New SilentCryptoMiner Campaign Abuses SIEM Agent in Cryptocurrency Mining Attacks

Kaspersky Labs has uncovered a sophisticated cyberattack campaign that abuses an open-source Security Information and Event Management (SIEM) agent to deploy SilentCryptoMiner, a stealthy cryptocurrency mining malware. This campaign, which began in 2022, illustrates the increasingly complex techniques being used by attackers to evade detection and persist on infected systems.
The primary target of this campaign appears to be Russian-speaking users, with 87.63% of affected victims located in Russia, followed by countries like Belarus, India, and Uzbekistan. The attackers are spreading the malware through multiple channels, including websites offering free downloads of popular software like uTorrent, Minecraft, and Microsoft Office, as well as Telegram channels aimed at cryptocurrency investors and YouTube videos promoting cheats.
What sets this campaign apart is the use of unconventional techniques to evade detection. According to Kaspersky, “attackers are using quite unusual techniques,” including the exploitation of the open-source Wazuh SIEM agent. This agent, commonly used for security monitoring, is being repurposed as a backdoor, allowing attackers to gain remote access to infected systems.
Kaspersky’s report reveals that the attackers lure victims with malicious websites that appear in Yandex search results when users look for free software. Once on the site, users are prompted to download a ZIP file containing a malicious MSI installer. Upon execution, the installer triggers a multi-stage infection chain, ultimately leading to the installation of SilentCryptoMiner.
The malware itself is cleverly hidden. After execution, the attackers leverage legitimate software components, such as AutoIt and dynamic libraries with valid digital signatures, to bypass security checks. Kaspersky notes that “the malicious payload is an A3X script which was compiled into an EXE file and injected right inside the second DLL file signature.” This ensures that the file appears legitimate, making it nearly impossible to detect without deep file analysis.
Once installed, the miner uses the victim’s system resources to mine anonymous cryptocurrencies like Monero and Zephyr. The mining configuration, stored in the SilentCryptoMiner, is designed to stealthily generate profit for the attackers while avoiding detection by common security tools.
Although most of the victims are Russian-speaking, the campaign has a global reach, with users in countries such as Germany, Kazakhstan, and Algeria also affected. The miners are capable of more than just mining cryptocurrency—some variants of the malware can also replace cryptocurrency wallet addresses in the victim’s clipboard or take screenshots, amplifying the potential damage.
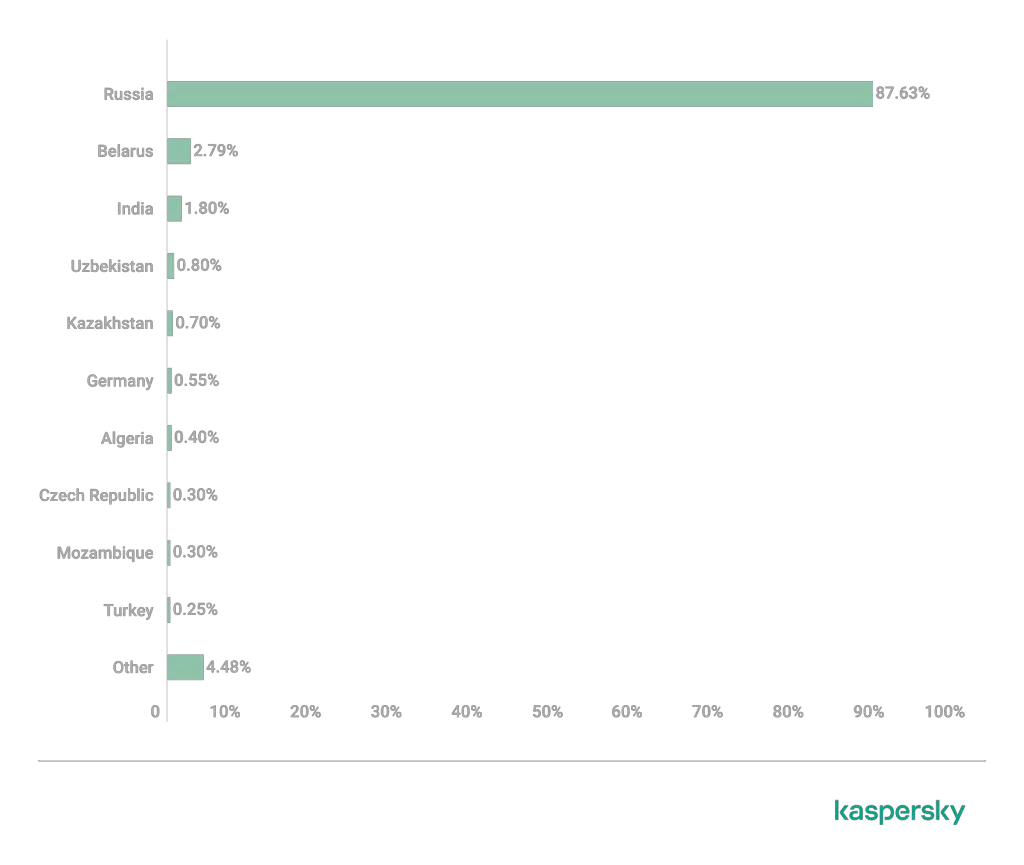
TOP 10 countries where users were affected by the described infection chain, June — August 2024
Kaspersky also warns of the dangers of downloading software from untrusted sources, stating that “this audience makes an easy target for the attackers because they are open to installing unofficial software from obscure sources and disabling security measures.”





