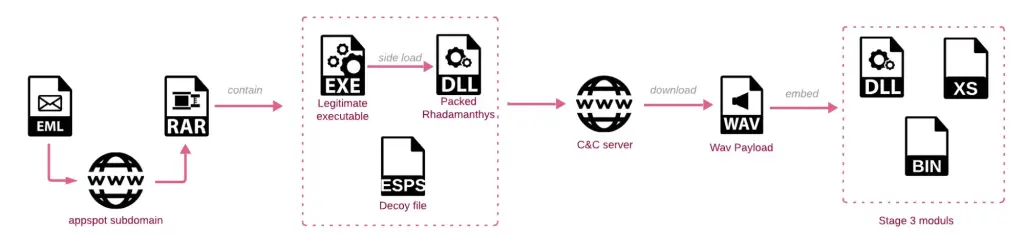
Check Point Research recently uncovered a large-scale phishing campaign exploiting a new version of the Rhadamanthys Stealer, dubbed “Rhadamanthys.07.” This sophisticated malware, designed to extract sensitive data from infected devices, is distributed through phishing emails masquerading as copyright infringement notices. The campaign demonstrates a vast reach, impacting targets across the U.S., Europe, the Middle East, East Asia, and South America.
The attackers behind this campaign send spear-phishing emails from fake Gmail accounts, claiming to represent well-known companies. Victims receive accusations of “copyright violations” on their personal Facebook pages, with emails alleging brand misuse and requesting content removal. These emails, tailored in language and tone, prompt victims to download a file supposedly containing removal instructions, but in reality, it triggers an infection of Rhadamanthys.07.
Check Point Research explains, “The attackers masquerade as various legitimate companies, alleging that victims have committed copyright infringements on their personal Facebook pages.” The emails are often convincingly crafted, though some localization mistakes were noted—such as an email to an Israeli recipient mistakenly written in Korean.
The latest version of the Rhadamanthys stealer includes supposed AI capabilities, though Check Point notes, “the malware does not use modern AI engines but much older classic machine learning, typical for OCR (optical character recognition) software.” Automated tools and potentially AI enhancements are likely used to generate phishing content and handle the high volume of emails required for the campaign.
The campaign predominantly targets high-profile sectors, with nearly 70% of phishing attempts aimed at entertainment, media, technology, and software organizations. According to Check Point, “these high-profile sectors also have frequent copyright-related communications, making such phishing attempts appear more credible.”
Unlike previous versions of Rhadamanthys linked to nation-state actors, this campaign appears to be financially motivated. Check Point analysts concluded, “several factors support this conclusion: the campaign’s broad scope and the use of malware from underground forums point to financial gain as the primary motive rather than espionage or political influence.” The use of Rhadamanthys.07 by non-state actors, combined with the campaign’s indiscriminate targeting, suggests the primary goal is financial gain.
Related Posts:
- Threat Actor Deploys LummaC2 and Rhadamanthys Stealers in Attacks on Taiwanese Facebook Accounts
- Rhadamanthys Evolves: AI-Powered Crypto Theft with Version 0.7.0
- Rhadamanthys Stealer: MaaS Malware Hits Oil & Gas
- New Cyber Threat: RHADAMANTHYS Infostealer Targets Israel
- Hackers Target System Admins with Fake PuTTY Website, Deploy Rhadamanthys Stealer