
The npm ecosystem has been infiltrated once more by the persistent Skuld infostealer, a notorious malware strain targeting developers with deceptive packages. Socket’s threat research team unveiled this campaign, led by the threat actor “k303903,” which posed significant risks to both individual developers and organizations.
The attack leveraged npm packages disguised as legitimate tools, including windows-confirm, windows-version-check, downloadsolara, and solara-config. These packages were downloaded over 600 times before their removal, compromising numerous development machines. This demonstrates “how even low-complexity attacks can rapidly gain traction,” the report highlights.
Socket researchers noted a recurring pattern of obfuscation, typosquatting, and reliance on commodity malware, echoing a similar attack on Roblox developers just a month earlier. “The return of the Skuld infostealer to npm highlights a recurring pattern: attackers gain a foothold, achieve brief success, and swiftly adapt by reintroducing the threat with new packaging and distribution strategies,” the report states.
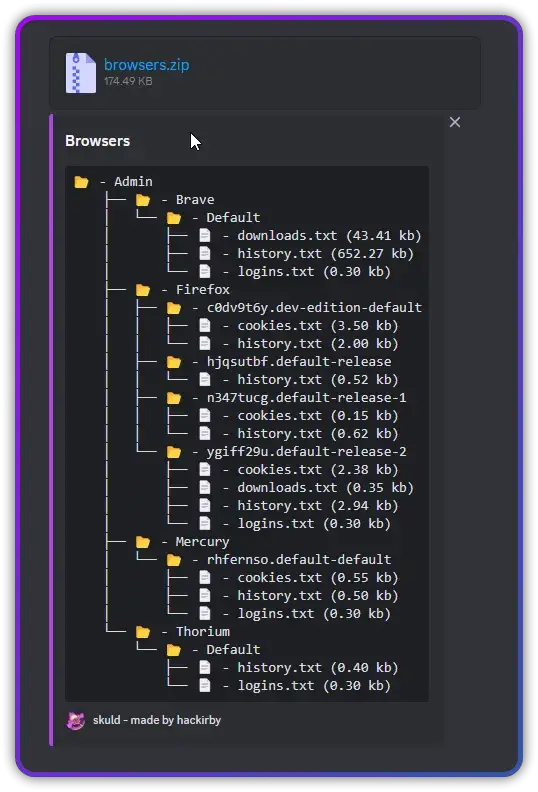
The threat actor utilized Obfuscator.io to obscure the malicious code and evade detection. A payload hosted on URLs designed to appear legitimate (including domains impersonating Cloudflare) was silently executed upon installation. Additionally, the attack used Discord webhooks for data exfiltration, blending into legitimate communication and testing environments.
This campaign exemplifies how threat actors exploit trusted supply chains to distribute malware. By masquerading as productivity and development tools, the attackers deceived developers into unknowingly executing malicious code.
The npm registry acted swiftly, removing the malicious packages within days. However, the impact on affected users remains significant. “Credentials, tokens, and other sensitive data were likely stolen, jeopardizing both individual developers and organizational networks,” the report warns. Even short-lived campaigns like this one can have long-term consequences, as compromised credentials may be exploited well after the attack ends.
Related Posts:
- Roblox Developers Targeted in Supply Chain Attack with Malicious npm Packages
- Roblox Cheaters Targeted: Skuld Stealer and Blank Grabber Malware Lurks in PyPI Packages
- Infostealers Overcome Chrome’s App-Bound Encryption, Threatening User Data Security